10 Essential Steps for Protecting Your Dynamics 365 Infrastructure
Securing your Dynamics 365 infrastructure keeps your business safe from real dangers. Last year, seventy-four percent of companies had at least one time when private business data was leaked.
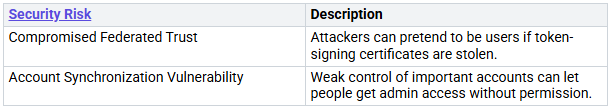
You face risks like:
Many companies have trouble with role-based access that does not fit what the industry needs. As you read, look at what you do now and find plac…