9 Key Azure Security Tools for Stronger Cloud Protection
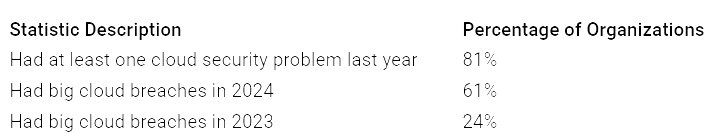
Cloud environments have more threats now. Reports say 81% of groups had at least one cloud security problem last year:
You need to stop problems like people getting in without permission, stolen data, and wrong settings. To make Azure Security better, use these nine important tools:
Microsoft Entra ID
Microsoft Defender for Cloud
Microsoft Sentinel
Azure Key…