Delegated Permission Challenges Simplified for Everyday Users
Delegated permission allows applications to act on your behalf while respecting your existing access rights. It plays a vital role in automating tasks like sending emails or managing files in tools like Microsoft Graph and Power Automate. However, implementing it can be challenging. You need to navigate multiple layers of Azure AD and Microsoft Graph API permissions, which can feel overwhelming. Managing OAuth tokens and ensuring proper access levels often complicates workflows further. Without careful oversight, over-privileged access or misconfigurations may expose sensitive data or disrupt automation processes.
Key Takeaways
Delegated permissions let apps work for you safely. They follow your access rules and help with tasks like sending emails.
Give users only the permissions they need to do their job. This keeps data safe and lowers security risks.
Check permissions often to find old or extra access. This keeps things secure and follows company rules.
Work with IT teams to handle permissions well. Talking clearly helps keep access controls organized and improves safety.
Learn about permission updates and changes. Use tools to watch and manage permissions, so you stay in charge of your tasks.
Understanding Delegated Permission
What Delegated Permission Means
Delegated permission allows an application to perform actions on your behalf while respecting your existing access rights. This concept is central to modern applications, where secure and verifiable delegation mechanisms are essential. For example, when you use a calendar app to schedule meetings, the app accesses your calendar data using delegated permissions. It acts as you, but only within the limits of the permissions you’ve granted.
The OAuth Security Model for Delegated Authorization explains how a party can delegate part of its authorization to another party without sharing credentials. This ensures secure access while maintaining control over sensitive data.
Delegated permissions are particularly useful in scenarios where applications need to interact with multiple services or tools. For instance, AI systems often rely on authenticated delegation to perform tasks requiring access to various resources. This trend highlights the growing importance of delegated permissions in enhancing the functionality of modern applications.
How Delegated Permission Works in Microsoft Graph and Power Automate
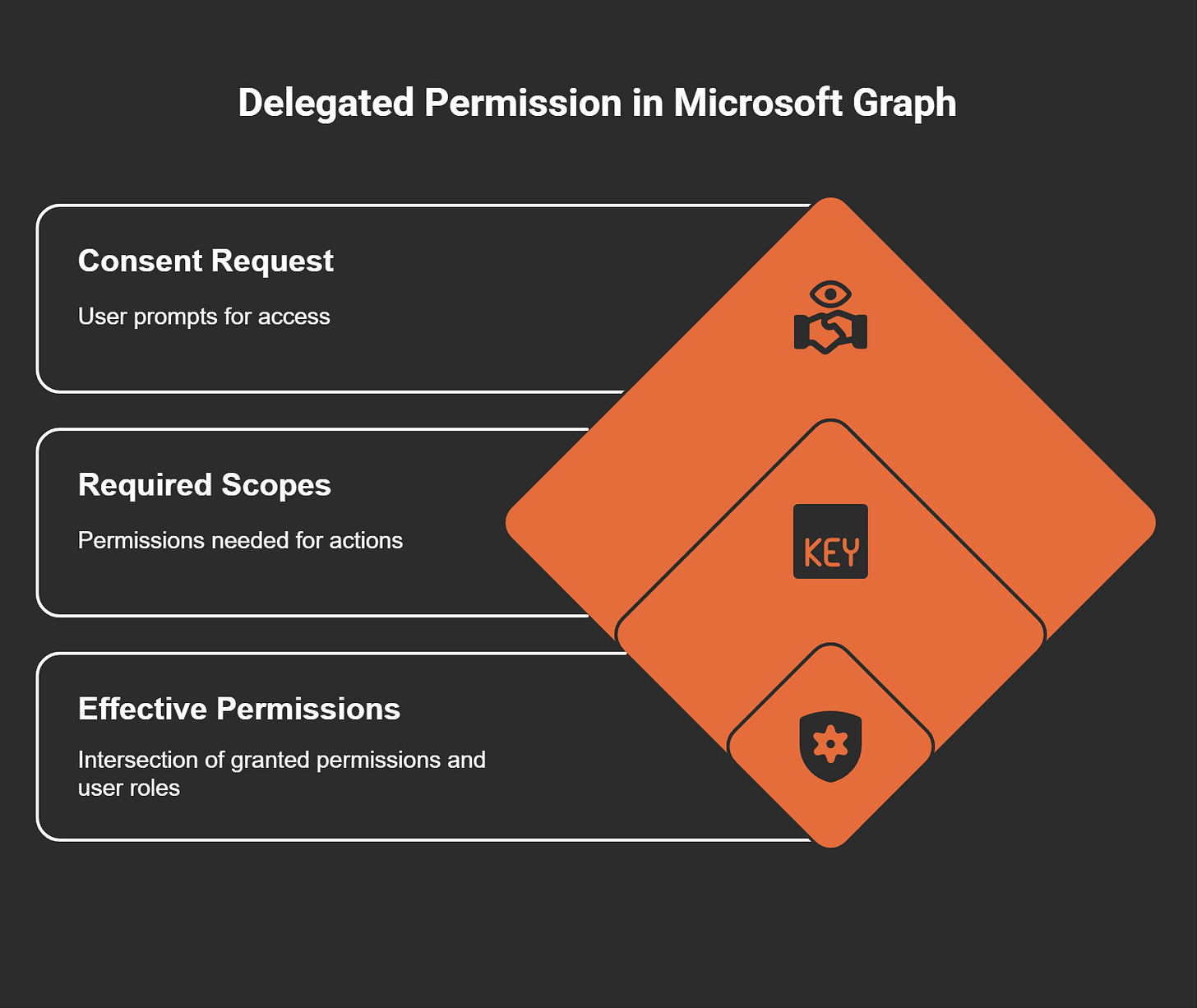
In Microsoft Graph and Power Automate, delegated permissions enable applications to access resources on behalf of a signed-in user. This functionality is crucial for automating tasks like sending emails, managing files, or updating calendars. Here’s how it works:
Required Scopes: When an application connects to Microsoft Graph, it specifies the permissions it needs in the Scopes parameter. These scopes define what the application can do.
Consent Request: If the application doesn’t already have consent for the requested permissions, you’ll be prompted to grant access. This ensures that you remain in control of what the application can access.
Effective Permissions: The actual permissions depend on the intersection of the granted delegated permissions and your user role. For example, an admin user may have broader access than a non-admin user.
This layered approach ensures that delegated permissions align with your role and the tasks you need to perform.
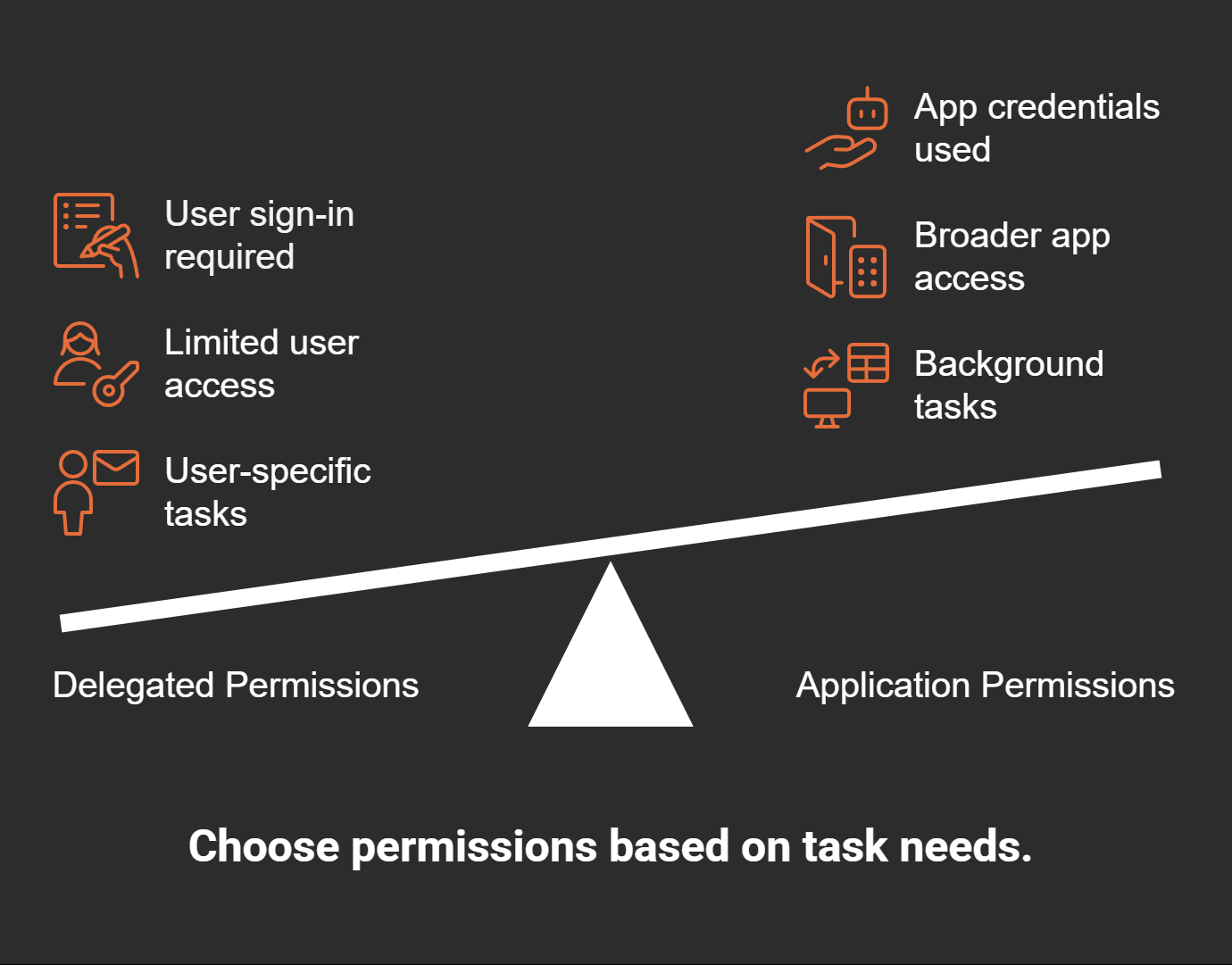
Key Differences Between Delegated and Application Permissions
Delegated and application permissions serve different purposes, even though both control access to resources. Understanding their differences helps you choose the right type for your needs:
Delegated permissions are ideal when tasks require user-specific context. For example, sending an email as a user requires delegated permissions. On the other hand, application permissions are better for system-level tasks that don’t involve a specific user.
The XACML 3.0 specification provides a framework for expressing delegation policies, helping you understand how to manage permissions effectively.
By understanding these differences, you can ensure that your applications use the appropriate permissions for their tasks.
Challenges of Delegated Permission
Security Risks and Overexposure
Delegated permissions can introduce security risks if not managed properly. When applications act on your behalf, they inherit your access rights, which may lead to overexposure of sensitive data. For example, if an application has delegated permissions to access your files, it could inadvertently expose confidential information if permissions are misconfigured.
To mitigate these risks, you should focus on monitoring and auditing activities. Regularly checking logs for unusual patterns, such as spikes in account lockouts or logon failures, can help you identify potential threats. Here are some best practices to enhance security:
Use descriptive names for security groups to avoid confusion and prevent unauthorized access.
Implement strong password policies to reduce the risk of compromised credentials.
Review audit logs to track login failures and authentication issues.
Tip: Always monitor suspicious activities in your environment. Unusual patterns in logs often indicate security risks that require immediate attention.
Case Studies Highlighting Security Risks:
Escalation of privilege issues in Azure Active Directory Domain Services can arise when delegated permissions are improperly configured.
Mismanagement of consent settings may lead to unauthorized access to sensitive resources.
Limited Access Control in Complex Scenarios
Managing delegated permissions becomes challenging in complex environments with multiple users, teams, and applications. You may encounter scenarios where permissions overlap or conflict, making it difficult to maintain control. For instance, when multiple applications request access to shared resources, ensuring that each application has the correct level of access can be overwhelming.
To address these challenges, you should adopt a structured approach to permission management. Here’s how you can simplify access control:
Define clear roles and responsibilities for users and applications.
Use role-based access control (RBAC) to assign permissions based on user roles.
Regularly audit permissions to ensure they align with organizational policies.
Note: Limited access control can lead to operational inefficiencies. By implementing RBAC, you can streamline permission management and reduce the risk of conflicts.
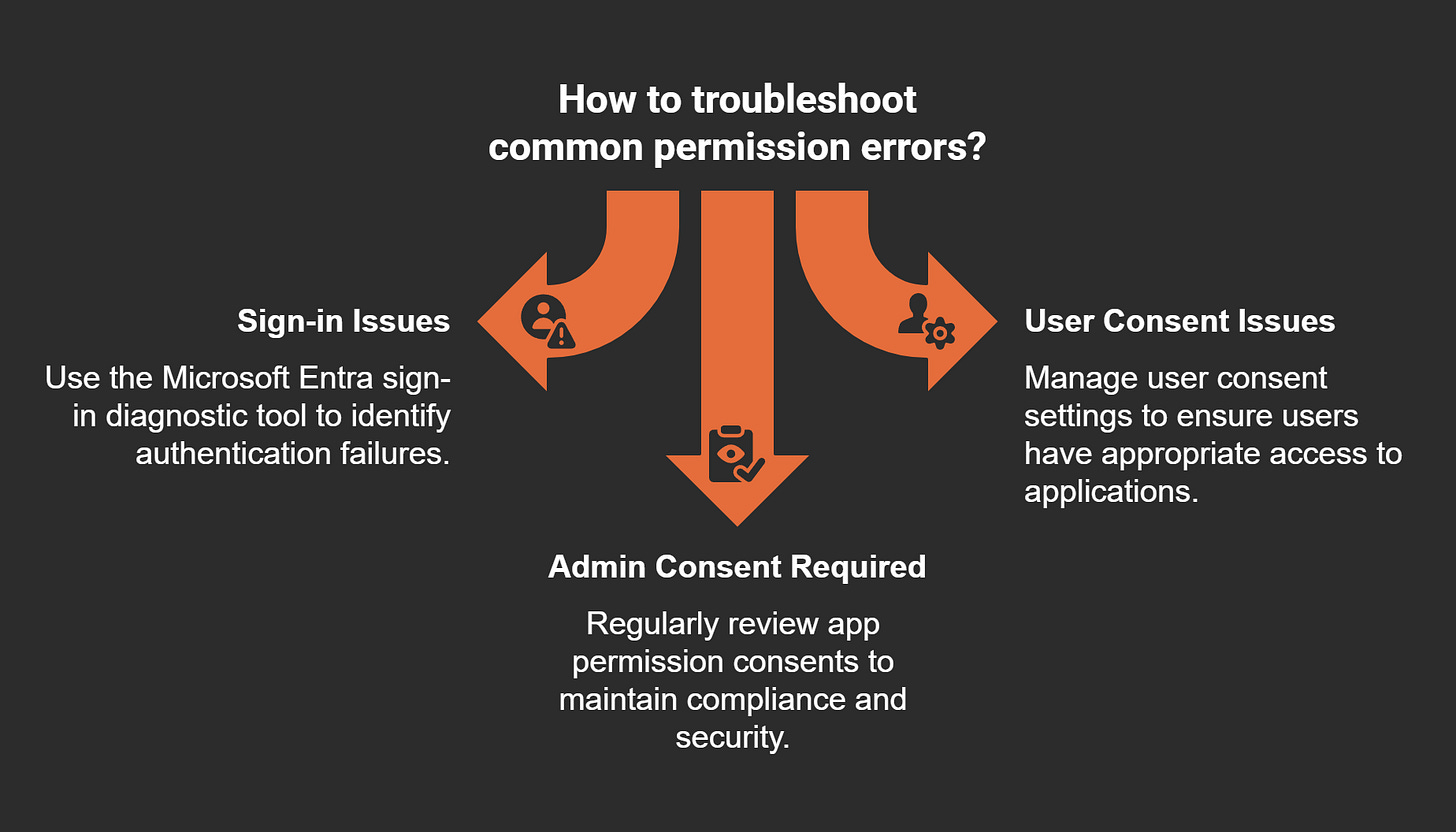
Troubleshooting Common Permission Errors
Errors in delegated permissions can disrupt workflows and hinder productivity. Common issues include sign-in failures, user consent problems, and admin consent requirements. Troubleshooting these errors requires a systematic approach to identify and resolve the root cause.
Here’s a table summarizing common issues and their troubleshooting steps:
You can also follow these steps to diagnose and resolve errors effectively:
Check the audit log for LoginFailure events to understand authentication issues.
Review the Reason for Failing to Login field in the User Profile for insights into consent problems.
Ensure applications request only the permissions they need to minimize admin consent requirements.
Tip: Always test permissions in a controlled environment before deploying them to production. This helps you identify and fix errors early.
Misconfigurations and Their Impact on Automation
Misconfigurations can disrupt automation processes and lead to unintended consequences. They occur when settings, parameters, or permissions are incorrectly configured. In platforms like Microsoft Graph and Power Automate, even a small error can cascade into larger issues. For example, assigning the wrong permission level to an application might grant it access to sensitive data or prevent it from performing essential tasks.
Automation relies on precise configurations to function smoothly. When these configurations go wrong, the results can be costly. Workflows may fail, sensitive information could be exposed, or systems might become vulnerable to attacks. Misconfigurations often stem from human error, such as misunderstanding permission requirements or overlooking critical settings.
Studies highlight how frequently misconfigurations affect automated systems. In one analysis of autonomous vehicles, 27.25% of detected bugs were linked to misconfigurations. Another study of unmanned aerial vehicles found that 19.6% of bugs resulted from parameter misuse and hardware inconsistencies. These examples show how common and impactful misconfigurations can be, even in advanced systems.
To minimize these risks, you should adopt a proactive approach. Start by documenting all permission requirements and configurations. Use tools to validate settings before deploying workflows. Regular audits can also help you identify and correct errors early. By addressing misconfigurations promptly, you can ensure that your automation processes remain secure and efficient.
Tip: Always test your configurations in a controlled environment. This practice helps you catch errors before they affect live workflows.
Misconfigurations can undermine the benefits of automation. However, with careful planning and regular reviews, you can reduce their impact and maintain the integrity of your systems. Understanding how delegated permission works and ensuring its proper configuration is a crucial step in this process.
Real-World Scenarios Highlighting Delegated Permission Issues
Automating Workflows in Power Automate
Power Automate simplifies complex workflows, but managing permissions can be tricky. When you automate tasks like sending emails or updating records, delegated permission ensures the application acts on your behalf. However, misconfigured permissions can disrupt these workflows. For instance, if a flow lacks the necessary access to a shared mailbox, it might fail to send emails.
Power Automate offers tools like Process Advisor to help you optimize workflows. It tracks the time each action takes, helping you identify bottlenecks. By focusing on the slowest steps, you can improve efficiency. Businesses of all sizes benefit from these advanced capabilities, making Power Automate a cost-effective solution for streamlining processes.
Accessing Shared Resources via Microsoft Graph
Accessing shared resources through Microsoft Graph often presents challenges. Errors like "400 Bad Request" or "403 Forbidden" can occur if your organization's conditional access policies block the request. These errors may also arise if OData access is disabled due to Exchange Web Services (EWS) application policies. Nested group permissions add another layer of complexity. If a parent group contains child groups with insufficient permissions, applications may fail to access the parent group.
To avoid these issues, ensure compliance with your organization's policies. Regularly review group permissions and test access configurations. This proactive approach minimizes disruptions and ensures smooth resource management.
Managing Permissions Across Teams and Departments
Managing permissions across teams and departments requires careful planning. In large organizations, overlapping roles and responsibilities can complicate access control. For example, when multiple teams share a resource, ensuring each team has the correct level of access becomes challenging. Mismanagement can lead to overexposure or restricted access, disrupting workflows.
Role-based access control (RBAC) simplifies this process. By assigning permissions based on roles, you can maintain clarity and consistency. Regular audits help you identify and resolve conflicts, ensuring permissions align with organizational policies. This structured approach enhances security and operational efficiency.
Solutions to Delegated Permission Challenges
Best Practices for Assigning Permissions
Assigning permissions effectively ensures secure and efficient workflows. Following best practices can help you avoid common pitfalls and maintain control over access rights. Here are some key recommendations:
Use Role-Based Access Control (RBAC) to assign permissions based on specific roles. This approach decentralizes administrative tasks and ensures users only access what they need.
Regularly review and update permissions to align with organizational changes. Outdated permissions can lead to security vulnerabilities.
Document all permission assignments. Clear records help you track changes and troubleshoot issues quickly.
By following these practices, you can reduce risks and ensure permissions are assigned thoughtfully.
Implementing Least Privilege Access
The principle of least privilege is a cornerstone of secure permission management. It ensures users operate with only the permissions necessary for their tasks. This approach minimizes risks and prevents overexposure of sensitive data.
For example, imagine an administrator using a privileged account accidentally executes malicious software. This could compromise the entire system. However, if the administrator had used a nonprivileged account, the damage would remain localized. Research shows that at least 80% of security breaches involve privileged credentials. By limiting access, you can significantly reduce the likelihood of such incidents.
Despite its importance, many organizations fail to implement this principle. Regular training and audits can help you enforce least privilege access effectively. This strategy not only protects your systems but also ensures compliance with security standards.
Testing and Debugging Permissions in Power Automate
Testing permissions in Power Automate is essential for ensuring workflows run smoothly. Misconfigured permissions can disrupt automation and lead to errors. To avoid these issues, you should test permissions in a controlled environment before deploying them.
Start by creating a test flow that mimics your actual workflow. Use this flow to verify that all required permissions are in place. If errors occur, review the logs to identify the root cause. Common issues include missing consent or insufficient access rights. Tools like the Microsoft Entra sign-in diagnostic tool can help you troubleshoot authentication problems.
Tip: Always test permissions with different user roles. This ensures your workflows function correctly across various scenarios.
By thoroughly testing and debugging permissions, you can prevent disruptions and maintain the reliability of your automated processes.
Utilizing Microsoft Support and Documentation
Microsoft provides extensive support and documentation to help you navigate delegated permission challenges. These resources are invaluable when you encounter issues with Microsoft Graph or Power Automate. By leveraging these tools, you can resolve problems efficiently and enhance your understanding of permission management.
Start by exploring the official Microsoft Learn platform. It offers step-by-step guides, tutorials, and examples tailored to common scenarios. For instance, if you face difficulties with admin consent while using Microsoft Graph API, the documentation explains how to configure permissions correctly. You can also find detailed instructions on managing user access in Microsoft Entra.
Tip: Bookmark key documentation pages for quick reference. This saves time when troubleshooting recurring issues.
Users often report challenges with accessing user details in Microsoft Entra. Many struggle to find clear solutions in the documentation. To address this, Microsoft continuously updates its resources to improve clarity and completeness. However, gaps may still exist. If you cannot find the answers you need, consider reaching out to Microsoft Support.
Common user feedback on documentation:
Difficulty understanding delegated permissions in Microsoft Entra.
Admin consent requirements for accessing user data via Microsoft Graph API.
Frustration with incomplete or unclear documentation.
Microsoft Support offers personalized assistance through forums, live chat, and ticketing systems. Engaging with these channels allows you to receive expert guidance tailored to your specific situation. Additionally, community forums like Microsoft Tech Community provide insights from other users who have faced similar challenges.
Note: When contacting support, prepare detailed information about your issue. Include error messages, configurations, and steps to reproduce the problem. This helps support teams provide faster and more accurate solutions.
By combining official documentation with support services, you can overcome delegated permission challenges effectively. These resources empower you to troubleshoot confidently and optimize your workflows.
Best Practices for Everyday Users
Staying Updated on Permission Changes
Staying informed about permission changes helps you maintain control over your workflows and data security. Permissions evolve as organizations update policies or introduce new tools. Keeping track of these changes ensures you avoid disruptions and unauthorized access.
Here are some effective ways to stay updated:
Monitor mailbox folder permissions regularly to prevent unauthorized access.
Use tools like AdminDroid’s auditing feature to track changes made by different users.
Set up instant notifications for modifications in permissions to stay informed in real time.
Schedule reports to receive regular insights into permission updates.
Tip: Automate your monitoring process with tools that provide detailed reports and alerts. This saves time and ensures you never miss critical changes.
By staying proactive, you can safeguard your workflows and ensure permissions align with your needs.
Collaborating Effectively with IT Teams
Working closely with IT teams simplifies permission management and enhances security. IT teams possess the expertise to monitor and update permissions efficiently. You can support their efforts by communicating your needs clearly and following established policies.
Effective collaboration starts with understanding the importance of synchronized permissions. For example, Microsoft Teams permissions should align with SharePoint and OneDrive settings to maintain consistent access control. IT teams often rely on governance frameworks, such as those outlined in "The Essential Guide to Microsoft Teams Governance," to ensure permissions remain balanced across platforms.
Additionally, IT teams may create policies that define the scope of monitoring user activities. These policies help balance security needs with privacy concerns. By adhering to these guidelines, you contribute to a secure and well-managed environment.
Note: Regularly discuss permission requirements with IT teams to address any gaps or conflicts. Clear communication fosters trust and ensures smooth workflows.
Conducting Regular Permission Audits
Auditing permissions regularly helps you identify unnecessary privileges and maintain security. Permissions can accumulate over time, leading to overexposure or inefficiencies. Conducting audits ensures your access rights remain appropriate and aligned with organizational policies.
Follow these steps for effective audits:
Review all assigned permissions to identify outdated or excessive access.
Use tools that provide detailed reports on permission changes and user activities.
Schedule audits periodically to ensure permissions stay current and relevant.
Tip: Document audit findings to track trends and address recurring issues. This helps you refine permission management over time.
By conducting regular audits, you can prevent security risks and optimize your workflows. This practice ensures your permissions remain efficient and secure.
Understanding delegated permissions is essential for managing workflows securely and efficiently. These permissions empower applications to act on your behalf while respecting your access rights. However, challenges like security risks, misconfigurations, and troubleshooting errors can complicate their use.
To overcome these hurdles, focus on solutions such as implementing least privilege access, testing permissions, and conducting regular audits. These strategies ensure your workflows remain secure and effective.
Pro Tip: Stay proactive by collaborating with IT teams and keeping up with permission updates. This approach helps you maintain control and avoid disruptions.
By adopting these practices, you can confidently manage permissions and unlock the full potential of automation tools like Microsoft Graph and Power Automate.
FAQ
1. What are delegated permissions in simple terms?
Delegated permissions let an app act on your behalf using your access rights. For example, when an app sends an email for you, it uses delegated permissions to access your mailbox securely.
Tip: Always review what permissions an app requests before granting access.
2. How do delegated permissions differ from application permissions?
Delegated permissions require a signed-in user and work within their access limits. Application permissions, however, operate independently of users and can access broader resources.
Permission TypeRequires User?Access ScopeDelegated PermissionsYesUser-specificApplication PermissionsNoSystem-wide
3. Why do I need to consent to permissions?
Consent ensures you control what apps can access. It protects your data by requiring explicit approval before an app can act on your behalf.
Note: Always read the consent prompt carefully to understand what data the app will access.
4. How can I troubleshoot permission errors in Power Automate?
Start by checking the error message. Use tools like the Microsoft Entra sign-in diagnostic tool to identify issues. Verify that the app has the correct permissions and test the flow in a controlled environment.
Pro Tip: Test permissions with different user roles to ensure smooth workflows.
5. What is the best way to manage permissions across teams?
Use role-based access control (RBAC). Assign permissions based on roles, not individuals. Regularly audit permissions to ensure they align with team responsibilities.
Reminder