Fix SharePoint Oversharing Before Copilot Goes Live
Fix sharepoint oversharing before Copilot goes live to prevent accidental exposure of sensitive information. Many organizations face major risks when broad permissions remain unchecked in SharePoint. Oversharing creates a significant barrier to deploying Copilot safely. IT admins and business leaders must fix sharepoint oversharing to ensure data remains secure and only accessible to the right people.
Key Takeaways
Fix SharePoint oversharing before deploying Copilot to prevent accidental exposure of sensitive data.
Use SharePoint governance reports, Teams exports, and PowerShell scripts to identify overshared sites and risky permissions.
Remove broad sharing links, tighten external sharing settings, and break permission inheritance to reduce oversharing quickly.
Apply sensitivity labels, data loss prevention policies, and automate access reviews to prevent future oversharing.
Regular audits, clear communication, and ongoing training keep SharePoint secure and support safe Copilot use.
Copilot Data Risks
Oversharing Impact
Oversharing in SharePoint creates a significant risk when organizations enable Copilot. When permissions are too broad, Copilot can access and surface sensitive information that users did not intend to share. Recent security incidents highlight the dangers:
The SSRF vulnerability (CVE-2024-38206) in Copilot Studio allowed attackers to bypass protections and access internal Microsoft cloud infrastructure, increasing the risk of sensitive data leakage.
Security researchers found that prompt injection attacks in Microsoft 365 Copilot could lead to data exfiltration, exposing confidential business information.
The US Congress banned Copilot for staff due to concerns about accidental leaks of sensitive congressional data.
Real-world cases show that finance, HR, and R&D departments face exposure of unreleased earnings, employee records, and intellectual property when Copilot accesses overshared files.
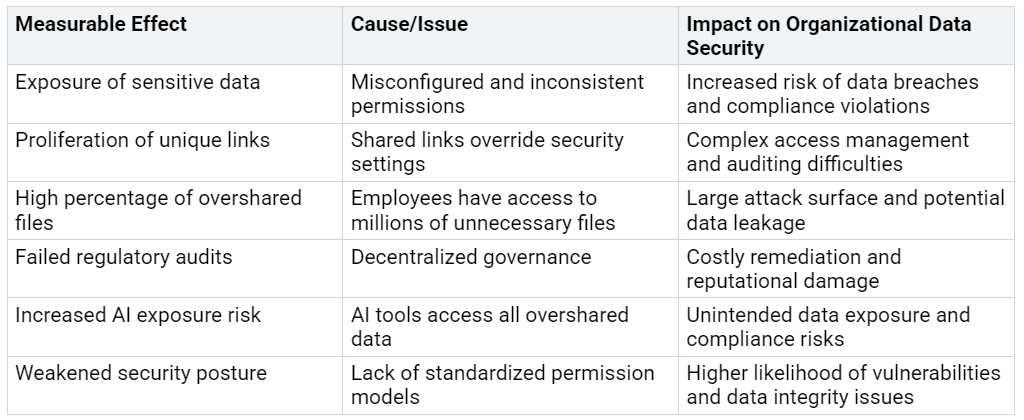
Oversharing issues have measurable effects on organizational data security. The following table summarizes key impacts:
Note: Studies show that 16% of corporate files are overshared, and employees often have access to millions of files they do not need.
Why Fix SharePoint Oversharing Now
Organizations must address oversharing before deploying Copilot. AI tools like Copilot do not distinguish between files that should be private and those that are safe to share. They surface any data within their reach, which can lead to unintentional exposure of confidential information.
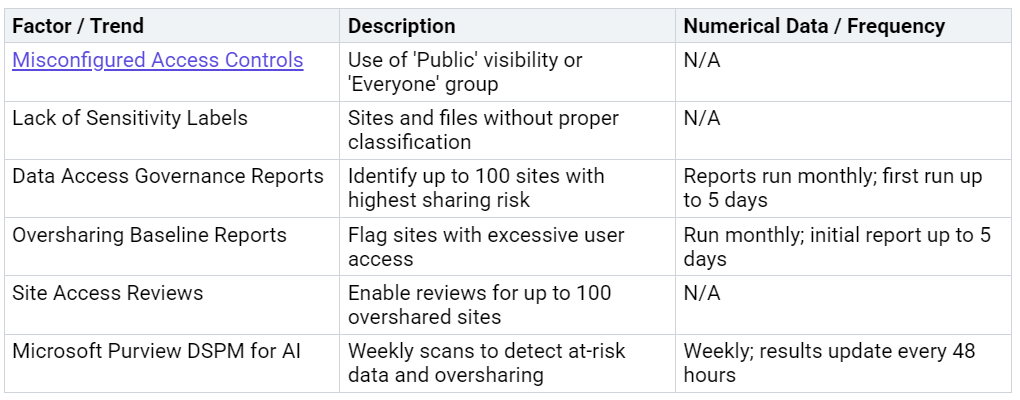
Several trends emphasize the urgency:
Organizations that delay fixing oversharing risk failed audits, regulatory penalties, and reputational harm. A law firm recently had to remove Copilot after it exposed confidential partner bonus data. Proactive remediation ensures that only the right people can access sensitive files, reducing the risk of data breaches and compliance violations.
Identify Overshared Sites
SharePoint Governance Reports
Organizations must begin their oversharing remediation journey by leveraging data access governance reports in the SharePoint admin center. These reports provide a comprehensive overview of sharing activities across all SharePoint sites. Administrators can quickly identify sites with broad sharing links, such as those accessible to "anyone" or "people in the organization." Data access governance reports highlight which sites have the highest risk of oversharing, allowing IT teams to prioritize remediation efforts.
To access these reports, administrators navigate to the SharePoint admin portal and select the data access governance section. The reports display the top 100 sites with the most extensive sharing. This information includes the type of sharing links, the number of users with access, and whether sensitivity labels are applied. Exporting this data to Excel enables deeper analysis and cross-referencing with other sources. By reviewing these reports regularly, organizations maintain visibility into their sharing landscape and can act on new risks as they arise.
Tip: Data access governance reports require SharePoint Premium or Microsoft 365 E5 licensing. Organizations should ensure they have the correct subscriptions to unlock these advanced reporting features.
Teams and Group Access
Microsoft Teams and Microsoft 365 Groups often serve as gateways to SharePoint sites. Every Team creates a linked SharePoint site, and group membership determines access to shared files and folders. Oversharing can occur when Teams are set to "public" or when large groups receive access unintentionally. Administrators should review the Teams admin center to identify public teams and those with unusually high membership counts.
A recent analysis revealed that over 80% of nearly 10,000 Team-linked SharePoint sites created between late 2019 and 2022 were inactive. This finding demonstrates the scale of unused or potentially overshared resources within many organizations. Monitoring solutions now offer dashboards that track exposure reduction, risk scores, and audit trails of administrative actions. These tools help organizations measure the effectiveness of their efforts to reduce oversharing in Teams, Groups, and SharePoint sites.
Administrators should export lists of Teams, Groups, and their associated SharePoint sites to Excel. By cross-referencing this data with data access governance reports, they can pinpoint sites with overlapping risks. This process uncovers existing overshared content and highlights where immediate action is needed.
PowerShell and Data Mapping
PowerShell scripts provide a powerful method for extracting detailed permission and membership data from Microsoft 365 environments. Administrators can use PowerShell to list all SharePoint sites, enumerate group memberships, and count the number of users with access to each site. This approach enables organizations to map their entire sharing landscape efficiently.
A typical workflow involves running PowerShell commands to gather site and group data, exporting the results to CSV files, and then analyzing the data in Excel. By combining outputs from PowerShell with data access governance reports and Teams exports, administrators create a unified view of oversharing risks. This comprehensive mapping supports informed decision-making and prioritizes remediation efforts.
Recommendations: Schedule regular PowerShell audits to maintain up-to-date visibility of permissions. Use data mapping to validate the effectiveness of changes made in response to data access governance findings.
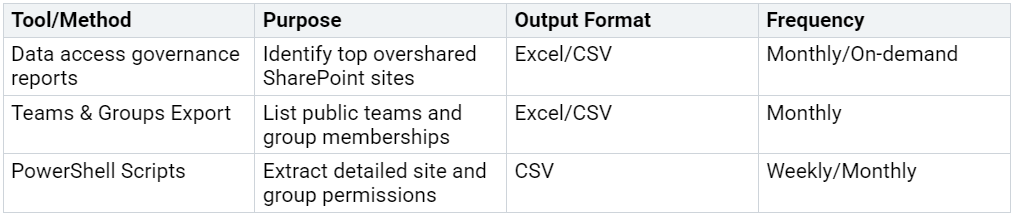
Summary Table: Oversharing Identification Tools
By combining these tools and approaches, organizations gain a clear understanding of their oversharing risks. Regular analysis and cross-referencing of exported data ensure that no site or group escapes scrutiny. These recommendations form the foundation for a robust data access governance strategy.
Fix SharePoint Oversharing Fast
Remove Broad Sharing Links
Organizations often discover that broad sharing links create the largest risk surface in SharePoint. These links, such as "Anyone with the link" or "People in your organization," can unintentionally grant access to sensitive files. To fix sharepoint oversharing, administrators should start by identifying and removing these links. The SharePoint admin center provides a centralized view of sharing links across all sites. Administrators can filter for links with the widest access and revoke them in bulk.
A practical approach involves exporting sharing link data to Excel. This allows teams to sort and prioritize which links to address first. Removing unnecessary links reduces the chance that Copilot or Microsoft 365 search will surface confidential information. IT teams should also enable external sharing alerts to receive notifications when users create new broad links. These alerts help maintain ongoing oversight and prevent new oversharing incidents.
Tip: Regularly review sharing link reports and set up automated reminders for quarterly audits. This habit ensures that new risks do not go unnoticed.
Adjust External Sharing Settings
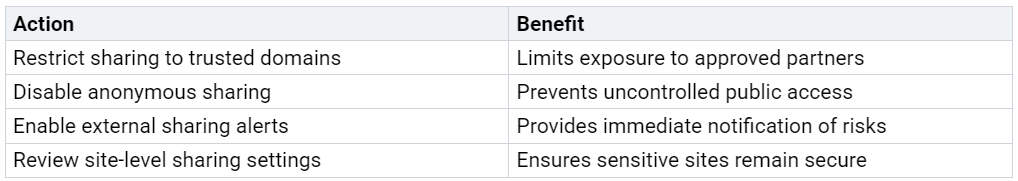
External sharing settings play a critical role in controlling who can access SharePoint content. Many organizations set these controls too loosely, which leads to oversharing. To fix sharepoint oversharing, administrators should review and tighten these settings at both the tenant and site levels. The SharePoint admin center allows for granular adjustments, including restricting sharing to specific domains or disabling anonymous access.
Teams should also configure external sharing alerts to notify administrators when users attempt to share content outside the organization. These alerts provide early warning of potential data leaks. By combining strict external sharing settings with real-time alerts, organizations can quickly detect and respond to risky sharing behaviors.
A table below summarizes recommended actions:
Break Permission Inheritance
Many SharePoint sites inherit permissions from parent sites or groups. This inheritance can lead to unintentional access for large numbers of users. To fix sharepoint oversharing, administrators should break permission inheritance on sites or libraries that contain sensitive data. Breaking inheritance allows for custom permissions, ensuring only authorized users have access.
The process involves navigating to the site or library, selecting "Permissions," and choosing "Stop Inheriting Permissions." Administrators can then remove unnecessary users or groups. This targeted approach reduces the risk of accidental exposure through Copilot or search features.
Note: After breaking inheritance, document all changes and communicate with site owners. Clear records help maintain compliance and support future audits.
By following these steps, organizations can fix sharepoint oversharing quickly and effectively. Proactive management of sharing links, external sharing settings, and permission inheritance creates a safer environment for Copilot deployment.
Advanced Oversharing Prevention
Sensitivity Labels
Sensitivity labels form the foundation of advanced oversharing prevention in SharePoint and Microsoft 365. Administrators can classify content by applying labels that enforce encryption, restrict downloads, and control external sharing. When organizations configure sensitivity labels at the site or file level, all content inherits these protections. This approach helps prevent oversharing by ensuring only authorized users can access sensitive information types.
Tools such as AdminDroid provide auditing for sensitivity label activities, offering insights into file usage and external sharing. Features like "user access to content expires" automatically limit access duration, reducing the window for potential exposure. Conditional Access policies further block downloads from unmanaged devices, while adaptive protection monitors suspicious activity. These combined controls statistically reduce the risk of data exposure and support ongoing compliance.
Data Loss Prevention Policies
Data loss prevention policies represent a critical layer in advanced oversharing prevention. Organizations deploy these policies to detect and block the sharing of confidential data, both internally and externally. Several recommendations help strengthen this approach:
Implement secure-by-default sensitivity labeling to protect data at scale.
Derive file labels from SharePoint and Teams site labels for consistency.
Train users to update labels for exceptions, minimizing manual decisions.
Use auto-labeling for highly sensitive content to enforce stricter controls.
Accelerate deployment of data loss prevention policies to restrict sharing of labeled content.
Employ Insider Risk Management to detect suspicious sharing behaviors.
Microsoft Purview’s Data Security Posture Management ensures that AI agents like Copilot cannot use sensitive labeled documents as grounding data. Auto-labeling in Dataverse classifies sensitive data upon ingestion, maintaining consistent protection. These policies, combined with machine learning and lifecycle management, create a robust advanced oversharing prevention checklist.
Automate Access Reviews
Automated access reviews play a vital role in advanced oversharing prevention. Manual reviews often lead to delays, errors, and missed risks. Automation introduces role-based access control, personalized user experiences, and streamlined workflows. Automated notifications keep stakeholders accountable and informed.
Organizations that automate microsoft 365 groups access reviews see improved transparency and reduced manual effort. For example, a leading media company replaced manual reviews with automated processes, reducing permission delays and enhancing security. Automated reviews ensure that only the right users retain access, supporting compliance and reducing oversharing risks.
Ongoing governance and user training remain essential. Regularly update the advanced oversharing prevention checklist, conduct microsoft 365 groups access reviews, and reinforce data loss prevention policies. These steps help prevent oversharing and protect sensitive information types across the organization.
Workarounds for Copilot Deployment
Exclude Sites from Copilot/Search
Organizations can reduce the risk of sensitive data exposure by excluding overshared sites from the Copilot and Microsoft 365 search index. When administrators remove high-risk sites from Copilot’s reach, they limit the AI’s ability to surface confidential information. This approach narrows Copilot’s semantic index to a curated list of trusted sites, which strengthens data governance. However, Copilot may still access files that users have previously interacted with, even if those files reside on excluded sites. Regular permission audits and user education remain essential to address this gap. Administrators should use sharepoint restricted access control to block Copilot from indexing specific sites until all oversharing issues are resolved.
Note: Excluding sites does not fully eliminate risk. Combine this workaround with ongoing access reviews and governance for best results.
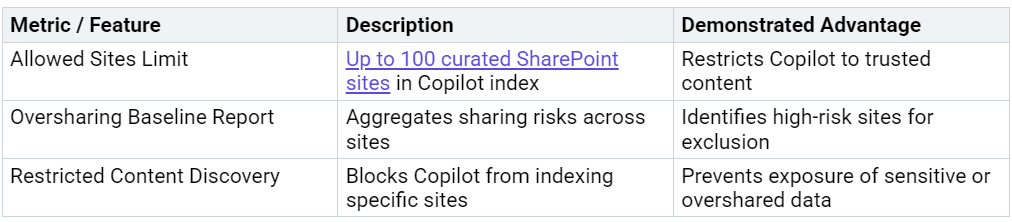
Enable Restricted Search Mode
Restricted search mode provides another layer of protection for organizations preparing for Copilot deployment. By enabling this mode, administrators can limit Copilot’s search capabilities to a defined set of SharePoint sites. This feature allows organizations to manage which sites Copilot can index, reducing the risk of data leakage from overshared or misconfigured locations. The table below summarizes key metrics that demonstrate the advantage of this approach:
Administrators should monitor these metrics to ensure restricted search mode delivers the intended security benefits.
Whitelist Critical Sites
Whitelisting critical sites ensures that only approved SharePoint locations become available to Copilot and Microsoft 365 search. Administrators can use sharepoint restricted access control to create a whitelist of up to 100 sites. This process allows organizations to prioritize business-critical content while excluding sites with unresolved oversharing risks. Site access reviews and permission audits help maintain the integrity of the whitelist. Regularly updating the whitelist ensures that Copilot continues to index only secure, compliant content.
Next Steps and Best Practices
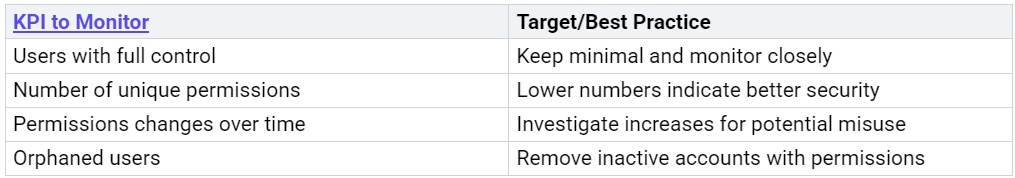
Remediation Checklist
A structured remediation checklist helps organizations address SharePoint oversharing efficiently. Teams should focus on clear steps and monitor key performance indicators to ensure ongoing security.
Define roles and access levels before implementing permissions to reduce complexity.
Apply the principle of least privilege, granting users only the access needed for their responsibilities.
Assign permissions through SharePoint groups instead of individual users for streamlined management.
Limit unique permissions and avoid breaking inheritance unless necessary.
Leverage inheritance for subsites, lists, and libraries to manage permissions effectively.
Conduct regular audits and reviews of permissions as roles change.
Provide user training on permission implications and data sharing best practices.
Implement governance policies to enforce consistent permission and access management.
Use advanced security settings such as encryption, security labels, and Information Rights Management for sensitive data.
Regularly reviewing these KPIs ensures that policies remain effective and risks stay manageable.
Communicate with Stakeholders
Effective communication with stakeholders drives successful data protection initiatives. Organizations that use multiple channels—such as email, instant messaging, video conferencing, and printed reports—see higher engagement. Clear and consistent messaging, feedback loops, and tailored communication plans help maintain stakeholder trust.
A recent study found that 73% of organizations with strong communication strategies achieve their change management goals. Teams should track metrics like email open rates, meeting participation, and survey responses to measure engagement. Adjusting communication plans based on feedback and emerging trends ensures that information remains relevant and timely.
Tip: Calculate communication effectiveness by dividing the number of engaged stakeholders by the total number, then multiplying by 100.
Schedule Regular Audits
Regular audits form the backbone of effective SharePoint governance. Running the Oversharing Baseline Report monthly through PowerShell provides a comprehensive permissions analysis. Data Access Governance reports, which track sharing events over the past 28 days, also support a monthly review cycle. Site access reviews for up to 100 overshared sites allow delegated site owners to participate in ongoing governance.
Monthly audits help maintain a stable baseline and quickly identify new risks. By aligning audit frequency with governance cycles, organizations ensure that policies adapt to evolving threats and organizational changes.
Consistent audits and reviews reinforce the effectiveness of policies and support a proactive security posture.
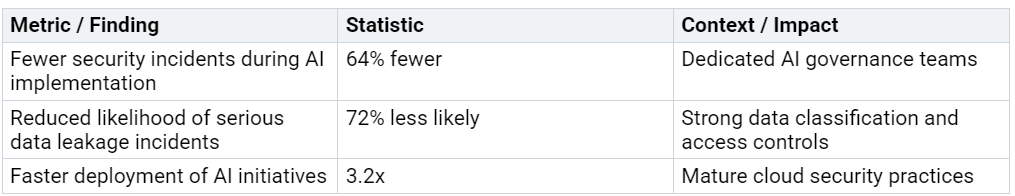
Addressing SharePoint oversharing before Copilot goes live remains critical for every organization. Teams that identify, remediate, and prevent oversharing risks see measurable improvements in security and compliance. The following table highlights the impact of robust data governance:
Ongoing training and regular policy updates help maintain a secure environment. Organizations that act now protect sensitive data and enable Copilot with confidence.
FAQ
What is SharePoint oversharing?
SharePoint oversharing happens when users grant access to files or sites too broadly. This often includes sharing with "anyone" or "everyone in the organization." Oversharing increases the risk of unauthorized data exposure, especially when deploying AI tools like Copilot.
How can organizations quickly identify overshared sites?
Administrators can use SharePoint data access governance reports, Teams admin center exports, and PowerShell scripts. Exporting this data to Excel helps cross-reference and prioritize sites with the highest risk. Regular reviews ensure ongoing visibility.
Does excluding a site from Copilot also remove it from Microsoft 365 search?
Yes. When administrators exclude a SharePoint site from Copilot, it also becomes unavailable in Microsoft 365 search results. This action helps prevent accidental exposure of sensitive content while remediation takes place.
What are the best practices for ongoing oversharing prevention?
Organizations should apply sensitivity labels, enforce data loss prevention policies, and automate access reviews. Regular audits and user training help maintain a secure environment. These steps reduce the risk of future oversharing incidents.
Can Copilot access files that users have never opened?
Copilot can only surface files that users have permission to access. If a file resides on an overshared site, Copilot may expose it, even if the user has never opened it before. Proper permissions remain essential.