How to Achieve Ultimate Data Security in Microsoft Fabric Data Warehousing
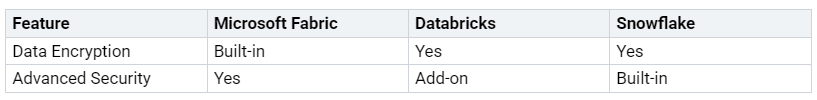
You get Ultimate Data Security in Microsoft Fabric by using smart security tools and strong rules for access. Microsoft Fabric is special because it has built-in encryption, role-based access, and tough compliance rules:
Keep your important data safe and follow the rules with these strong tools.
Key Takeaways
Use sensitivity labels and Purview policies to …