How to Strengthen Data Security in Power Apps Model-Driven Apps
Securing sensitive data within your Power Apps Model-Driven Apps is essential. These apps often handle critical workflows and confidential information, making them a prime target for breaches. By implementing strong security strategies, you can protect data integrity and ensure compliance with industry standards. Taking proactive steps to safeguard your applications not only keeps your organization secure but also builds trust with your users. This guide delivers actionable insights to help you fortify your app's security framework effectively.
Key Takeaways
Use role-based access control (RBAC) to manage user permissions. This makes sure users only see data they need, keeping it secure.
Protect sensitive data with field-level and row-level security. Field-level security hides certain data fields. Row-level security limits records based on user roles.
Check user activities often using audit logs and reports. This helps find strange actions or risks and respond quickly.
Train users regularly about security. Teaching your team good habits and warning signs helps them stop breaches early.
Create data loss prevention (DLP) rules to manage data sharing. DLP rules stop data from being shared wrongly and follow privacy laws.
Security Strategies in Power Apps Model-Driven Apps
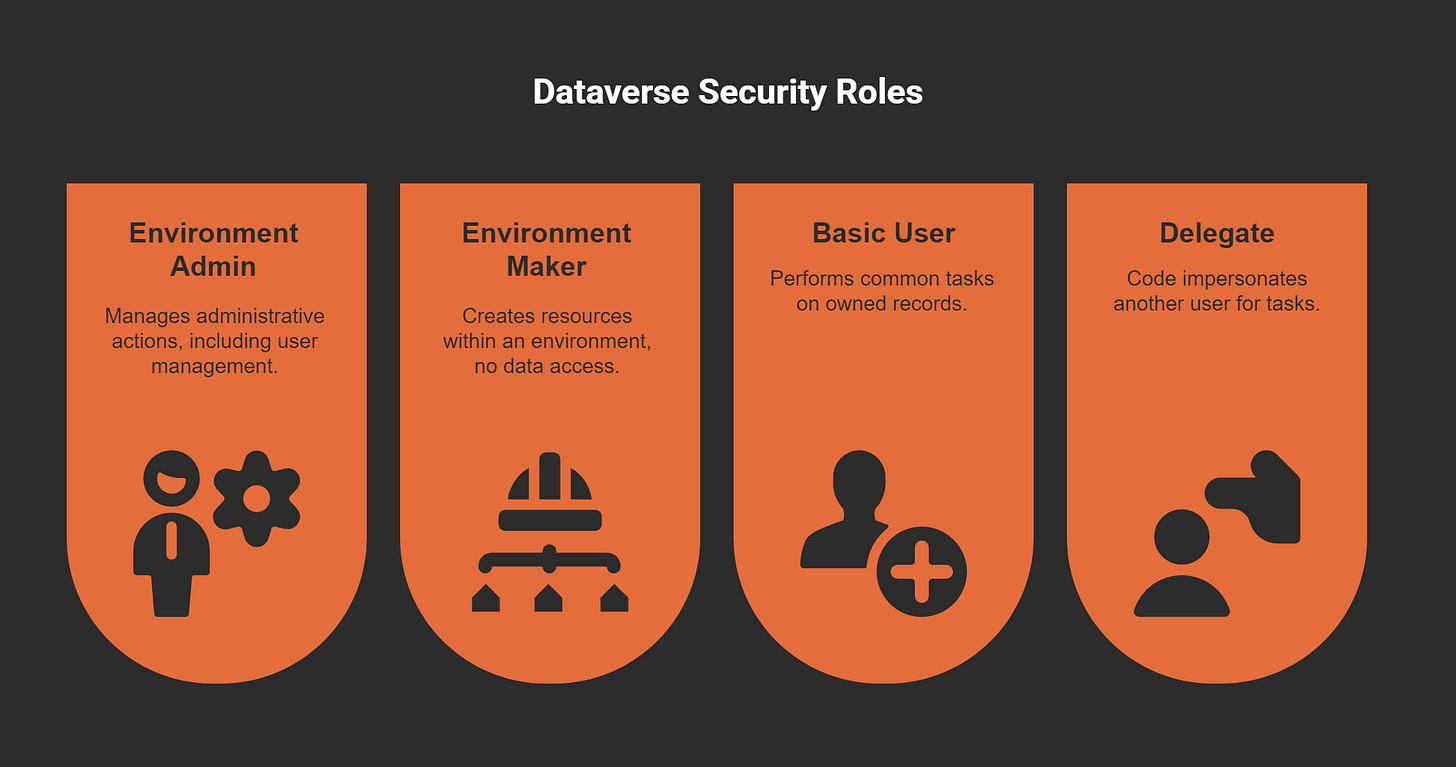
Overview of Dataverse Security Roles
Dataverse security roles form the foundation of protecting your data in Power Apps Model-Driven Apps. These roles define what actions users can perform and which data they can access. By assigning appropriate roles, you ensure that users only interact with the information necessary for their tasks.
Here are some key security roles in Dataverse:
Understanding these roles helps you leverage robust security features and maintain control over your app's environment.
Field-Level Security for Sensitive Data
Field-level security allows you to protect sensitive information by restricting access to specific fields in a table. For example, you can limit access to fields containing personal or financial data, ensuring only authorized users can view or edit them.
This feature works by associating security profiles with fields. You can configure these profiles to grant read, write, or no access permissions based on user roles. By implementing field-level security, you reduce the risk of unauthorized data exposure and maintain compliance with privacy regulations.
Row-Level Security for Record Access Control
Row-level security ensures users only access records relevant to their roles. For instance, a sales representative might only see customer records assigned to them. This strategy enhances data protection by preventing unauthorized users from viewing or modifying records they shouldn't access.
Key features of row-level security include:
Security Roles: Define roles to restrict access to specific records.
Row-Level Permissions: Control visibility of records in tables and subgrids based on user permissions.
API Integration: Automatically checks user permissions during record access, ensuring compliance with security rules.
By implementing row-level security, you create a tailored experience for users while safeguarding your organization's data.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a cornerstone of managing data security in Power Apps Model-Driven Apps. It allows you to define and enforce permissions based on user roles, ensuring that individuals only access the data and features necessary for their responsibilities. By implementing RBAC, you can streamline security management and reduce the risk of unauthorized access.
Assigning Security Roles to Users
Assigning security roles is essential for controlling access in Power Apps Model-Driven Apps. Each user must have a role that aligns with their responsibilities. Without a proper role, users cannot access the app or its data.
Here are some key considerations for assigning security roles:
By following these guidelines, you can ensure that users have the appropriate level of access without compromising security.
Customizing Roles for Business Needs
Every business has unique requirements, and customizing roles allows you to tailor access controls to meet those needs. Instead of relying solely on default roles, you can create custom roles that align with your organization's workflows and security policies.
Custom roles offer several benefits:
Customizing roles not only enhances security but also improves operational efficiency. For example, you can create a role for sales managers that grants access to team performance dashboards while restricting access to sensitive financial data.
Managing Permissions for Teams
Managing permissions for teams simplifies access control when multiple users share similar responsibilities. Instead of assigning roles individually, you can assign them at the team level. This approach ensures consistency and reduces administrative overhead.
To manage team permissions effectively:
Create Teams in Dataverse: Group users based on their roles or departments.
Assign Security Roles to Teams: Apply roles to teams instead of individual users. This ensures all team members inherit the same permissions.
Monitor and Adjust Permissions: Regularly review team roles to ensure they align with current responsibilities.
For example, you can create a "Customer Support" team and assign it a role that grants access to customer records and support tickets. This setup ensures that all support agents have the tools they need without exposing unnecessary data.
By leveraging RBAC, you can implement security strategies that protect your data while maintaining flexibility and efficiency.
Advanced Security Features
Conditional Access Policies for Authentication
Conditional Access Policies provide an additional layer of security by controlling how users authenticate when accessing Power Apps Model-Driven Apps. These policies use signals like user location, device type, or application to determine access permissions. For example, you can require multi-factor authentication (MFA) for users accessing the app from an untrusted network.
To implement Conditional Access Policies effectively:
Define Access Conditions: Specify conditions like device compliance, IP address, or geographic location.
Set Authentication Requirements: Enforce MFA or block access based on the defined conditions.
Monitor Policy Impact: Use Azure Active Directory logs to review how policies affect user access.
These policies ensure that only authorized users can access your apps, even in dynamic environments. They also help protect against unauthorized access attempts, enhancing overall security.
Data Loss Prevention (DLP) Policies
Data Loss Prevention (DLP) Policies safeguard sensitive information by controlling how data moves within and outside your organization. In Power Apps Model-Driven Apps, DLP policies prevent users from sharing data with unauthorized apps or services.
Key steps to configure DLP policies include:
Identify Sensitive Data: Determine which data requires protection, such as financial records or personal information.
Define Policy Rules: Specify actions to restrict, such as blocking data export to non-compliant apps.
Apply Policies to Environments: Assign DLP policies to specific environments to ensure consistent enforcement.
For instance, you can block users from exporting customer data to external file-sharing apps. This prevents accidental or intentional data leaks, ensuring compliance with privacy regulations. DLP policies act as a critical component of your security strategies, helping you maintain control over sensitive information.
Business Rules for Enforcing Security Logic
Business rules in Power Apps Model-Driven Apps enforce data integrity and security logic by validating data before submission. These rules ensure that users follow predefined business logic, reducing the risk of errors or unauthorized actions.
Benefits of using business rules include:
They validate data to ensure it meets specific criteria.
They enforce workflows that align with organizational policies.
They enhance security by restricting invalid or incomplete data submissions.
For example, you can create a rule that prevents users from saving a record unless all required fields are completed. This ensures that data adheres to your organization's standards.
Business rules indirectly strengthen security by ensuring data accuracy and compliance. They also reduce the need for manual checks, saving time and minimizing errors.
By leveraging these advanced features, you can create a secure and efficient environment for your Power Apps Model-Driven Apps. These tools not only protect your data but also enhance user trust and operational efficiency.
Monitoring and Auditing Activities
Monitoring and auditing activities in Power Apps Model-Driven Apps are essential for maintaining data security and ensuring compliance. By tracking user actions and app events, you can identify potential vulnerabilities and respond to security incidents effectively.
Setting Up and Managing Audit Logs
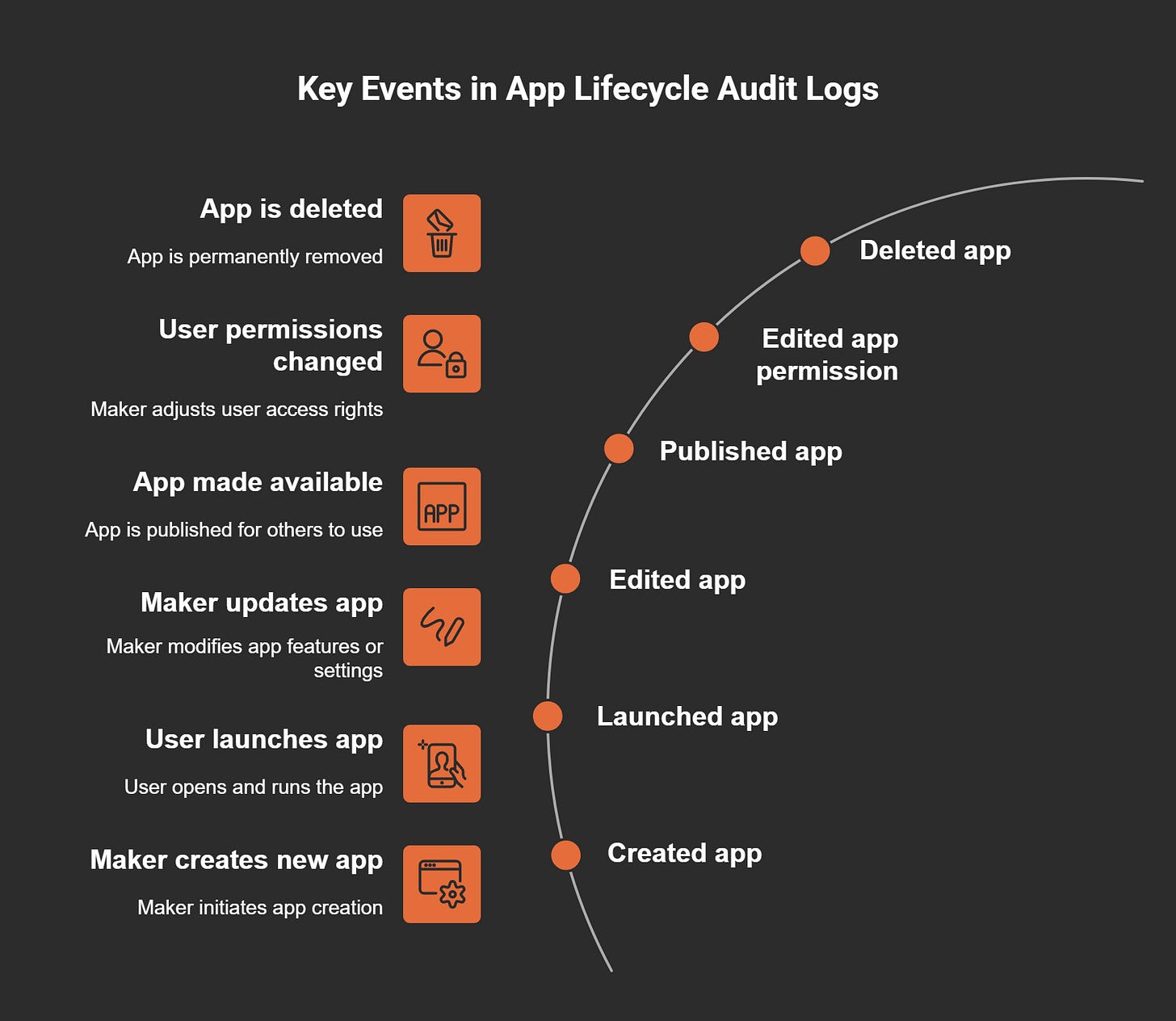
Audit logs provide a detailed record of user and system activities within your apps. These logs help you track changes, monitor access, and maintain accountability. To set up audit logs, enable auditing in the Microsoft Dataverse environment and configure the entities and fields you want to monitor.
Key events captured in audit logs include:
These logs allow you to trace actions, such as when an app is launched or permissions are modified. By reviewing this data, you can ensure compliance and detect unauthorized activities.
Reviewing User Activity Reports
User activity reports provide insights into how users interact with your apps. Regularly reviewing these reports helps you identify unusual patterns or behaviors that may indicate security issues. For example, monitoring login times or access frequency can reveal potential unauthorized access attempts.
Benefits of reviewing user activity reports include:
Spotting unusual behaviors that may signal security vulnerabilities.
Maintaining the integrity of your apps by identifying anomalies.
Receiving real-time alerts for abnormal activities through automated monitoring tools.
By analyzing these reports, you can take proactive steps to address potential threats before they escalate.
Identifying and Addressing Security Incidents
When a security incident occurs, quick identification and resolution are critical. Audit logs and user activity reports play a vital role in this process. They help you pinpoint the source of the issue and understand its impact. For example, tracking CRUD (Create, Read, Update, Delete) activities allows you to assess the scope of a problem and ensure compliance with data protection regulations.
To address incidents effectively:
Investigate the root cause using audit logs and activity reports.
Take corrective actions, such as revoking access or updating permissions.
Implement preventive measures to avoid similar incidents in the future.
By actively monitoring and auditing your apps, you can create a secure environment that protects your data and builds user trust.
User Education and Awareness
Conducting Security Training Programs
Security training programs play a vital role in protecting your Power Apps Model-Driven Apps. These programs equip users with the knowledge to recognize and respond to potential threats. You can organize regular workshops or online sessions to educate your team about best practices for data security.
Focus on topics like secure app usage, identifying suspicious activities, and understanding organizational policies. Interactive sessions, such as quizzes or scenario-based exercises, can make learning more engaging. By investing in training, you empower your users to act as the first line of defense against security breaches.
Tip: Schedule periodic refresher courses to ensure users stay updated on evolving security threats.
Promoting Awareness of Phishing and Social Engineering
Phishing and social engineering attacks exploit human vulnerabilities. Raising awareness about these tactics helps users avoid falling victim to them.
Here are some effective strategies:
Regular and Updated Training Programs: Teach users about the latest social engineering techniques.
Simulated Phishing Exercises: Conduct mock phishing campaigns to help users identify suspicious emails.
Lessons on AI-Specific Threats: Educate users about AI-generated phishing emails and DeepFakes.
For example, you can simulate a phishing email that mimics a legitimate request. Afterward, review the results with your team to highlight red flags they missed. These exercises build confidence and improve their ability to detect threats in real-world scenarios.
Note: Awareness campaigns should be ongoing to address new and emerging threats.
Encouraging Strong Password Practices
Strong passwords are a cornerstone of data security. Encourage users to create passwords that are difficult to guess but easy to remember. A good practice is to use a combination of uppercase and lowercase letters, numbers, and special characters.
You can also promote the use of password managers to store and generate secure passwords. These tools reduce the risk of users reusing passwords across multiple platforms. Additionally, remind users to update their passwords regularly and avoid sharing them with others.
Pro Tip: Implement multi-factor authentication (MFA) to add an extra layer of security to your apps.
By fostering a culture of security awareness, you create a safer environment for your Power Apps Model-Driven Apps. Users who understand their role in protecting data become valuable allies in your organization's security efforts.
Strengthening data security in Power Apps Model-Driven Apps requires a multi-faceted approach. You can implement role-based access control to manage permissions effectively. Advanced features like field and row-level security, conditional access policies, and data loss prevention policies enhance protection. Monitoring user activities and educating your team about security best practices further fortify your defenses. These security strategies not only safeguard sensitive data but also ensure compliance with industry regulations. By taking proactive measures, you create a secure environment that fosters trust and operational efficiency.
FAQ
What is the difference between field-level and row-level security?
Field-level security restricts access to specific fields within a table, while row-level security controls access to entire records. You can use field-level security to protect sensitive data like financial details and row-level security to limit record visibility based on user roles.
How do you assign security roles in Power Apps Model-Driven Apps?
You assign security roles through the Microsoft Dataverse environment. Navigate to the user settings, select the user, and assign the appropriate role. Ensure the role aligns with the user's responsibilities and includes necessary permissions for accessing app features and data.
Can you monitor user activities in Power Apps?
Yes, you can monitor user activities by enabling audit logs in Dataverse. These logs track actions like app launches, data edits, and permission changes. Reviewing these logs helps you identify unusual behaviors and maintain accountability within your apps.
What are Conditional Access Policies, and why are they important?
Conditional Access Policies control how users authenticate based on conditions like location or device type. These policies enhance security by requiring multi-factor authentication or blocking access from untrusted sources, ensuring only authorized users can access your apps.
How can you educate users about data security?
You can conduct regular training sessions focusing on secure app usage, phishing awareness, and password best practices. Interactive activities like quizzes or simulated phishing exercises make learning engaging. Educating users empowers them to recognize and respond to potential security threats effectively.