Microsoft Sentinel vs Splunk: A Security Analytics Comparison
Comparing Key Security Analytics Features
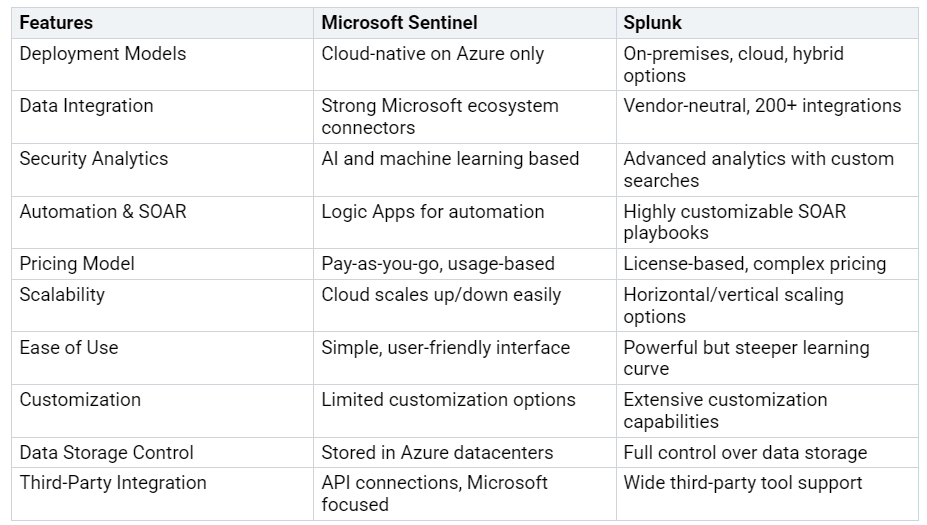
Explore differences between Microsoft Sentinel and Splunk security platforms.
Choosing between Microsoft Sentinel and Splunk depends on what the company needs. Splunk is a leader in SIEM and has strong analytics. It also works with many types of data. Microsoft Sentinel is good for cloud use and works well with Mi…