Your company heavily relies on Microsoft 365, yet its collaboration and data management tools are becoming increasingly complex. With escalating online threats, evolving regulations, and the integration of AI in 2025, robust Microsoft 365 governance is paramount. Proactive planning for Microsoft 365 governance is essential. You need to establish foundational governance guardrails from the outset. These rules ensure security, maintain compliance, and optimize operational efficiency. A well-structured plan prevents future complications. Effective M365 governance is crucial, encompassing guidelines for collaborative efforts. Implement these core principles as your initial Microsoft 365 governance strategy to maximize teamwork effectiveness.
Key Takeaways
Set up strong rules for Microsoft 365 early. This protects your company from online dangers and helps follow important data rules.
Control who can make new teams and sites. Also, use clear naming rules. This stops too much growth and keeps your digital space neat.
Manage who can access your data. Use multi-factor authentication and give people only the access they need. This keeps your information safe.
Know your data and label it. Use rules to stop private data from leaving your company. This helps keep your information secure and private.
Set clear rules for AI tools like Copilot. This ensures they use your data safely and correctly. It also helps you use AI well.
Why M365 Governance Matters
You need strong Microsoft 365 governance. It protects your company. Poor governance causes problems. Good governance helps a lot. It makes your digital space safe. It also makes it work well.
Mitigate Security Risks
Without good Microsoft 365 governance, you face big dangers. Sharing private files too much is common. Bad actors use sharing tools. Settings that allow too much sharing create weak spots. Sharing with outsiders without control is risky. You might see many outside users. You might also see their data in Teams. Bad actors also use old systems. They use wrong settings. Security rules change over time. Not managing them causes problems. This can lead to hacks. Hidden tech is a big worry. Not training staff on security is also a concern. You need strong data protection.
Ensure Compliance
Not following data rules costs a lot. Target paid $18.5 million. This was for a data breach. This shows big fines happen. Bad rules and controls lead to huge fines. You risk data leaks. You can lose trust from customers. Finding old data also costs more. Employees might share private data by mistake. You must follow rules like ISO, HIPAA, and GDPR. These rules keep personal data safe. Strong Microsoft 365 governance helps you follow these rules.
Prevent Sprawl
Too much growth in Microsoft 365 causes sprawl. This wastes money. Companies spend $1,370 per employee each year on software. This is 55% more since 2021. You spend $500 more per employee each year on software. Up to 25% of software licenses are not used. Many people do not use Microsoft 365 fully. This means better rules are needed. A clear plan stops this waste.
Boost Operational Efficiency
Good M365 governance makes your team work better. It lowers IT costs. You save money by using licenses wisely. People find things faster. This makes them happier. Clear rules for teamwork make work smoother. Your plan makes sure everyone follows good ways of working. This makes your digital workplace neat. It also makes it work well. Good teamwork rules make things easier.
Core Policy Guardrails
You need clear rules. Write them down. These rules guide your Microsoft 365. They are your first governance guardrails. They make things consistent. They keep things safe. They make things work well. This is true for all your digital spaces.
Workspace Creation Policies
You must control how people make new workspaces. This includes Microsoft Teams. It also includes SharePoint sites. And Microsoft 365 Groups. Without rules, things get messy. You risk too much growth.
Decide Who Can Create a Team: Make rules for team creation. You can watch a little. Or you can control a lot. This stops too many teams from being made.
Define Approved Purposes for Creating Teams: Set clear reasons for making teams. This makes sure new teams fit your company’s needs. It also helps save money. It lowers risks.
Empty Teams: Make a rule for empty teams. Find them. Then save them or delete them. This uses resources better. It makes work more efficient.
Inactive Teams: Decide what “inactive” means. Check these teams often. Decide what to do with them. This keeps your system neat. It keeps it safe. It makes it work well. This lowers security risks. It saves resources.
Public Teams: Make clear rules for public teams. Have a check-in process. Owners must confirm members often. This makes the company work better. It makes it safer.
Teams with Guest Users: Check guest user access often. Make sure guests only see what they need. This lowers security risks. It stops outsiders from seeing private things.
These rules are a key part of your governance strategy. They keep your collaboration governance strong.
Naming Conventions
Good naming rules help a lot. They make things easy to find. They prevent confusion.
For Microsoft Teams:
Prioritize Shorter Names: Team names show only 30-35 letters. Try to use about 30 letters. This stops names from being cut off. It avoids problems with Microsoft Graph.
Utilize Team Photos: Use a good team picture. This shows what the team is for. Small versions show up in team lists.
Avoid Naming Policy for Prefixes/Suffixes: You often cannot see suffixes in Teams. Prefixes can group things in Exchange. But most teams are hidden from Exchange. Prefixes can take up too much space.
Exclude Dates from Team Names: Dates can make a team name old fast. For talks that have a time limit, use channels. Put dates in channel names instead.
Do Not Include Hyphens or Dashes: These go into the SharePoint site address. They add to the 400-character limit for file paths. Do not use them.
Use Sensitivity Labels: Do not use words like ‘Confidential’ in the team name. Use sensitivity labels instead. These show how private information is. A team’s goal might change.
For SharePoint Sites:
Use Short Names: Shorter names are better. The site name is part of the web address. This adds to a 400-character limit in SharePoint. Long names can cause issues. This happens with many folders.
Consider Email Addresses: The site name affects the Microsoft 365 Group’s email. Keep it short and clear. This makes a friendly email. It is easy to remember.
Avoid Dashes and Apostrophes: Spaces are removed from web addresses. Dashes and apostrophes become part of the address. This makes it longer. It is harder to remember. Do not use them.
Ensure Unique Names: Stop problems. A department might need many sites. For example, ‘HR Team’ for private. ‘HR Department’ for public. Use different names.
Avoid Adding Dates: SharePoint admins can sort sites by when they were made. Dates in site names are usually not needed.
Avoid Keywords that Might Contain Site Attributes: Do not use words like ‘Internal’ in site names. The site’s purpose might change. Its sharing might change. This makes the name wrong.
Avoid ‘Visitors’, ‘Members’, and ‘Owners’: These are official SharePoint roles. They can cause confusion. This happens when setting site permissions.
Remember URL Visibility: The site address is always seen by outsiders. This includes the site name. Be careful what information is in the address.
General Strategies for Microsoft 365 Groups, Teams, and SharePoint Sites:
Define a Clear Structure: Make a clear pattern. For example,
[Department]_[Project]_[Topic]. Like Marketing_Website_Relaunch.Use Short, Concise Names: Aim for less than 30 letters. This stops names from being cut off. This happens in the sidebar.
Utilize Prefixes: Use short codes to show team types. For example,
DEPT_for department teams.P_for project teams.Employ Suffixes: Add endings for more info. This includes region codes (
_DE). Status codes (_ACTIVE). Or priority codes (_P1).Avoid Special Characters or Emojis: Characters like
# % & / \ ? * : < > | – ,cause problems. They can also make searching hard.Ensure Uniqueness: Pick names that are one of a kind. Add location, year, or department if needed. For example, Sales_DACH_Q1_2024.
Use Consistent Terms and Abbreviations: Make and use company-wide short forms. For example, HR for Human Resources. This stops confusion.
Regularly Review Naming Conventions: Check and change rules often. This keeps them in line with company changes. It makes sure people follow them.
Apply to Channels and OneNotes: Use naming rules for channels too. For example,
Project: [project name]. And for OneNotes. For example,[Team name]_Notes.Avoid Common Mistakes: Do not use overly creative names. Do not be inconsistent. Do not miss context. Do not have duplicate teams.
You can make naming rules happen. Use the Microsoft 365 Naming Policy. Admins can set up prefix-suffix rules. They can block bad words in Microsoft Entra ID. For more control, use other tools. These tools offer more features. They let you make many company-specific naming rules. They add custom prefixes/suffixes automatically. They make sure names are the same. This is for SharePoint, OneNote, Planner, and Teams. This is a key part of your microsoft 365 governance.
Acceptable Use Guidelines
You must clearly say how staff can use Microsoft 365. These rules keep your data safe. They make sure you follow rules.
Data Usage Policies: These say how to use data. How to share it. And any limits.
Retention and Deletion Policies: These set rules for data life. And how long to store it.
Security and Privacy Policies: These help follow rules. Both inside and outside the company.
Governance Escalation Paths: These set ways to handle problems. Or when rules are broken.
Companies may ask users to agree to terms. This happens before using some apps. Like Microsoft Admin Portals. This makes sure admins agree to the rules. This is part of their first login. These rules are key for good m365 governance.
Roles and Responsibilities
Clear roles are key for good collaboration governance. You need to know who does what.
Define Your Governance Core Team: Find this team. They make big governance choices. Like setting up things. Naming things. And outside access. Then, make other choices.
Establish a Governance Board or Steering Committee: Get a balanced group of people. They lead how things are done. Give them clear jobs. This makes sure someone is in charge.
Key Roles in Microsoft 365 Governance:
Administration and Governance:
Power Platform admins: Manage Power Platform. Handle security. Check how it works. Fix problems. Keep it healthy. Set up governance guardrails.
Power Platform environment admins: Manage Power Platform environments. Set them up.
Information Governance team: Handle info correctly. Make sure rules are followed.
Information Security and Compliance team: Make sure Power Platform follows rules. And company policies.
Support and Enablement:
Community and enablement leads: Train and help Power Platform users.
IT operations (support): Help with apps and solutions first.
Azure service administrator: Watch over Azure services. This is for the whole company.
Microsoft 365 admin: Help the Power Platform team. Do Microsoft 365 admin tasks.
Other service admins: Manage specific services. Like Copilot, Power BI.
Development and Architecture:
Makers (citizen to pro-devs): Use the platform well. Stay within the rules.
DevOps engineer: Set up and automate software steps.
Enterprise architects: Design Power Platform. Watch over it.
Solution architects: Make solution designs. Use Power Platform. Microsoft 365. And Azure services.
Data and AI:
Data stewards: Keep data good. Keep it safe. Follow rules.
AI strategist: Make AI plans fit business goals.
Ethics officer: Check AI ethics rules. Make sure they are followed.
End Users: Use Power Platform for daily work.
This full plan makes sure your governance strategy covers everything.
Employee Training and Awareness
Your rules work only if staff know them. And follow them. You must train them often. Make them aware.
Create a User Resource Center: Make a central place. For Microsoft 365 help. And training. This helps users use the platform well.
Consider a Microsoft 365 Champions Program: Start a champions program. In your company. This helps people use it. It helps them share knowledge.
Establish Clear Policies and Procedures: Say who can see what data. Explain how to store data. How to share it. Say what is allowed. What is not. Get key people from different teams. This makes rules fit business goals.
Train and Educate Employees: Make sure all staff know your rules. They must know their part. In keeping data safe. And following rules. Train them often. Update them. This keeps them informed. It holds them responsible.
Invest in In-depth Training: Give full training. Cover all of SharePoint. And Teams governance. This includes site management. Content management. Permissions. Access control. Rules. And security. Write down this rule. Make it easy for all to find.
Tailor Training to Your Organization’s Needs: Change training materials. Change sessions. Match them to your needs. And how you use them. This makes learning more useful. More fun. And better.
Identity and Access Management
You must keep your Microsoft 365 safe. Only the right people should get in. This is Identity and Access Management (IAM). It lets only approved users in. It also limits what they can do. Good IAM keeps your data safe. It stops wrong people from getting in. It is a main part of your security plan.
Enforce Multi-Factor Authentication
Add more security to logins. Multi-Factor Authentication (MFA) does this. It asks for more than a password. Users give a second check. This can be a phone code. Or a fingerprint.
Microsoft says MFA stops 99.9% of attacks. This makes your security much better. It makes it harder to get in without permission. This is true even if a password is stolen. MFA stops many password attacks. These include phishing. Also brute force. And credential stuffing. MFA is good at stopping identity hacks in Microsoft 365. Reports show it cuts 99.9% of cyber risk. It needs another check besides a password. This makes it very hard for bad guys to get in. MFA protects against many common attacks. These include:
Phishing emails
Fake business emails
Tricking people
Password spray attacks
Brute force attacks
Using stolen passwords
Weak spots in software
Dangers from working far away
Implement Least Privilege
Limit what users can do. Give them only what they need. This is called least privilege. Users get just enough access. They can do their job. This makes fewer places for attacks. It lessens harm from a hacked account.
Do these things for least privilege:
Find all powerful accounts. This means admin accounts. You see who can get to sensitive data.
Check current access. See who can use apps. Systems. Servers. And devices.
Take away unneeded access. Make sure no one has too many rights.
Watch all accounts with high power. This includes admin accounts.
Give access only when needed. Give just enough access.
Check rights for all apps. Users. And cloud places. Use privileged access management (PAM). This means no constant high access. It makes security better.
Privileged access management (PAM) in Office 365 gives fine control. It is for powerful tasks. It lets users get access just in time. And just enough. This means access is given only when needed. It is taken away when the task is done. This protects important things. It helps follow rules. PAM is ready to use. You need an Azure AD Premium P2 license. This license is also for users. They ask for or answer access requests.
Role-based access control (RBAC) limits user access. It is based on their job in a company. It lets you limit access to certain info. It stops users from seeing other company data. RBAC changes as needed. It is part of free plans. You can use it with Microsoft 365 admin center. And Exchange Online. Give admin jobs and access rights. Base these on set rights in Exchange Online. And Office 365. This is key for user access control.
Control Guest Access
Working with outside people is common. You must manage guest access well. Unchecked guest access is very risky. You need clear rules for outside users.
Here are good ways to set up guest access:
Let guests use only the web. This is for devices not managed by you. It lowers risk. Sensitive files won’t download to unsafe devices. You can set this up. Use Microsoft Entra Conditional Access policy. This is for Microsoft 365 Groups and Teams. You can also set it in SharePoint admin center. This is for SharePoint.
Set a time limit for guests. Guests must log in again after some time. This lowers risk. It stops bad access if a guest’s device is hacked. You set this as a conditional access policy. This is in Microsoft Entra ID.
Make guests use Multi-Factor Authentication (MFA). This is with Conditional Access. It stops attackers from getting into guest accounts. They can’t use stolen logins. It needs a second check.
Use Microsoft Entra terms of use. This is for guests. It makes sure guests agree to your rules. This is before they see shared things. This keeps info private.
A key rule for safe guest access is this. Guests must use only their browser. Stop them from downloading files. This is extra important. It is when guests use their own devices. Or company devices not managed by you. You might not make guests follow managed device rules. But you must not leave their access wide open. You can set this rule in the SharePoint Admin Center. This makes two conditional access policies in Entra. One stops mobile apps and desktop access. It is for compliant or hybrid devices. The other stops browser access for SharePoint Online. It uses ‘app enforced restrictions’.
Other important guest access rules include:
Check Guest Access: Look at guest access often. Make sure guests don’t keep access too long.
Use Sensitivity Labels: Add security labels. This is based on sensitive info types. It manages who sees content.
Make a Managed Guest Area: For partners using Azure AD. Let them sign up for extranet sites or Teams. Use approval steps.
Manage ‘Anyone’ Links: Set end dates. Set default ‘View’ rights for ‘Anyone’ links. This lowers risks. It stops sharing without logging in.
Configure Conditional Access
Conditional Access policies give fine control. It is over how users get to your things. These policies set certain rules. Then they make specific demands. This makes your security better. You can change access. It is based on user. Device. Place. And app.
Common Conditional Access policies make Microsoft 365 safer. These include:
Making admins use multifactor authentication.
Making Azure management tasks use multifactor authentication.
Stopping logins for users. They try to use old login methods.
Needing trusted places for security info sign-up.
Stopping or allowing access from certain places.
Stopping risky login actions.
Needing company-managed devices for certain apps.
Using these access rules is key. It is for strong microsoft 365 governance.
You must keep your data safe. You also need to follow rules. This part shows how to do this in Microsoft 365. Strong data security and information protection are very important.
Data Classification and Labeling
You need to know your data. You need to know how private it is. Data classification helps you do this. It puts your data into groups. This makes it easier to protect.
Here are common ways to sort your Microsoft 365 content:
Confidential: This is for very private data. Think of company secrets. Or money details. It needs strict access. It needs strong security.
Internal: This data is for daily work. It is less private. Only certain staff can see it.
Public: This data is not private. You can share it freely. Marketing papers are an example. It needs little security.
Restricted: This data is between private and internal. It is more private than internal data. It is less key than private data. Only certain people can see it. It needs extra security.
After sorting data, you add sensitivity labels. These labels help protect your info. They make sure of proper information protection.
Using sensitivity labels gives many good things:
You can see how private data is. This is true across your company.
You set protection rules. These match data privacy. These rules stay with the content.
You control who sees content. Encryption for emails helps. It helps for meeting invites. It helps for documents.
You can give special rights to users. Or to groups. You can also set how long these rights last.
You can mark content in Office apps. Use watermarks. Use headers. Or use footers.
You manage info well. This lowers risk. It also helps you show you follow rules.
You add visible marks. These include headers. Footers. Or watermarks. They show who can access.
You control who can open. View. Edit. Print. Or send documents.
You get fine control over content use. Access rules like encryption help.
You give roles like viewer. Editor. Or co-owner. You can set end times. You can also stop actions. Like copy/paste. Or printing.
You keep info safe. You make sure company rules are followed.
You keep data safe in AI talks. For example, Copilot respects sensitivity labels.
You allow labels to pass on. New AI content gets sensitivity labels. This is from its source data.
You make sure user rights are followed. You control access. This stops AI from seeing private data.
You make sure rules are always followed. This is for data security. This applies to all AI talks.
You stop data leaks. You allow safe teamwork.
You protect data early. You use security steps. These include content encryption. And access limits.
You stop outside sharing. You add watermarks. You stop copying. Or downloading private files.
You sort and secure info. This happens its whole life.
You make information governance better. You follow rules.
You lower risks. These include data leaks. And wrong access.
You make data protection easier. Automation helps. Tools like Microsoft Purview help.
You keep data clean. You help AI projects.
You protect and sort Microsoft 365 groups. SharePoint sites. Teams. And other workspaces.
You lower the risk of data leaks. You always use protection rules.
Data Loss Prevention (DLP)
Data loss prevention (DLP) rules are very important. They stop private data from leaving your company. These rules are policies. They work on their own. This is based on certain events. They mainly control content with private info. These rules help you watch security. They help you control it.
Microsoft Purview rules can apply to:
Sensitive Data Types: This includes money. Medical. And privacy data. From many countries. You can also use your own private info types.
Locations: Rules cover Microsoft Exchange Online. Microsoft SharePoint. Microsoft OneDrive. Microsoft Teams. And company computers.
You can make DLP rules. This is in the Microsoft 365 Compliance Center. You can pick from ready-made rules. Or make your own. Ready-made rules cover things like Money. Medical and Health. Or Privacy. You pick a template. Like the US Health Insurance Act for HIPAA. Then, you set the rule name. Description. And services. You also change settings for private info. And protection actions. Last, you pick how the rule runs. Right away. In test mode. Or saved for later.
Custom rules allow more complex rules. You can set conditions. Like ‘Content Contains’ specific private info. You can also set conditions. For ‘Content is Shared outside Microsoft 365’. You can set exceptions. And specific actions for protection.
Microsoft 365 has strong DLP tools. You should know what they do well. And what they don’t.
Here are key points and good ways to use Microsoft 365 DLP:
Built-in Policies: Microsoft Purview has ready-made rules. They protect private data. But they have limits. These limits are in file types. Cloud coverage. And exit watching.
Creating DLP Policies: The Microsoft 365 Compliance Center lets you make rules. Both ready-made and custom rules. They watch and limit data sharing.
Methods to Prevent Incidents: Good data loss prevention includes DLP rules. It also includes ransomware protection. Sharing control. Login control. And shadow IT control.
Methods After an Incident: Data backup. Data keeping rules. And archiving are key. They help you get back data. This is after data loss.
Microsoft Defender and Purview DLP have some limits:
File Type Restrictions: Rules and scanning mostly work. This is for specific file types. These are mainly Microsoft Office documents. Other important company secrets might not be safe. This includes CAD files. Source code. Pictures. And videos.
Limited Cloud Coverage: It covers Microsoft 365 apps. But rules across different clouds can be uneven. This leads to weak spots. Examples include Google Workspace. Or Box.
Insufficient Egress Monitoring: Microsoft Defender works well. This is within its own system. But it might not show you everything. It might not track data movement. This is across devices. Company systems. And other cloud services.
Many companies use other solutions. They add to their DLP plans. These solutions offer more features. They watch everything. This is across different systems.
Retention and Deletion Policies
You need clear rules. For how long to keep data. You also need rules. For when to delete it. These are retention and deletion policies. They are key for information governance. They help you manage data life.
Many laws affect these rules. You must set up Microsoft 365 retention policies. This keeps data. As laws require. These laws include GDPR. HIPAA. And FINRA. This helps you avoid fines. It stops penalties. For not following rules. You must know the rules. For your business. And location. This stops you from deleting needed data by mistake. This makes sure you compliance with regulations.
Data Residency Management
Data residency means where your data is stored. Many countries have laws about this. You must manage data residency well. This is a key part of your microsoft 365 governance.
Microsoft Purview’s compliance boundaries help you manage data. They work across many areas. They follow local rules. These boundaries let you:
Make sure data stays where it should.
Manage and watch data flow by area.
Make sure data use and access follow local rules.
Keep rules the same. This is across different areas.
These boundaries are important for eDiscovery. They make clear lines. They control what data can be searched. They also control who can see eDiscovery cases. This matches data residency laws.
Here are ways to manage data residency:
Classify and Identify Data: Use tools like Microsoft Purview. Copilot for compliance also helps. They find private and personal data. They link it to needed rules.
Define Sovereignty Requirements: Turn country rules into computer rules. Examples include GDPR in the EU. Or local laws for public groups in France.
Apply Automated Policies in Microsoft 365: Set up country controls. Use the Microsoft Purview portal. This stops customer data from leaving certain areas. This applies to SharePoint. OneDrive. And Power Platform.
Enforce Access Controls: Automate permissions. Use conditional access rules in Microsoft. This makes sure only certain people use private data. It makes sure country-specific data access is followed.
Monitor with Dashboards and Alerts: Watch rules all the time. Use automatic dashboards. Get alerts right away for rule breaks. Tools like Microsoft Defender for Cloud Apps show wrong data transfers.
Scale Across Global Geographies: Use automation. This makes rules work across regions easily. It makes sure rules are followed. This is without manual work.
Simplified Compliance: Extending data residency rules to Copilot shows Microsoft cares about rules. And data control.
Enhanced Control: You get more control. Over where Copilot data is. This helps you follow rules.
Transparency and Verification: The Data Location Card in the admin portal shows Copilot residency info. This helps you check rules.
Licensing Considerations: You might need Multi-Geo. Or Advanced Data Residency licenses. This is for users needing storage. Outside your tenant’s area. This makes sure things work well. And follow rules.
Advanced Data Residency (ADR) in SharePoint Online gives you more control. It lets you say where data is. This is at a detailed level. This is for specific tasks. User groups. Or departments. This helps global companies. They need to follow different data residency rules. Examples include GDPR in the EU. Or the Australian Privacy Act in Australia. ADR also lets you move data between regions. This is if business needs. Or rules change. This makes sure it can change. It does not hurt rules. Or data security. This makes it a strong data governance solution.
Collaboration and Content Lifecycle
You need clear rules. These rules are for how people work together. They are also for how content starts and ends. This part helps you set up strong collaboration governance. It makes your digital space neat and safe.
Manage External Sharing
Sharing info outside your company is often needed. But you must control it well. Sharing without control causes big security risks. You can set up safe ways to protect your data.
Restrict Default Sharing Links: Set sharing links to ‘Specific people’. This means only planned outsiders can see things. It stops accidental viewing.
Set Default Permission for Sharing Links: Decide if outside links let people just view or also change things. This stops giving too much power. It helps you control shared content.
Restrict Guest User Invitations in Microsoft Entra: Only let certain people invite guests. Or only admins. Do this in Microsoft Entra’s External collaboration settings. This controls who joins your system.
Prevent External Users from Re-Sharing Content: Change SharePoint’s Site sharing settings. Go to Site Settings. Then Site permissions. Then Change how members can share. Say who can share again. This stops outsiders from giving access to others.
Watermark Sensitive Documents with Sensitivity Labels: Use Microsoft 365 sensitivity labels. These labels add watermarks or headers/footers. They go on private documents. This shows the content is private. It shows who owns it when shared outside. It stops wrong use.
Implement Data Loss Prevention (DLP) Policies: Use DLP policies. These policies check content for private info. This happens before sharing outside. DLP can block, limit, or warn about sharing. This happens if content matches rules. It stops accidental data leaks.
Enable Information Rights Management (IRM): Turn on Azure Rights Management. Set up IRM in the SharePoint admin center. This protects files like PDFs and Office documents. It stops them from being printed, copied, or sent. This is true even after sharing outside. Once on, use IRM for certain SharePoint lists and libraries. This controls rights. Like stopping printing or sending.
Implement MFA for Guest Access Using Conditional Access: Make guest users use multi-factor authentication (MFA). This adds more security. It makes sure that even if guest logins are stolen, bad people cannot see shared content. They need a second check.
Govern Teams and Site Provisioning
You need a clear way to make new Teams and SharePoint sites. This stops too much growth. It keeps your system neat. Automated tools help you manage this well.
You can use different tools to make new workspaces automatically:
Forms: People fill out a form. This is to ask for a new workspace.
Bots: Chatbots help people ask for a workspace.
SPFx solutions: Special web parts in SharePoint offer a request screen.
Custom websites or APIs: Build your own place for requests.
Azure Functions: Computer code handles the background work for making things.
Logic Apps: Cloud tools make tasks happen automatically.
WebJobs: These run background tasks in Azure App Service.
PnP Provisioning Engine: Use code templates. This is for SharePoint.
SharePoint site templates: These are ready-made designs for new sites.
Microsoft has tools to make Teams and SharePoint automatically:
Teams templates: Use ready-made or custom templates. These set up channels and apps.
SharePoint templates: Use ready-made designs. These are for lists, libraries, look, and navigation.
Naming policies and blocked words: These rules make workspace names standard.
Group creation restrictions: These rules say who can make new workspaces.
Power Automate can make things automatically by:
Approval workflows: Certain people approve requests.
Notifications and reminders: Automatic emails or Teams messages happen in SharePoint.
Integration with other Microsoft services: Workflows connect with PowerApps, Forms, Planner, or other tools.
Other tools, like Teams Manager, offer combined making, collaboration governance, and automation. They have features like:
Template management: Make, manage, and use templates. This is with central control and syncing.
Automated approval workflows: Check and approve requests. This is with automatic workflows.
Advanced governance integration: Manage naming rules, life cycle, or extra info.
Implement Lifecycle Management
Teams and SharePoint sites have a life. They are made, used, and then stopped. You must manage this whole process. This stops too much cloud growth. It makes your information governance better.
You should:
Develop governance policies: Teach users about making teams. About naming rules. And about sorting data. This stops copies. It makes finding things easy.
Manage team changes: Plan for staff changes and new jobs. This stops teams from being left alone. It keeps security.
Implement expiration policies: Set end dates for Microsoft 365 Groups and Teams. This controls cloud growth. It makes collaboration governance better. It makes things clearer.
Leverage automation tools: Use tools like Teams Manager. These make tasks easy. Like finding unused teams. And making life cycle rules happen.
Establish clear policies for concluding a team’s lifecycle: Set end dates. Explain how to keep and save content.
Define team purpose and creation processes: Use collaboration governance rules early. These include naming rules and access control. Start life cycle plans from the start.
Monitor team usage: Make reports. Find unused or forgotten teams. This is for getting them back or restarting them.
Define post-purpose actions for teams: Use saving rules. Manage content keeping. This is at the end of a team’s life.
When managing team changes, you should:
Plan for each life stage.
Make teams with templates.
Watch and control activity.
Stop unused teams.
Include important people.
For expiration policies, you should:
Set end dates for groups and teams.
Tell owners before deleting.
Manage related data.
Check outside users.
For end-of-life management, you can:
Choose to save or delete unused teams.
Change to private channels if some work is left.
Combine teams.
Check and reuse ownership.
These actions reduce cloud growth. They make collaboration governance better. This is by following data keeping rules. They also make things clearer. This is by helping track teamwork and user access.
Control Content Versioning
Versioning helps you track file changes. It lets you get back older versions if needed. This is a key part of content governance. You need to set up versioning correctly. This is in SharePoint Online libraries.
SharePoint Online libraries have versioning on by default. They save 500 versions for files. And 50 for lists. It is best to keep versioning on. This helps with things like working together. You should only turn it off for special reasons. Usually, this is with code.
You have two main choices for versioning settings:
Automatic (Microsoft Recommended): This setting smartly changes version limits. It removes old versions. This is based on how old they are. This helps save storage. Microsoft says automatic settings can save 96% storage. This is over six months. This is compared to limits based on number. This works for Office files. It does not work for files like PDFs. New updates make whole new versions for them.
Manual: This choice lets admins set exact limits. This is for major versions. You can also set both end dates and number limits.
You can set versioning limits at different levels:
Organization-level: As a SharePoint or Global admin, sign in to the SharePoint admin center. Go to Settings > Version history limits. Choose Automatically. Then save and confirm. You can also do this with code. By default, SharePoint Online saves 500 versions for files. Older versions delete automatically. This happens when the limit is hit. These better controls only work for new OneDrive accounts. Or SharePoint document libraries. They do not change old ones. Site owners can change them.
Site-level: SharePoint admins can change company-wide limits. This is for certain sites. They use code. To turn on automatic version limits for all document libraries on a site, use code. For new document libraries only, add a command. For old ones, use another command. To set manual controls, use code.
Library-level: You can set specific version history limits. This is for single libraries. These change site settings. Do this with code. This is for automatic settings. Site owners can also turn on automatic versioning. This is through SharePoint document library settings. Go to Settings > Library Settings > More library settings > Versioning settings. Then choose Automatic under ‘Version time limit’.
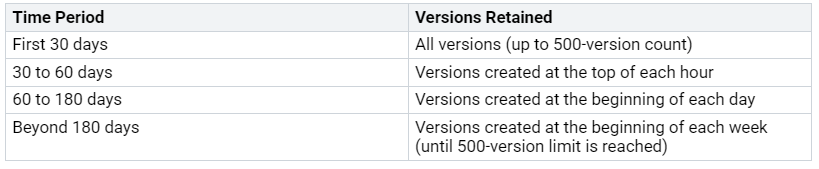
When using automatic versioning, SharePoint keeps versions based on a time plan:
Think about storage use. All versions use SharePoint storage. For example, a 10 MB file. If only small changes are made, it will use 20 MB. This is 10 MB for the first file. Plus 10 MB for the changed file. Be careful with storage limits. This is especially true with big files like 300MB PDFs. 500 versions could quickly go over site limits.
You should not upload PST (mail archive) files. Do not put them in OneDrive for Business. Or SharePoint Online team site document libraries. They use a lot of storage. If uploaded, versions are kept for 30 days.
AI and Copilot Governance
Adding AI tools like Copilot to your Microsoft 365 brings new powers. It also brings new problems. You must set clear rules for AI and Copilot use. These rules keep things safe. They follow rules. They help use AI well. This part shows how to set these rules.
Establish Data Access Policies
You must make sure Copilot only sees data users can see. Microsoft 365 Copilot uses your current permission rules. It stops data leaks. This is between users, groups, and tenants. Copilot only shows data you can access. It uses the same rules as other Microsoft 365 services. The Semantic Index honors user access. This makes sure it only sees content the user can view.
Microsoft 365 Copilot respects your rights. This is when Microsoft Purview Information Protection encrypts data. These rights come from sensitivity labels or IRM. Customer content is kept separate. This is within each tenant. It uses Microsoft Entra and role-based access control. Microsoft uses strong physical safety. It does background checks. It uses many layers of encryption. This keeps data safe. This is when it is stored and moved. Encryption can also stop program access to content. This limits Copilot agent access.
You need strong ways to log in. This way cannot be broken by guessing passwords. Your system checks login tries for risk. It asks for more things if needed. You should check who can access user accounts. This stops sharing too much. Microsoft 365 E3 has Microsoft Entra ID P1 licenses. These licenses suggest common Conditional Access rules. For example, ask for MFA for admins and all users. Also, block old ways to log in. For mixed logins, use Microsoft Entra Password Protection. This finds and blocks weak passwords. Microsoft 365 E5 has Microsoft Entra ID P2 licenses. These licenses suggest Conditional Access rules. For example, ask for MFA if login risk is medium or high. Also, ask high-risk users to change their password. This is if they do not use passwordless login.
Microsoft 365 Copilot sees content and context. It does this through Microsoft Graph. It makes answers based on your company data. This includes documents, emails, calendar, chats, meetings, and contacts. Prompts, answers, and data from Microsoft Graph do not train Large Language Models (LLMs). This includes those used by Microsoft 365 Copilot. Copilot only shows company data you can at least view. You must use permission rules. These are in Microsoft 365 services. SharePoint is one example. This makes sure the right users or groups can access content. This includes permissions for teamwork tools. Like shared channels in Microsoft Teams.
You can limit company-wide search and Copilot to certain SharePoint sites. This is a short-term fix. It helps you check and set permissions. SharePoint has built-in controls. For example, use ‘Specific people links’. Do not use company-wide sharing by default. Hide broad permissions. Like ‘Everyone Except External Users’. Let site admins stop members from sharing. SharePoint Advanced Management has data access reports. These reports find content that might be overshared or private. Restricted Content Discovery flags sites. This stops users from finding them. This is through Copilot or company search. It does not change current permissions. SharePoint Advanced Management lets you make a rule for inactive sites. This rule automatically manages inactive sites. SharePoint Advanced Management also lets you limit access to OneDrive sites. It limits access to users in a certain group. This uses the restricted access control rule. Microsoft Purview can use sensitivity labels with encryption. This limits Copilot’s access to files. You need EXTRACT and VIEW rights. Data Loss Prevention (DLP) for Microsoft 365 Copilot stops access to content. This is content with certain sensitivity labels. These steps are vital for strong microsoft 365 governance.
Define Use Cases and Scope
You need to say how staff can use AI help. Set clear rules for Copilot use. Teach staff what is okay to use. Work with IT and compliance teams. Set up ways to watch and fix problems. Use Microsoft’s admin tools. These tools help you check Copilot’s outputs.
Companies face three problems with Copilot. First, access control. You must decide who can use Copilot. And how much. Second, data safety. You must make sure private information protection is not misused. Third, checking outputs. You must have ways to check AI-made content. Do this before sharing outside. Key ways to secure and manage Copilot are to focus on data safety. Also, risk management. And using AI well. Use Microsoft Purview for this. Protect private data. Use Microsoft Purview information protection for sorting and labeling. Use Data Loss Prevention (DLP) rules. These rules stop sharing private content. Watch and manage risks. Turn on Insider Risk Management. This finds risky actions. Use Communication Compliance. This checks AI-made content for bad words. Manage AI talks. Check Copilot prompts and answers. Use Purview eDiscovery and Audit Logs. Use Compliance Manager for rules and ethics. Use Data Lifecycle Management for keeping and deleting. Check permissions. This stops oversharing or wrong access. This full plan makes your m365 governance stronger.
Implement Data Discovery and Classification
Finding and sorting data is key. It makes Copilot better and safer. By sorting and labeling data well, you can automatically remove old or useless files. This is from Copilot’s answers. This makes Copilot’s answers much better. It makes them more correct. It lowers the chance of ‘hallucinations’. These are wrong facts. From a safety view, sorting helps lower risks. These risks come from content with too many permissions. By sorting data correctly. And by using a ‘least privilege’ access rule. You can limit Copilot’s access to very private information protection. This lowers the chance of private data being seen. It makes sure you follow data safety rules.
Finding and sorting data is basic. It affects how well and how safe Microsoft Copilot is. For how well it works, controlling data quality helps stop ‘hallucinations’. These are wrong answers from LLMs. By making sure Copilot uses good, new data. And by making prompts clear. You can make AI-made content more reliable. For safety, sorting is vital for risks. Like ‘over-permissioned content’. If permissions are too wide, Copilot could accidentally show private information protection. Using a ‘least privilege’ access rule. This is based on correct data sorting. It limits Copilot’s access to very private files. This stops data leaks. It makes sure rules are followed. Microsoft Purview tools. With sensitivity labels and Data Loss Prevention (DLP) rules. They help with this management.
You should make Data Loss Prevention (DLP) rules. These are for files and email. Make rules for how long to keep data. Keep needed data. Delete unneeded data. Use content explorer to check items. These are items with sensitivity labels. Or retention labels. Or marked as private info. With Microsoft 365 E5, make sensitivity labeling wider. This is to protect more content. This includes SharePoint sites and Teams. Use container labels. Also, label items automatically. Make DLP rules work in more places. Use more ways to find private information protection. Automatically add retention labels. This is when private info is found. This is for items needing different settings. Or more management. Use activity explorer. And all of content explorer’s features. This helps you understand private data and its labels.
Promote Responsible AI Practices
You must encourage using AI well with Microsoft Copilot. This means following key ideas.
Fairness: Give code ideas that are fair. Make sure AI treats all users fairly. Give code ideas that are always fair. This is no matter who they are. Key goals are steady ideas. Less bias. And helping people without being unfair. This means checking training data. Testing with different groups. Making bias less. Watching how it works. And having ways to change things.
Reliability and Safety: Make sure answers are sure and safe. Make sure AI systems always work as expected. Make risks small. Do this by testing hard against strange cases. Make it strong against bad inputs. Follow safe coding rules. Good ways include checking code automatically. Testing with bad data. Safe software making steps. Being strong against attacks. And designs that work even if parts fail.
Privacy and Security: Keep code and user data safe. Protect user data. Do this by using encryption. And hardware security modules (HSMs). Ways include getting clear permission for data. Only get data that is needed. Watch inputs for privacy. Use encryption when data moves. And when it is stored. Use ways to hide who people are. Like changing names. And grouping data.
Inclusiveness: Let all developers use it. Make sure AI helps everyone. This is no matter their ability. Or where they are. Or who they are. Copilot helps with access features. It works offline. It changes to local coding ways. Focus areas include helping developers with problems. Give modes for slow internet. Get ideas from many groups. Add ways to check across groups.
Transparency: Build trust. Show how AI models make choices. Copilot gives explanations you can use. It has tools to fix problems. It has dashboards to see where ideas come from. Main parts include clear ways it works. Explain design choices. Talk openly about what it can do. And what it cannot. Keep records of what happened.
Accountability: Keep management. And fix problems fast. Say who is clearly in charge of AI results. You should set jobs. Watch how the system works. Do checks. Fix harms fast. Good ways include management plans. Checking risks all the time. Planned safety, privacy, and ethics checks. Plans for what to do if AI acts wrong.
Secure Power Platform Deployments
Power Platform works with Microsoft 365’s advanced information protection. And compliance tools. It uses the same strong safety system as Azure. Built-in features in the Power Platform admin center. And Managed Environments. They help you set rules. Tools like Microsoft Purview for Power Platform. Built-in data rules. Tenant separation features. And examples like the CoE Starter Kit are there. These make sure safety rules are followed. And compliance needs are met.
You must set rules. Use your safety plan. This sets and manages rules. And a management plan for Power Platform work. These rules make sure needed safety settings are used. Technologies. And actions. They make risks and rule-breaking small. Say and write down specific safety settings for each item. Make templates. Or automatic ways to use them everywhere. Think about company-wide, specific resource, and specific work settings. Say what role-based access control (RBAC) and multifactor authentication (MFA) needs are. Write down ‘just enough access’ for each item. Follow the rule of least privilege. Set clear ways to make rules happen. Say what happens if safety rules are not followed. Make people and teams responsible for keeping safety standards. Watch all the time. Check how well the safety plan works. Do this by watching. Make ongoing improvements. Include ideas for data safety. And network safety within the plan.
Managed Security brings all features together. These features keep low-code apps, agents, and automations safe. Safety posture management gives smart advice. This advice is for strong safety that can grow. Better identity and access management makes sure only allowed users access certain things. Features include IP firewall. IP cookie binding. And conditional access for single Canvas Apps. Data safety and privacy offer strong controls. These controls keep private information protection secret and correct. AI-powered threat protection works with Microsoft Sentinel. This is for finding and fixing suspicious actions fast.
Watching and Checking for Microsoft 365 Governance
You need to watch your Microsoft 365. This makes sure your governance guardrails work. Watching and checking are key. They keep things safe. They help you find problems fast.
Use Audit Logs
You must use audit logs. These logs write down what users do. They show who did what. They show when. You can find these logs. They are in the Microsoft Purview compliance portal. Use them to check strange actions. For example, see if someone looked at private files. Audit logs help you track changes. They show changes to rules. They also show changes to access. This data is key for safety checks.
Set Up Security Alerts
You should set up security alerts. These alerts tell you about big events. For example, set alerts for odd logins. You can also get alerts for big data downloads. Microsoft Defender for Cloud Apps helps you make these alerts. Fast messages help you act quickly. This makes threats less harmful.
Use Compliance Reports
You need to use tools for compliance reports. These tools help you show you follow rules. They show you follow company rules. The Microsoft Purview compliance portal has many reports. These reports cover data rules. They also cover compliance management. You can make reports on how long data is kept. You can also report on Data Loss Prevention (DLP) rule breaks. These reports are key for checks. They show you care about data safety.
Plan Regular Checks
You must plan regular checks. This is for your governance setup. This is not a one-time job. Check your rules often. Check your settings. Make sure they still fit your needs. Look at audit logs. Look at alert summaries. This helps you see patterns. It also helps you find ways to do better. Regular checks make your microsoft 365 governance stronger. They keep your system safe and working well.
You must set up these basic rules. They are for Microsoft 365 in 2025. They are the strong base. This makes your digital work safe. It follows rules. It works well. These first steps keep you safe. They stop common mistakes. They help you use all of M365. This includes new AI tools. Your overall governance strategy will get stronger. Your collaboration governance will too. Remember, Microsoft 365 governance keeps going. It is not a one-time thing. Put these key rules first. This is your most important first step. Good M365 governance starts here. Good collaboration governance starts here. Use these rules right away.
FAQ
What are governance guardrails in Microsoft 365?
These are basic rules. They are also policies. You set them up. They keep your Microsoft 365 safe. They make sure you follow rules. They stop too much data growth. They make work better from the start. Think of them as key safety steps.
Why should I set up governance guardrails first?
Setting rules first stops problems later. You avoid safety risks. You avoid fines. You stop data from growing too much. Good rules early make your digital work safe. It follows rules. It works well. It saves time and money later.
How often should I review my Microsoft 365 governance policies?
You should check your rules often. Tech, dangers, and rules change a lot. Plan to check them every three or six months. This makes sure your rules still work. They should fit your changing business needs.
Can AI tools like Copilot function effectively without governance?
No, AI tools like Copilot need strong rules. Without them, you risk data leaks. You risk breaking rules. Rules make sure Copilot uses data safely. It respects who can see what. It helps use AI well. It keeps your private info safe.