I use Microsoft Defender for Cloud because it gives me one place to manage security across Azure, AWS, and Google Cloud. Every week, I see thousands of threats, from ransomware to phishing and cloud misconfigurations. Ransomware attacks now disrupt 86% of businesses, and AI makes phishing even harder to spot. I rely on Microsoft Defender to replace old tools, improve compliance, and protect my growing cloud workloads as threats keep getting more complex.
Key Takeaways
Microsoft Defender for Cloud protects all your cloud resources in one place, covering Azure, AWS, and Google Cloud.
It helps detect threats like ransomware and phishing early, using tools like Secure Score and real-time alerts.
The platform offers strong features such as Cloud Security Posture Management and workload protection to keep your cloud safe.
Multi-cloud support and automation simplify security management and speed up response to attacks.
Starting with the free tier lets you explore security basics before upgrading to advanced protection.
Microsoft Defender Overview
What It Is
When I first started using Microsoft Defender, I wanted a tool that could protect all my cloud resources in one place. Microsoft Defender is a security platform that helps me monitor, protect, and respond to threats across my cloud environments. It works with Azure, AWS, and Google Cloud, so I do not have to switch between different tools. I can see security alerts, get recommendations, and track my progress with Secure Score.
Here is a table that shows some of the main features I use every day:
I also like that Microsoft Defender gives me continuous security posture monitoring, compliance checks, and even helps me spot risky code before it goes live. I can set custom security policies and use machine learning to catch unusual behavior.
Who It’s For
I have seen that Microsoft Defender works well for many types of organizations. Large companies use it because they have lots of cloud resources and need strong protection. Industries like healthcare, government, and finance rely on it to meet strict security rules and keep sensitive data safe.
Here is a quick look at who benefits most:
Even though big companies lead the way, I find Microsoft Defender helpful as an individual or in a small team. It gives me the same advanced tools that large organizations use, so I can protect my cloud workloads with confidence.
Threat Landscape
Ransomware Trends
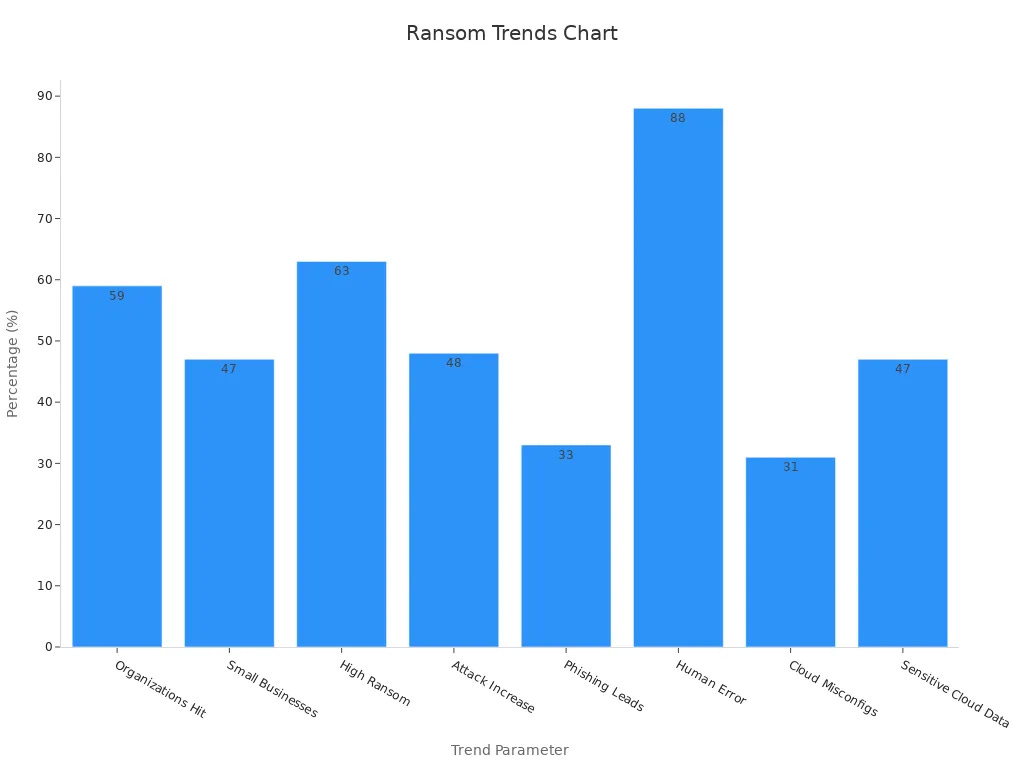
When I look at the current threat landscape, ransomware stands out as one of the biggest dangers to cloud environments. I see that attackers target both large companies and small businesses. Ransomware attacks have increased by 48% according to IT professionals, and 59% of organizations faced at least one ransomware attack last year. The financial impact is huge, with projected annual costs reaching $265 billion by 2031. Attackers do not just go after big companies. Nearly half of the victims have less than $10 million in revenue.
I notice that most ransomware attacks start with human mistakes or misconfigurations. In fact, 88% of data breaches come from human error, and 31% of cloud breaches happen because of misconfigured settings. Attackers also exploit known and zero-day vulnerabilities, making it important for me to keep my systems updated and patched. Ransomware groups often demand high ransoms, with 63% asking for $1 million or more.
Here is a table that summarizes some key trends:
Phishing and Credential Attacks
Phishing attacks have become more advanced and frequent. I have seen a 703% surge in credential phishing attacks in the second half of 2024. Attackers use spear phishing in 65% of cases, and almost 71% of targeted attacks start with a phishing email. These emails trick users into giving up their passwords, which leads to cloud account takeovers.
More than half of organizations report phishing as the main way attackers steal cloud credentials. About 68% see cloud account takeovers as a major risk. Attackers now target online communication platforms and social media, making it easier for them to reach users. In my experience, once attackers get credentials, they can access sensitive data and move through cloud environments quickly.
Here are some important statistics:
🛡️ I always remind my team that strong passwords, multifactor authentication, and regular training are key to stopping these attacks.
Key Features
CSPM and CWPP
When I started managing cloud security, I quickly realized that two features made the biggest difference: Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP). These tools help me keep my cloud environment safe and healthy every day.
CSPM checks my cloud settings and finds weak spots before attackers do. It scans for misconfigurations, missing updates, and risky permissions. CWPP protects my workloads, like virtual machines and containers, by watching for threats in real time. I get alerts if someone tries to break in or if a container acts strangely.
Here’s what I notice with these features:
I see real-time monitoring and alerts for suspicious activity in my cloud apps and infrastructure.
The system checks containers and Kubernetes for privilege escalation or unauthorized access.
File integrity and network activity are tracked, so I know if something changes unexpectedly.
I use dashboards and reports to hunt for threats and respond quickly.
Automated security checks help me stay compliant with standards like CIS and PCI DSS.
🛡️ I trust CSPM and CWPP because they give me visibility and control. I can spot risks early and fix them before they become real problems.
Secure Score
One of my favorite tools in Microsoft Defender is the Secure Score. This score shows me how strong my cloud security is at any moment. When I make improvements, like turning on multi-factor authentication or adding endpoint protection, my Secure Score goes up.
I use the Secure Score dashboard to track my progress over time. It helps me see which actions matter most. For example, enabling data encryption or setting up identity management gives my score a big boost. I also compare my score to similar organizations, which motivates me to keep improving.
Organizations that use Microsoft Defender see their Secure Score rise as they add critical security controls. This leads to fewer cyber incidents, better compliance, and smoother business operations. I have noticed that focusing on Secure Score helps me reduce risk and keep my cloud environment safe.
MITRE ATT&CK Integration
I rely on the MITRE ATT&CK framework inside Microsoft Defender to understand how attackers think. This framework breaks down cyberattacks into steps, called tactics and techniques. When I get an alert, I can see exactly which stage of an attack is happening.
This mapping helps me:
Analyze threats using a common language.
Find gaps in my defenses and fix them fast.
Respond to incidents more quickly because I know what to look for.
By using MITRE ATT&CK, I move from reacting to threats to hunting for them. My team and I work better together because we all understand the same attack patterns. This approach leads to faster resolutions and stronger defenses.
Multi-Cloud Support
My cloud setup includes Azure, AWS, and Google Cloud. Managing security across all these platforms used to be hard. Now, with Microsoft Defender, I get a single dashboard that shows me risks and alerts from every cloud.
Here’s how multi-cloud support helps me:
I set up consistent identity and access rules across all clouds, which reduces vulnerabilities.
Automated security checks run on each platform, so I catch issues early.
I see all my sensitive data, no matter where it lives, in one place.
I use built-in dashboards to track trends and spot risks across clouds.
Regular testing and unified policies help me prevent attackers from moving between clouds.
🌐 With multi-cloud support, I feel confident that my security is strong everywhere—not just in one cloud.
I also use integrations with SIEM tools, workflow automation, and attack path visualization. These features let me connect alerts to my incident response system, automate fixes, and see how attackers might move through my environment. This makes my security operations faster and more effective.
How It Works
Integration and Automation
When I set up Microsoft Defender, I noticed how much easier my daily work became. The platform lets me automate many security tasks that used to take hours. For example, I can set up workflow automation to handle repetitive jobs like responding to threats or syncing data between systems. I use integrations with third-party services, such as ApiX-Drive, to connect different tools without writing a lot of code. This helps me keep my security operations agile and efficient.
I often schedule vulnerability scans during off-peak hours. This way, my systems stay protected without slowing down important business tasks. I also fine-tune detection settings to focus on the most critical resources. By doing this, I make sure my team gets alerts that matter most, and we avoid wasting time on low-risk issues. Automation reduces manual work, improves our response times, and keeps our security posture strong.
💡 Tip: Automating routine security tasks frees up my time so I can focus on bigger threats and strategy.
Dashboards and Alerts
The dashboards in Microsoft Defender give me a clear view of my entire cloud environment. I see real-time event reports and alerts as soon as something suspicious happens. This helps me catch threats early and respond before they become bigger problems.
Here’s how dashboards and alerts help me work faster and smarter:
I get instant alerts for high-risk incidents, so I can act quickly.
Centralized dashboards show all my security data in one place, making it easy to spot patterns.
I customize alert thresholds to reduce false alarms and focus on what matters.
Automated responses kick in for certain threats, which speeds up recovery.
Machine learning helps prioritize alerts, so my team always knows where to look first.
Customizable widgets let me adjust the dashboard to fit my needs. This makes it easier to make quick decisions and keep my cloud secure.
Getting Started
Free Tier
When I first tried Microsoft Defender, I started with the free tier. This option gave me a quick way to see my cloud security posture without any cost. I enabled it directly from the Azure portal. I just searched for "Defender for Cloud," selected my subscription, and clicked "Enable." The free tier provided security policy management, basic security assessments, and a Secure Score overview. I could see which resources needed attention right away.
The free tier also let me explore recommendations for improving my security. I liked that I could test these features before making any commitment. If I wanted to try advanced protection, I could activate the 30-day free trial for enhanced security plans. This trial unlocked extra features like threat detection, just-in-time VM access, and multi-cloud support.
💡 Tip: I always recommend starting with the free tier to get a feel for the dashboard and see where your biggest risks are.
Upgrading and Best Practices
After using the free tier, I decided to upgrade for more advanced features. The upgrade process was simple. I chose the resources I wanted to protect and selected the right Defender plan. The enhanced features helped me detect threats faster and automate responses.
For onboarding, I followed these steps:
I reviewed the default security policies and adjusted them to match my organization’s needs.
I set up alerts for critical resources.
I used the Secure Score dashboard to track my progress.
To improve my Secure Score, I focused on high-impact actions. I enabled multi-factor authentication, encrypted my data, and fixed misconfigurations. I also scheduled regular reviews to keep my security posture strong.
🚀 Starting with Microsoft Defender’s free tier and following these steps helped me build a strong foundation for cloud security.
I trust Microsoft Defender to keep my cloud environments secure. It automatically finds sensitive data across Azure, AWS, and Google Cloud, and uses attack path analysis to spot risks before they become problems. I use the Secure Score to check my security posture and follow the recommendations to improve. I suggest starting with the free tier to see how it works. Next, I plan to use Cloud Security Explorer and continuous monitoring to protect my data even more.
FAQ
How do I enable Microsoft Defender for Cloud?
I open the Azure portal, search for "Defender for Cloud," and select my subscription. I click "Enable" to start. The setup takes just a few minutes.
Can I use Microsoft Defender for Cloud with AWS and Google Cloud?
Yes, I connect my AWS and Google Cloud accounts directly. Defender for Cloud then monitors and protects resources across all my cloud platforms in one dashboard.
What is Secure Score, and why does it matter?
Secure Score shows how strong my cloud security is. I use it to track improvements, find weak spots, and compare my security to others. A higher score means better protection.
Does Microsoft Defender for Cloud help with compliance?
Absolutely! I use built-in compliance checks and policy recommendations. Defender for Cloud helps me meet standards like CIS, PCI DSS, and more.
How does Microsoft Defender for Cloud alert me about threats?
I get real-time alerts in the dashboard and by email. I can also set up automated responses. This helps me act fast when something suspicious happens.