In today’s online world, comprehensive security and management in Microsoft 365 are very important. You face more threats now. Microsoft 365 services were part of 22% of break-ins through SharePoint. They were also part of 17% through Outlook in early 2024. Using real accounts caused 35% of cloud problems during this time. Knowing the tools you have and using good practices is key. This helps protect your organization from these changing dangers.
Remember, working together on comprehensive security makes your defenses stronger against today’s tricky cyber threats.
Key Takeaways
Turn on Multi-Factor Authentication (MFA) to lower the risk of unauthorized access. This extra security can stop about 99.9% of automated attacks.
Use a Zero Trust Model to make sure users only see what they need for their jobs. This method treats every access request as untrusted.
Use Data Loss Prevention (DLP) rules to watch and control how sensitive information is shared. This helps stop accidental data leaks.
Give regular security awareness training to employees. This training can lower the chances of breaches caused by human mistakes, which make up to 95% of incidents.
Use a proactive threat detection plan with tools like Threat Explorer. Fast detection and response can greatly reduce the risk of data breaches.
Microsoft 365 Security Overview
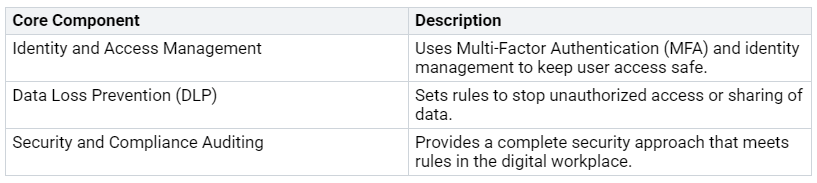
Microsoft 365 uses a combined security plan. This plan has different tools and features to keep your organization safe. It focuses on three main parts:
Identity and Access Management: You can keep user access safe with Multi-Factor Authentication (MFA) and strong identity management.
Data Loss Prevention (DLP): DLP rules help stop unauthorized access or sharing of sensitive data.
Security and Compliance Auditing: This complete approach meets rules and makes sure your organization follows important standards.
A combined security system in Microsoft 365 greatly improves how you find and respond to threats. By using different security tools together, you make managing cyber threats easier. This teamwork gives you better visibility and quicker response times. It also cuts down on alert fatigue, which is a common problem with separate solutions.
With a united approach, you can see a great return on investment. Studies show a 242% ROI over three years, along with big improvements in alert fatigue and stronger security.
Remember, a strong security plan not only keeps your data safe but also builds trust in your organization. Using Microsoft 365 security tools as connected parts will help you respond well to new threats.
Comprehensive Security Features
Identity and Access Management
Good identity and access management is very important for strong security in Microsoft 365. You can use many features to improve security and keep sensitive information safe. Here are some key parts:
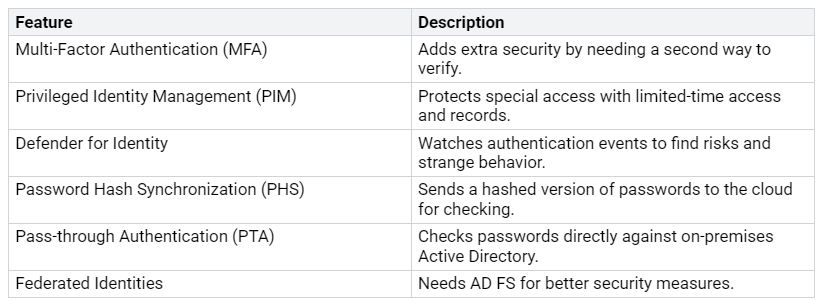
Multi-Factor Authentication (MFA): This feature adds extra security. It needs a second way to verify, like a fingerprint or a one-time code. MFA can stop about 99.9% of automated attacks. This greatly lowers the chance of unauthorized access.
Privileged Identity Management (PIM): PIM protects special access. It allows limited-time access and needs approvals for higher permissions. This makes a record of activated access, ensuring responsibility.
Defender for Identity: This tool watches authentication events. It finds login risks and strange behavior. By fixing possible threats early, you can make your organization’s defenses stronger.
Password Hash Synchronization (PHS): PHS sends a hashed version of passwords to the cloud for checking. This helps with cloud-based identity checks.
Pass-through Authentication (PTA): PTA checks passwords directly against on-premises Active Directory. It does not store user passwords in the cloud. This is good for organizations needing stricter rules.
Federated Identities: This feature needs Active Directory Federation Services (AD FS). It is best for large companies needing better security, like smart cards or fingerprint checks.
Data Protection and Compliance
Data protection is very important in Microsoft 365 security. The platform has many ways to ensure it follows major rules like GDPR and HIPAA. Here are some key features:
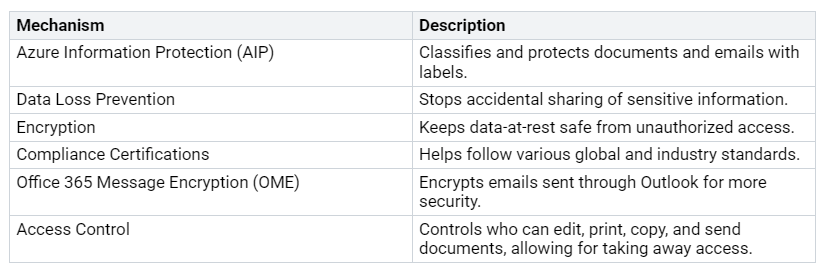
Azure Information Protection (AIP): A cloud solution that classifies and protects documents and emails with labels. This keeps sensitive information safe.
Data Loss Prevention (DLP): DLP helps stop the accidental sharing of sensitive information. By setting DLP rules, you can watch and control how data is shared in your organization.
Encryption: Microsoft 365 automatically encrypts data-at-rest. This stops unauthorized access. It is very important for keeping sensitive information safe from breaches.
Compliance Certifications: Microsoft has many global, regional, and industry certifications. This shows a commitment to keeping high standards of data protection.
Office 365 Message Encryption (OME): This feature lets users encrypt emails sent through Outlook. This adds extra security to email communications.
Access Control: Administrators can control who can edit, print, copy, and send documents. This ability lets you take away access when needed, improving data protection.
By using these comprehensive security features, you can greatly improve your organization’s security posture. Microsoft 365 gives you the tools needed to protect sensitive data and follow regulatory rules.
Security Best Practices for Microsoft 365
To keep your Microsoft 365 environment safe, you should follow some important practices. These practices improve your security and help reduce risks from user mistakes and wrong settings. Here are some key security best practices to use:
Enable Multi-Factor Authentication (MFA): This important security step needs users to give more than one way to confirm their identity. MFA can greatly lower the chance of unauthorized access.
Implement a Zero Trust Model: This method treats every access request like it comes from an untrusted network. It makes sure users have only the access they need for their jobs.
Use Mobile Device Management (MDM): MDM tools help keep mobile devices safe and manage them when they access company data. This lowers risks from lost or stolen devices.
Activate Security Defaults: This feature sets up key security settings automatically to improve protection against unauthorized access.
Establish Secure Password Policies: Require strong passwords and regular changes to boost security. This helps stop unauthorized access from weak passwords.
Conduct Regular Security Awareness Training: Teach your employees to spot and deal with security threats well. Human mistakes cause 68%-95% of data breaches, often from user actions like clicks or misplaced trust. Regular training can help lower these incidents.
Remember, up to 95% of breaches are due to preventable human errors. Investing in training is key to reducing risks.
Besides these practices, organizations often make common mistakes when using Microsoft 365 security. Here are some traps to avoid:
Ignoring misconfigurations in OneDrive, SharePoint, and Teams.
Not enforcing Multi-Factor Authentication (MFA) properly.
Keeping default settings in Entra, Exchange Online Protection, and calendars that create risks.
Overlooking the hidden dangers of Bring Your Own Device (BYOD) and unsecured mobile access.
Forgetting about conditional access policies.
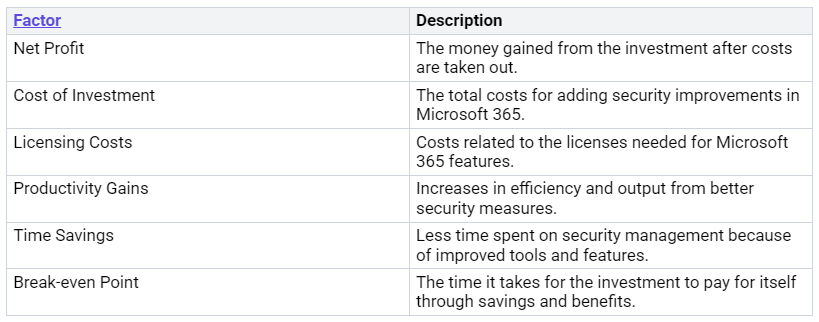
To check how well your security improvements are working, think about these factors:
By following these security best practices and investing in training, you can greatly improve your Microsoft 365 security. A proactive approach not only protects your organization but also builds a culture of security awareness among your employees.
Threat Management in Microsoft 365
Managing threats well is very important for keeping Microsoft 365 safe. By using smart threat detection and strong response plans, you can make your organization’s security much better.
Proactive Threat Detection
Proactive threat detection tools in Microsoft 365 help you find new threats before they get worse. Some key tools are:
Threat Explorer: This tool lets you see malware found by Microsoft 365 security. You can also check harmful emails and phishing URL data.
Real-time Detections: This feature gives quick alerts about possible threats, so you can act fast.
With these tools, you can usually detect threats in just 15 minutes and fix them in about 30 minutes. This quick response helps lower the chance of data breaches and improves your overall security.
Also, platforms like Vectra AI use advanced Attack Signal Intelligence™ to find unknown attackers. They give insights into the first signs of hybrid cloud problems, using parts of the MITRE D3FEND framework for strong threat detection.
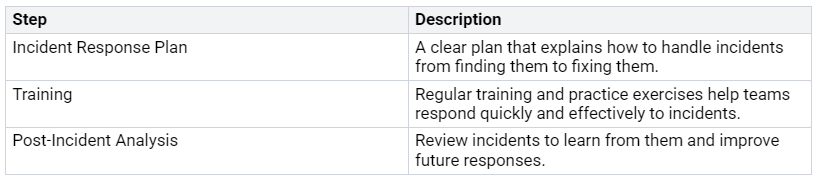
Incident Response Strategies
When a security problem happens, having a clear incident response plan is very important. Here are some steps to improve your response and fixing efforts:
Invest in a Multi-layered Security Strategy: This method makes sure you have many defenses ready.
Conduct Regular Phishing Simulations: These drills help your team learn to spot and react to phishing attempts well.
Provide Ongoing Security Training: Teach your users about possible threats and how to deal with them.
Post-incident analysis is key for learning from problems. It means going over what happened and finding the main causes. This helps you write down incidents well and strengthen defenses for the future.
By using these proactive detection tools and response strategies, you can greatly lower the risk of data theft and reduce the overall costs linked to security problems.
Governance and Compliance in Microsoft 365
Good governance and compliance are very important for organizations using Microsoft 365. You must manage data carefully while making sure your organization follows the rules. A strong governance plan acts like a guide for managing data from start to finish. It shows how to handle different types of organizational data through rules, processes, roles, and responsibilities.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is an important feature in Microsoft 365 that helps stop unauthorized access to data. By setting up roles and permissions, you can make sure users have the right access based on their jobs. Here are some key benefits of using RBAC:
Minimized risk of data exposure: RBAC limits access to only the information needed for each role, lowering the chance of sensitive data being seen by the wrong people.
Simplified permissions management: Grouping permissions by roles instead of individuals makes it easier to manage who can access what and reduces mistakes.
Support for compliance requirements: RBAC helps you follow rules by giving structured access control and keeping track of actions.
A good way to manage permissions is to divide them based on roles. This leads to fewer global administrators and better protection for your Microsoft 365 environment. Allowing local administrators can save time and money, making IT work more efficiently.
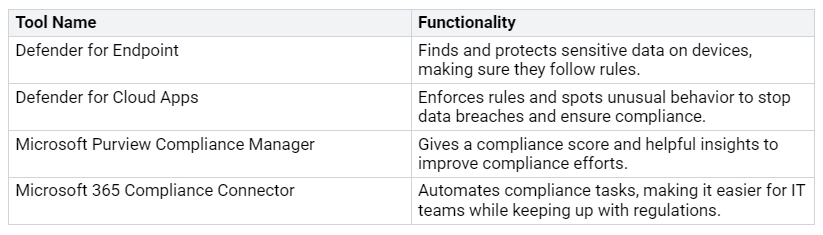
Compliance Monitoring Tools
Microsoft 365 has many compliance monitoring tools that help your organization meet regulatory needs. These tools help you keep governance in check and follow necessary rules. Here’s a table that summarizes some key compliance monitoring tools:
Using these tools helps you perform security checks and follow rules like HIPAA and PCI DSS. Setting up compliance settings early during migration can improve long-term safety and lower risks.
By using RBAC and compliance monitoring tools, you can build a safe environment in Microsoft 365. This method not only protects sensitive information but also encourages a culture of responsibility and compliance in your organization.
To keep your Microsoft 365 environment safe, you need a complete plan. Focus on managing identities and access, protecting data, and following rules. Using role-based access control (RBAC) improves security by giving admin rights based on job duties. Companies like Peters & Associates have used Microsoft security tools to make their IT consulting better.
Ongoing security training is very important. Programs like Evolve 365 and ONLC Microsoft Security Training offer helpful resources to keep security high. Regular training keeps you and your team aware of possible threats and good practices.
By using these strategies, you can lower risks and make your Microsoft 365 environment secure.
Remember, taking action today helps create a safer tomorrow.
FAQ
What is Multi-Factor Authentication in Microsoft 365?
Multi-Factor Authentication (MFA) adds extra security. It needs users to confirm their identity in two or more ways. For example, they might use a password and a code sent to their phone. This greatly lowers the chances of unauthorized access.
How does Microsoft Defender for Office 365 enhance security?
Microsoft Defender for Office 365 protects against threats like phishing and malware. It uses smart algorithms to find and block harmful emails and attachments. This keeps your organization’s data safe.
Why is identity management important in Microsoft 365?
Good identity management makes sure only authorized users can access sensitive information. By using strong authentication methods like MFA, you can lower the risk of data breaches and follow regulations.
What are the benefits of using Microsoft 365 for compliance?
Microsoft 365 has built-in compliance tools that help you meet rules. Features like data loss prevention and compliance monitoring make it easier to keep data secure and follow industry standards.
How can I improve my organization’s security posture in Microsoft 365?
To boost your security posture, turn on Multi-Factor Authentication, provide regular security training, and use Microsoft Defender for Office 365. These steps help protect against threats and ensure you follow security policies.