Intune is crucial for device management and security. However, its effectiveness hinges on proper configuration. Many Intune administrators make common errors. For example, application deployment issues on Android devices are frequent, leading to significant operational disruptions. These top mistakes diminish Intune’s utility, create security vulnerabilities, and can lead to compliance breaches. Overlooking updates on non-Windows devices is another common oversight. Furthermore, difficulties with basic reporting can compromise your organization’s security posture and regulatory adherence. This guide aims to equip all administrators with the knowledge to avoid these critical missteps.
Key Takeaways
Plan your Intune setup carefully. Start with a small test group to find problems early.
Protect your company’s data. Use strong security rules and check them often.
Test apps before giving them to everyone. Use managed app stores for better control.
Watch your Intune system all the time. This helps you find and fix problems quickly.
Bad Planning and Design
Many big mistakes happen because of bad planning. You need a clear plan for Intune. If you don’t plan well, you will make expensive mistakes. Things will get messy. You might not notice until it’s too late. Without a good plan, your Intune setup can grow too big. No one will know who is in charge. You might miss problems like old devices. Or policies that don’t work together.
No Step-by-Step Rollout
Not rolling out Intune in steps is a common error. Always start with a small group. These are your test users. Watch how much work the helpdesk has. See if people can sign up easily. Check if users can work well. Make sure their data is safe. Doing it in steps stops big problems. It lowers risks during setup. It also helps you make smart choices. You can see if apps work together. This helps you roll out Intune in an organized way.
Unclear Company Needs
Unsure Who Owns Devices
You need to know who owns devices. Do this before you set anything up. Mixing up users and devices causes confusion. This can lead to rule problems. It makes managing devices hard. Figure out if devices belong to the company. Or if they are personal. This helps you set the right rules. It makes sure you control your devices properly.
Common Intune Deployment Mistakes
Many admins make mistakes. They do this during Intune deployment. You might set up policies once. Then you forget them. This means you don’t see problems. You miss issues with compliance. Or app deployment errors. Another mistake is turning off ESP. ESP helps users. It helps fix problems. These common mistakes hurt your Intune setup.
Skipping Conditional Access
You might skip Conditional Access. This is a big security risk. Conditional Access protects your stuff. It lets only trusted users in. It lets only trusted devices in. They can get to company data. Without it, your security is weaker.
Weak MFA Configuration
A weak MFA configuration causes problems. Attackers can get past MFA. Intune certificate mistakes can happen. Bad identifiers let regular users get more power. This is an ESC1 attack. It happens in Active Directory. This shows bad MFA setup. It lets people get more power. This is through a bad part of your Intune setup.
Ineffective Compliance Policies
Bad compliance policies cause issues. If a device is not compliant, Conditional Access can block it. You might see ‘Sign-in error code 53000’. This means your device is not compliant. This can stop Windows upgrades. It can also stop a device from becoming compliant. Assigning compliance policies to device groups is bad. It should be user groups. This can make the ‘system account’ non-compliant. Devices might stay non-compliant. This happens until a user checks access. Intune can act on noncompliance. It can send alerts. It can send emails. You can also lock devices. Or remove them. These actions warn users. Or they protect data.
Ignoring Conditional Access Integration
You should link Conditional Access with other services. This makes a strong defense. It works with endpoint security. It works with data loss prevention. This helps you see everything. It helps make rules the same. This makes your security stronger. Linking also helps meet rules. Like GDPR. It makes things better for users. Trusted users get easy access. Stricter rules apply to strange actions. Linking with Microsoft 365 helps. Like Microsoft Defender. It helps make rules happen. It gives full security view. This supports zero-trust ideas. Using MFA and SSO helps. It stops security problems. It also makes things easier. Conditional Access checks device compliance. It makes sure only safe devices get data. It works with Azure AD Identity Protection. This gives real-time risk tools.
App Management Mistakes
Good app management is key. It makes Intune work well. But many admins make big mistakes. These mistakes can cause problems. They can make your data unsafe. They can make things work slowly. Users will have a bad time. You need to plan app management well. You need to do it right.
Untested App Deployments
You often put out apps. You do not test them first. This is a big error. Untested apps make more work. This is because of manual steps. They also have more errors. These errors happen when you put them out. Apps will not be the same. They will be different on your devices. For example, you put out MSI Line of Business Apps. You do not wrap them. You do not think about them. This often causes problems. Always test apps. Use a small group first. Then put them out to everyone.
Missing App Protection
You might forget app protection rules. This leaves your company data open. Intune helps keep your data safe. It controls how apps use private info. It stops data from leaking. It stops bad sharing. You must set up these rules. They make sure company data is safe. This is true even on personal devices. It is safe inside managed apps.
Neglecting Managed App Stores
You should use managed app stores. These are like Apple Business Manager. Or Google Play for Work. Not using them is a lost chance. These links offer big benefits. They give strong data safety. They give good access control. Intune lets you manage app settings. It lets you manage updates. This makes sure employees use the newest apps. They use the safest apps. The Intune admin center links to the public Play Store. It also syncs with a Managed Google Play account. This lets you get Android Enterprise apps. This includes private apps. This link makes it easy. It helps put out different app types. Do not add too many apps to Intune. Do not make them ‘required’. Make them ‘available’ in the Company Portal instead. This can make your setup slow. It can make the user experience slow.
Security Baseline Oversights
You need to set up strong security rules. Many forget these important settings. This leaves your company open to danger. You must know the risks. You need to set things up correctly.
Default Security Settings
Using the default security settings is a common error. These settings often do not fit your company’s needs. A bug in Microsoft Intune can even change your special security rules. It sets them back to default during updates. For example, an update from 23H2 to 24H2 might erase your custom settings. This means your special security rules are gone. You then have to put them back yourself. This makes your devices less safe for a time. Microsoft says this is true. Your custom settings are lost when you update to newer versions. This problem changes settings back to Microsoft’s defaults. This makes your security weaker.
Inconsistent Baselines
You might have different security rules. This causes big problems. Not having the same policies everywhere makes security messy. This makes things riskier. It also makes managing rules harder. It is tough to decide which alerts are important. Choices are made without good information. SaaS management tools help here. They make sure rules are followed. They ensure security checks are the same. They constantly check devices against rules. They point out any mistakes. Automated fixes bring bad systems back in line. This means fewer human errors.
Missing Device Restrictions
You must put in place proper device limits. Not doing so causes serious security issues. If you do not block bad devices, they can get to company stuff. This means people can get in without permission. Devices that are not safe can still connect. Not stopping personal devices from joining your MDM lets non-company devices onto the network. These devices skip your company’s security rules. You also need clear steps to follow. These steps let you erase devices and apps from far away. This is key when someone leaves. It is also key if a device is lost or stolen. Without these steps, private data can be easily stolen. You must set up device compliance policies for all types of devices. If not, devices are not watched all the time. Those not meeting rules might not be quickly marked as bad. This makes security risks higher.
Update Management Errors
You must manage device updates well. Many admins make big mistakes here. These mistakes can make your systems weak. They can also stop people from working. You need a clear plan for updates.
Neglecting Windows Update for Business
You might forget Windows Update for Business. This is a big mistake. Intune puts all your update tasks in one place. It uses one cloud system. This makes setting things up easy. It puts updates on all your devices. This means you do not need old WSUS servers. It makes things faster and bigger. Intune makes sure your devices get the newest security fixes. It also gives new features automatically. This makes your system safer. It helps you follow rules. Automatic updates stop you from missing important fixes. These could let bad people in. You must update your Intune rules often. Companies often set rules. Then they do not check them. They do not update them as Intune changes. This leads to old settings. It makes them use old ways to fix things. These ways are not needed anymore. This makes your system work badly. You can manage all parts of Windows OS updates well. Use Windows Update for Business with Intune. This mix makes sure devices always online get the newest security updates and Windows features. Intune is the main place for these settings.
Untested Update Rollouts
You might put out updates. You do not test them first. This is a common mistake. Waiting too long to release updates makes you very open to danger. For example, waiting more than 2-3 days makes you more open to hackers. Intune lets you set up update rules. You can set how long to wait. You can use update groups. You can also stop updates. Update groups help you put out updates slowly. You can set them based on what devices do. Use pilot, test, and main groups. This makes things less risky. You can wait on quality and feature updates. This lets you check if things work together. Do this before putting them out widely. Deployment groups help put out feature updates in steps. This lets IT fix problems.
Poor Update Monitoring
You might not watch your updates well. This causes problems. Not setting Active Hours well means updates do not install at the best times. Set Active Hours to let updates install. Do this at the start and end of the workday. For example, 9 am-3 pm for an 8 am-4 pm workday. Not using the ‘Deadline’ option for restarts stops fast installs. This is true even when you put out updates faster. Intune has Delivery Optimization. This tech lets devices share files. Devices on the same local network share update files. This means they do not need to download from Microsoft’s servers many times. Intune lets you set Delivery Optimization rules. You can control how much internet is used. You can limit downloads to the local network. You can pick between CDN or peer sources. This saves internet use in big companies. Fixing things well needs constant watch.
RBAC Mistakes
RBAC helps keep Intune safe. Bad RBAC settings make big security holes. You must say who can do what. Wrong settings can let people change things. Or steal data.
Too Many Admin Rights
Giving too many rights to an admin is a big mistake. This makes your security risk much higher. Attackers often use high-level rights. They use them to put in bad software. Or steal private data. They can also turn off safety tools. More than 90% of Windows problems come from local admin rights. Getting into a local admin account lets an attacker move around your network. This can cause a lot of harm. Attackers use special tricks. They use stolen passwords from local admin accounts. This helps them move around. Especially if you use the same password everywhere. Bad software often needs high rights to get in. If a user has local admin rights, bad software can run with full power. This puts your company at risk of bigger attacks. Local admin access lets hackers get around important safety settings. They can delete system records. Or pretend to be other users. They can run bad code or tools. This gives them access to private data. Attackers can also add bad software to existing apps. These apps run with system power. Like tasks that run on a schedule. They can then run quietly.
Unclear Admin Areas
You must clearly say what each admin can handle. Without clear areas, admins might change settings by mistake. This causes confusion. It can make the system unstable. An admin for device rules should not see app settings. Not unless they need to. Clear areas stop bad things from happening by accident.
Not Checking Roles Often
Not checking your RBAC roles often is another common mistake. Jobs change. People leave. If you do not update rights, old workers might still have access. Or people in new jobs. This creates extra security risks. You should check your Intune roles often. This makes sure rights are right and safe.
Monitoring and Reporting Gaps
You use Intune to manage devices. You also use it to keep them safe. But many admins forget to watch and report. This means you do not see problems. You cannot fix what you do not see. If you do not watch, you miss important warnings. You miss when rules are broken. You miss when things do not work well. This makes fixing problems hard. It leaves your system open to danger.
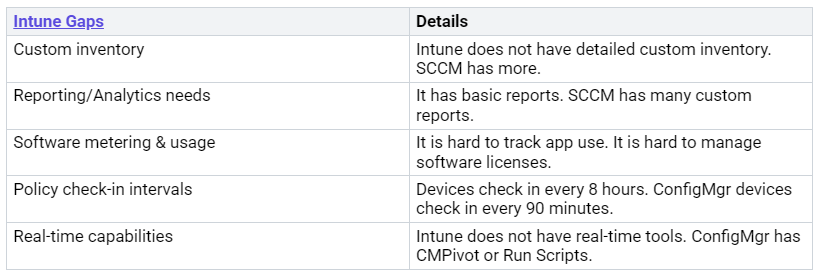
Underutilized Intune Reports
You might not use all of Intune’s reports. This means you miss important facts. These facts are about your devices. Intune gives basic reports. But it does not have all the details.
These gaps mean you might not see everything. You need to know these limits. Then you can find other ways. You can get the data you need.
No Compliance Alerts
You must set up alerts. These are for when rules are broken. If you ignore these alerts, you will not know. You will not know when devices break rules. This creates big security risks. You might see:
BitLocker or Defender rules quietly failing
Old or duplicate device records. They make the count too high.
App deployment errors piling up
Certificates expiring. This causes access problems.
Forgetting to watch Apple certificates is common. This stops services from working. Without quick alerts, you cannot act fast. This leaves your data open. You need strong alerts for rules. They tell you right away. They tell you when a device fails. It fails to meet your safety rules. This helps you stay safe.
Unclear Troubleshooting
Bad watching leads to unclear fixing. When a problem happens, you do not have the facts. You cannot fix it fast. You spend more time guessing. You spend less time fixing. This hurts users’ work. It also stresses your IT team. Clear reports and alerts help. They give you the facts you need. They help you find problems fast. This helps you fix problems well.
Intune Setup Best Practices
Comprehensive Planning
You must plan carefully. Do this before you start Intune. This is very important. Know your goals clearly. Understand what your company needs. Think about who owns devices. Think about who uses them. Roll out Intune in steps. This is another good idea. Start with a small group. This helps find problems early. Good planning stops many mistakes. It builds a strong base for Intune. You should also map your current systems. Think how Intune will work with them. Write down your choices. This saves time and money later. It makes things go smoothly.
Strong Security Posture
You need strong security. Make strong rules. These rules control who can get in. They make sure devices follow rules. Set up Conditional Access. This keeps your data safe. Strong MFA is also key. Check your security settings often. This keeps security high. These good practices protect your system. They guard against dangers. Do not use default settings. Change them for your risks. This active approach protects data. Use security baselines. They help make devices safer.
Continuous Optimization
Your Intune needs constant care. This is a key practice. Check your rules often. Change them as your company changes. Watch compliance reports. Fix devices that do not follow rules fast. Stay updated on new Intune features. Use them to make your setup better. Constant work keeps Intune good. It keeps your security strong. Also, ask users what they think. Use it to make your settings better. This ongoing work helps you change. It helps with new needs. Plan regular checks of your settings. This finds problems before they get big.
You have learned about common Intune setup mistakes. These errors hurt your security. They hurt how well things work. They hurt following rules. Setting up Intune well is a long trip. It needs careful planning. It needs watching all the time. It needs changes when needed. Use these ideas. Build a strong and safe system. This is for managing phones and apps. Every admin can set up Intune well. This helps you be a better admin.
FAQ
How can you avoid common deployment mistakes?
You must plan your Intune setup well. Start with a small test group. This helps you find problems early. Always check your rules. Make sure they fit your company’s needs. Do not skip Conditional Access. It keeps your data safe.
What is the best way to manage app deployments?
You should always test apps. Do this before you give them to everyone. Use managed app stores. Apple Business Manager is one. This gives you more control. It also makes things safer. Put apps out as ‘available’. Do this in the Company Portal. This stops slow setups.
How do you ensure strong security baselines?
You must change security settings. Do not use the default ones. Check your security rules often. Make sure they are the same on all devices. Put in place good device limits. This stops people from getting in without permission.
Why is continuous monitoring important for Intune?
Watching all the time helps you find problems fast. It makes sure devices follow the rules. You can find security risks. Do this before they get big. Use Intune reports. Set up alerts for rules. This keeps your system safe and working well.