It’s a challenge to maintain robust security while simultaneously ensuring a seamless user experience, especially within the context of hybrid work in 2025. Traditional security protocols often prove overly restrictive, hindering productivity. This issue is evident in the fact that 61% of businesses report an increase in security incidents directly attributable to hybrid work. Furthermore, 40% of employees struggle with remote access, and while nearly 64% of organizations embrace hybrid models, their security frameworks frequently fall short. This inadequacy leads to a concerning 65% of employees bypassing security measures, creating significant vulnerabilities. The critical question then becomes: how can companies achieve stringent security while fostering user satisfaction, particularly when considering Microsoft hybrid work security? Even Microsoft’s own recommendations may not fully address these complex challenges; a dedicated focus on securing hybrid work environments is paramount.
Key Takeaways
Old security methods do not work for hybrid work. People work from many places. They use many devices. This makes old security weak.
Your identity is the new security border. Zero Trust means you check every access. This helps keep your data safe.
AI and automation make security stronger. They find threats fast. They fix problems quickly. This helps your team work without trouble.
Good security training is important. Easy-to-use tools help your team. Clear talks about security updates also help.
You can have strong security without making users mad. Focus on smart ways. Make them fit users. This helps everyone work well.
The Shifting Landscape of Hybrid Work Security
Perimeter Security’s Limitations
Old security ways do not protect you. This is true for hybrid work in 2025. The idea of a “safe” inside network is gone. The “unsafe” outside network is also gone. Your staff logs in from many devices. They often use public Wi-Fi. This makes it easy for attackers to get in. Your data is now in many places. It is on cloud services. It is on personal devices. You do not fully control these. This makes your network weak. If one device is hacked, attackers can move freely. This raises your risk of ransomware. Public Wi-Fi is not safe. It can lead to “Man-in-the-Middle” attacks. Attackers can steal your private data. You also have issues with personal devices. These devices are not watched. They do not get updates. Your rules may not cover them. Home networks are often weak. They are easy targets. Watching staff outside the office is hard. This means less watching. Data can leak out. This shows old security has limits.
User Frustration and Shadow IT Risks
Security rules can be too strict. This makes users unhappy. They look for easier ways to work. This leads to “Shadow IT.” Shadow IT means staff use unapproved software. They also use unapproved cloud services. These tools often skip your main login. They skip your device protection. They do not have strong security. Users might put private files on these tools. This creates big security holes. It also makes it easier for attacks. For example, 65% of remote staff use unapproved tools. About 11% of cyber attacks come from Shadow IT. Many companies do not check for Shadow IT risks. This makes them weaker. It is hard to make staff follow security rules. Shadow IT also causes rule problems. You can get big fines. This happens if data leaks through unapproved apps. Your security rules must change.
Identity as the New Security Perimeter
How you do hybrid work security has changed. Cloud computing changed things. SaaS apps changed things. APIs changed things. Old network borders are gone. Every device is a way in. Every place is a way in. So, your identity is the new security border. Attackers now go after user identities. They steal login info. They use fake emails. They trick people. These attacks get past old network defenses. Identity-first security looks at who you are. It does not just look at where you are. This helps you control access. It makes logging in easier. It also helps you follow rules. Zero trust rules are key here. You must always check every access request. This includes requests from inside your network. This puts identity at the center of security. Your zero trust plan needs strong rules.
You need a new way to do security in 2025. Zero Trust is that way. It is key for Microsoft hybrid work security. This idea means we trust no user. We trust no device. We trust no app by default. You must check everything. Microsoft’s Secure Future plan focuses on your devices. It also focuses on endpoints. Zero Trust helps make your security modern. It works well for hybrid setups. It makes your hybrid work security strong. It does not slow down your team.
AI and Automation for Secure Hybrid Work
You can make your security stronger. Use AI and automation. These tools help protect your company. They do not bother your team. They find threats fast. They fix problems quickly. This is key for secure hybrid work.
Proactive Threat Detection with Defender XDR
Microsoft Defender XDR finds threats. It finds them before big damage. It shows you your whole system. This includes emails and devices. It includes user identities. It also includes cloud services. Defender XDR connects different threats. It finds patterns. Other tools might miss these. This makes checks faster. It makes them easier. You spend less time switching programs. You can focus on key issues.
Defender XDR brings alerts together. It gets info from many services. This gives you a full picture. You can respond well. This helps remote teams. It helps cloud systems. It helps follow rules. It watches your emails. It watches documents. It finds bad emails. It finds hacked accounts. It finds common attacks. It can block senders. It can quarantine messages. It watches your endpoints. These are computers and phones. It sees what threats do. It sees how they spread. It can stop attacks. It can restore files. For apps, it stops attacks. It stops them on cloud systems. It stops them on servers. It stops key processes. On your network, it checks traffic. It looks for strange events. It finds weak spots. It finds unmanaged devices. It sends alerts fast. For identity, it finds attacks. It finds them based on user accounts. It sees strange user actions. It combines login data. It uses device info. This stops attackers. You can add your own threat info. This helps protect against known attacks. Defender XDR uses smart machine learning. It uses AI. It finds complex attacks. Old security methods miss these. It looks at patterns. It looks across different areas. It can spot phishing emails. These lead to cloud access. They lead to stolen identities. These are used to take data. It helps you stop hacked systems. It blocks bad files. It checks identities. It protects you from malware. It protects from ransomware. It protects from other threats. It works across endpoints. It works across networks. It works across cloud. It works across email.
Automating Security Workflows with Sentinel
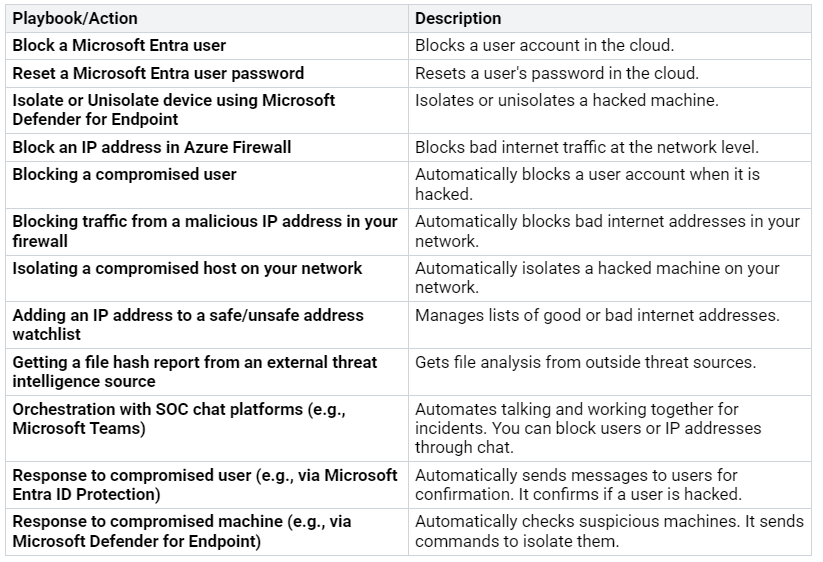
Microsoft Sentinel helps automate security tasks. It uses SOAR. SOAR means Security Orchestration. It means Automation. It means Response. This makes fixing incidents smoother. SOAR playbooks are like automatic lists. They do repeated tasks for you. This lets your security team focus. They focus on harder threats. You can change these playbooks. They can start automatic actions. This happens when a security incident occurs. For example, a playbook can stop a hacked system. It can block bad internet addresses. It can also send alerts to your team.
Sentinel uses Logic Apps. This tool helps it respond. It can automatically turn off hacked accounts. It works in the cloud. It works on your systems. Sentinel’s automation rules start these workflows. No one has to do it by hand. It creates a full automatic system. This Logic App connects cloud systems. It connects your own systems. It uses Microsoft’s tools. This makes sure hacked accounts are off everywhere. This starts when Sentinel finds a new incident. It involves a user account. Automated incident response stops threats fast. It works well with Azure Logic Apps. SOAR gives you custom workflows. This makes response times faster. It reduces manual work. AI helps make your SOC better. It saves money. It speeds up how you respond. It responds to cyber threats. It helps your team focus. They focus on what matters. Generative AI helps you check faster. It summarizes incidents. It creates search questions. It suggests next steps. This makes analysts better. It also gives useful threat info. It uses Microsoft’s big threat data. This helps your SOC find threats. It helps investigate. It helps respond faster.
Here are some examples of what Sentinel can do:
Sentinel can also reset a password. It resets an Azure AD user password. This happens if an account is hacked. It can block an AD user. This happens if they try to log in too many times. These actions stop security breaches. These security solutions help you stay protected.
User Behavior Analytics for Anomaly Detection
UBA tools help find strange actions. They find them by your team. These tools learn what is normal. They learn for each user. They use data analysis. They use basic methods. They look at numbers. They find patterns. They also use advanced AI. They use machine learning. AI and machine learning look at much data. They create exact models. These show how users act. They get better over time. This happens as your business changes. They learn about single users. Like where they log in. Or when they use apps. They also learn about groups. Like who uses databases. UBA can combine activity. It combines from many user accounts. It makes one identity. This helps it find patterns. It finds them across your network.
After UBA learns what is normal, it watches users. It compares what they do now. It compares to their normal actions. If someone does something very different, it might mean a threat. UBA sends alerts. It sends them to your security team. It uses rules you set. For example, if someone tries to get to something. Something they should not. It sends an alert. AI and machine learning find strange actions. They look for things that are different. Different from a user’s past actions. For example, logging in at odd times. They can also compare a user’s actions. They compare to their teammates. For instance, if a marketing person looks at credit card records. You can add threat info to UBA. This teaches it to spot known bad activities.
Streamlining Incident Response
UBA helps find key signs of trouble. It finds them in your hybrid work security. It spots things like many failed logins. Then a successful one. It sees logins from strange places. Or strange devices. It also notices if an account. One not used for long. It suddenly becomes very active. These are signs of a hacked account. UBA can also find if an employee is stealing data. Or using it wrongly. For example, if an employee uses files. Files they never used before. Or if they copy data. They copy to a personal drive. Or if they email sensitive documents. They email to a personal address. This is true after a bad work event.
UBA also finds if someone with special access. They do things they should not. For example, a system admin. They look at finance records. Or they create new user accounts. They do it without permission. It can spot if a user account tries to get to many servers. Or databases. Ones it has not used before. Or if it uses strange computer commands. These are signs of someone moving around. Moving inside your network. UBA can also find if someone is taking data. Taking it out of your company. This happens if a user downloads much data. Or puts files into archives. This is different from their normal actions. UBA can find red flags. For example, an employee downloads much sensitive data. At 2 AM. From a device you do not know. This happens even if their login details are correct. UBA looks at when you access things. What device you use. Where you are. Your normal patterns. This helps it find small strange actions. Actions that happen before big security problems. This makes your secure hybrid work environment safer.
Cultivating a Security-Aware Culture
Engaging Security Training for Hybrid Teams
You need to make your team part of your security solution. Start with good training. Your training should be specific to your company’s risks. Use different ways to teach. This helps everyone learn. Hold regular sessions to keep your team updated on new threats. Always ask for feedback to make training better. Avoid long, boring sessions full of tech words. Employees learn best from engaging, interactive content, not just one-time lectures. You can use live learning tools like Microsoft Teams. You can also offer self-paced learning with videos and quizzes. This mix works well for hybrid teams. Good training really helps. Cybersecurity awareness training led to a 70% drop in security risks in 2023. People who learn about phishing are 30% less likely to click bad links. This shows training makes a big difference for your security.
User-Friendly Security Tools and Self-Service
Give your team tools that are easy to use. User-friendly security tools help your employees work better. They reduce tech problems and data loss. This lets your team stay focused. Tools like password managers make security simple. They create strong passwords and fill them in for you. They also check for weak passwords. These tools give you insights without invading privacy. Self-service options also empower your users. They can reset their own passwords or unlock accounts. This means they do not need to call IT for every small issue. For example, some password management solutions cut help desk calls by up to 85%. This frees up your IT team. It also makes your employees feel more in control.
Clear Communication for Security Updates
Always tell your team clearly about security updates. Explain why changes are happening. Tell them how these changes affect their work. Use simple language. Avoid jargon. Make sure everyone understands what they need to do. This builds trust. It also helps your team follow new rules.
Feedback for Continuous Security Improvement
Ask your team for their thoughts on security. Collect feedback often. You can use surveys, support tickets, or direct talks. This helps you see what works and what does not. Filter all feedback into a system. This helps you see common issues. Then, act on what you learn. Tell your team what changes you made based on their ideas. This “closing the loop” makes your security better. It also shows your team you value their input. This leads to a stronger overall security posture.
You can have strong Microsoft hybrid work security. It will not make users mad. Good security helps people. It does not hold them back. Focus on smart ways. Make them fit users. Use identity as the main security. Follow Zero Trust rules. Use Zero Trust everywhere. Add AI to find threats. Use automated security tools. This Zero Trust way makes hybrid work safe. It also helps people work together. This makes hybrid work good for all.
FAQ
What is hybrid work security?
Hybrid work security keeps your company safe. It protects your data. Your team works from many places. They use different devices. You need strong security for all.
Why is traditional security not enough for hybrid work?
Old security focuses on your office. Hybrid work means your team works anywhere. Old ways cannot protect all new ways to log in. You need a new plan.
What is Zero Trust in Microsoft environments?
Zero Trust means you trust no one. You check every request to get in. This is for people, devices, and apps. Microsoft tools help you do this.
How does AI help with hybrid work security?
AI finds dangers faster. It does security jobs automatically. This means less work for your team. AI helps find strange user actions. It makes your security better.
How can you make security user-friendly?
Offer tools that are easy to use. Give clear training. Let people fix small problems themselves. Listen to what your team says. This helps everyone be more secure.