Deploying custom copilots in a secure and effective manner is crucial for organizations today. Balancing innovative ideas with risk management enables you to harness the power of AI while safeguarding your data. A staggering 73% of companies reported experiencing at least one AI-related security issue last year. To encourage broader user adoption of AI, emphasize job security and present AI as a means to enhance job performance. Robust management systems facilitate rapid innovation without compromising security.
“Organizations that hesitate to embrace Microsoft Copilot due to security concerns are falling behind. Recent studies indicate that companies utilizing AI tools like Copilot complete tasks 26% faster and achieve 44% greater accuracy in security operations.”
Key Takeaways
Use Role-Based Access Control (RBAC) to manage user permissions well. This stops unauthorized access and makes security better.
Use Multi-Factor Authentication (MFA) to keep sensitive data safe. MFA can stop up to 99.9% of account hacking attempts.
Set up strong data rules to follow privacy laws like GDPR and CCPA. This helps keep personal data safe and builds user trust.
Provide regular training for users to boost their confidence in using Microsoft 365 Copilot. Ongoing training raises awareness about security and compliance issues.
Use phased deployment strategies to test features and get feedback. This method lowers risks and helps users get used to new tools.
Access Management
Good access management is very important for safely using Microsoft 365 Copilot. It makes sure that only the right people can see sensitive information and use important features. By using strong access controls, you can lower the chances of data breaches and unauthorized access.
Role-Based Access
Role-Based Access Control (RBAC) is key for managing user permissions. This method gives access rights based on a person’s job in the organization. Here are some main benefits of RBAC:
Automated Role Assignment: RBAC automatically gives roles to new workers. This helps them get the access they need quickly, which lowers the chance of unauthorized access during onboarding.
Prompt Access Revocation: When workers leave or change jobs, RBAC quickly takes away or changes their access. This reduces the risk of former workers keeping unauthorized access.
Principle of Least Privilege: RBAC follows the principle of least privilege. Users get only the permissions they need for their jobs, which limits possible unauthorized access.
Easier Audits: RBAC makes audits easier. Organizations can find accounts with too many privileges and make sure they follow rules like HIPAA and GDPR.
Separation of Duties: The Constrained RBAC model helps with separation of duties. This stops one user from doing important tasks alone, which lowers the risk of fraud or mistakes.
Limited Breach Impact: If there is a security breach, RBAC limits what the attacker can access to the permissions of the affected account. This stops them from moving around the network.
Without good governance, there is a chance that Copilot could access or share information wrongly. This can cause data leaks or break rules, raising big security worries about Microsoft Copilot. Setting clear governance policies is very important to make sure security settings and permissions are set up correctly.
Authentication Methods
Authentication methods are very important for keeping access to Microsoft 365 Copilot safe. Using strong authentication methods helps protect sensitive data and keeps user trust. Here are some suggested methods:
Multi-Factor Authentication (MFA): MFA adds another step of verification beyond passwords. It is the first defense against account hacks and can stop up to 99.9% of account compromise attacks, greatly lowering risk. Right now, 57% of organizations use MFA for security, which is a 12 percentage point rise from last year.
Continuous Verification: Continuous verification is key for keeping security in a zero-trust setup. This method makes sure that user identities are checked all the time, even after the first login.
Identity and Access Controls: Use strong identity and access controls for Copilot users. Make sure all users use multi-factor authentication to boost security. Use Conditional Access policies to limit access based on trusted devices, locations, and risk levels.
By focusing on access management with RBAC and strong authentication methods, you can build a safe environment for using Microsoft 365 Copilot. This not only protects your organization but also encourages users to adopt the system by building trust in its security.
Data Governance
Data governance is very important for safely using Microsoft 365 Copilot. It helps your organization follow data privacy rules and manage sensitive information correctly. By setting up strong data governance practices, you can keep your organization safe from risks and build user trust.
Privacy Regulations
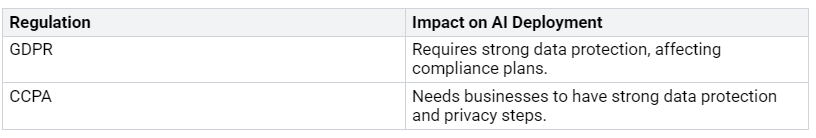
Knowing privacy rules is key for using custom copilots well. Rules like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have strict rules about how organizations handle personal data. Here’s how these rules affect your AI use:
Microsoft is dedicated to following GDPR and CCPA.
This promise helps protect data and follow the law in AI tools.
To make sure your use follows these rules, you must ensure that your large language model (LLM) development meets changing privacy standards. You will face challenges in balancing new ideas with rules, but focusing on following the rules will help your AI efforts in the end.
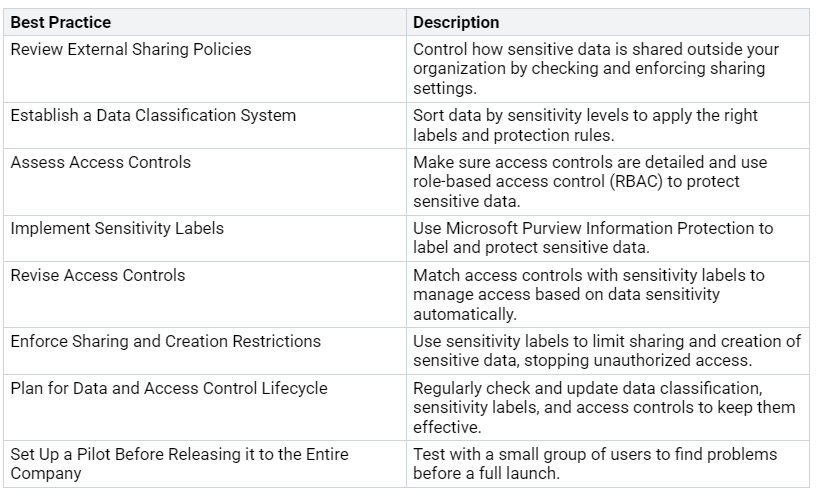
Data Handling Practices
Handling sensitive information the right way is very important for keeping data private and safe. Using best practices for data handling can greatly lower risks from data breaches. Here are some good practices to follow:
By following these practices, you can create a safe place for your employees to work with Microsoft 365 Copilot. Also, think about doing regular checks and using tools to find and secure overexposed content. This proactive approach will help you stay compliant and protect sensitive information well.
User Training
Training your employees well is very important for using Microsoft 365 Copilot successfully. A good training program helps users feel confident with AI tools. Here are some important parts to think about for your training programs:
Training Programs
Multi-modal Training Approaches: Use different training methods for different learning styles. This can include videos, hands-on workshops, and interactive tutorials.
Structured Curricula: Create a clear path from basic knowledge to advanced topics. This helps develop skills fully. Organizations that used structured training saw a 78% success rate in three months for a four-level curriculum.
Real-world Examples: Use case studies and situations that show real workplace problems. This helps employees connect better with the training.
Ongoing user training is also very important for improving your security. It raises awareness of data rules and compliance, helping employees spot possible security issues. Regular training encourages best practices and builds a culture of constant improvement.
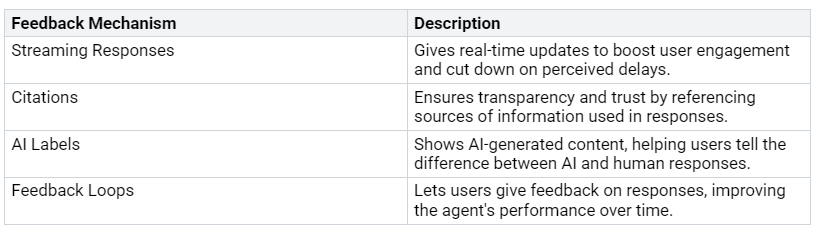
Feedback Channels
Creating good feedback systems is key for improving the employee experience with Microsoft 365 Copilot. Here are some effective feedback channels:
To improve feedback collection even more, think about these strategies:
Use response analysis tools to find common issues and understand employee feelings.
Set up workflows for quick follow-up on negative feedback.
Send out surveys through different platforms, like web portals and SMS.
By using strong training programs and good feedback channels, you can greatly improve the use and security of Microsoft 365 Copilot in your organization.
Phased Deployment Strategies
Using phased deployment strategies is very important for successfully adopting Microsoft 365 Copilot. These strategies help you test features, gather information, and make changes before launching fully.
Pilot Programs
Pilot programs act as a testing area for new tools and processes. They offer many benefits that improve both security and effectiveness during deployment. Here are some main advantages:
By running pilot programs, you can find security problems early. This step-by-step method lets your team collect feedback and fix possible issues. For example, GitHub Copilot can check code in real-time, spotting common security problems that might be missed during regular development.
Feedback Loops
Feedback loops are very important for improving your deployment strategy. Collecting user feedback often helps you make the copilot work better. Here’s how to set up good feedback loops:
Collect Feedback: Regularly get user feedback through surveys, ratings, or direct comments after interactions.
Analyze Data: Use data analysis to find patterns and insights from the feedback you collected.
Iterate on Model: Make needed changes to the AI model or copilot features based on what you find.
Test Changes: Before full launch, test the changes in a controlled setting to make sure they work better.
Deploy Updates: Once confirmed, release the updated model or features to all users.
By including user interactions in your development process, you make Microsoft 365 Copilot more relevant and accurate. This method not only increases user satisfaction but also creates a culture of ongoing improvement in your organization.
Monitoring and Oversight
Monitoring and oversight are very important for keeping your Microsoft 365 Copilot safe and effective. After you launch your copilot, you need to keep an eye on how it works and how users interact with it. This active approach helps you find security threats and compliance problems early.
Continuous Monitoring
Continuous monitoring gives you real-time views of user actions and data movements. This visibility is key for spotting security threats linked to AI tools like Microsoft Copilot. Here are some main benefits of continuous monitoring:
Early Detection of Threats: You can spot strange behavior, changes in permissions, and risks of data exposure. This early detection lets you act fast if there are security issues.
Enhanced Security Posture: Tools like Defender XDR help you watch data flows related to Copilot use. This ability improves your response to threats.
Improved User Experience: By checking agent usage and performance data, you can make the copilot work better. This leads to a nicer experience for your employees.
To monitor your deployment well, think about using these tools:
Analytics, dashboards, and reports: Use built-in analytics dashboards to see agent usage and performance data.
Alerts and incident response: Set up alerts with Microsoft Sentinel for quick incident management.
Compliance and auditing: Use Microsoft 365 Copilot Analytics for insights on how employees use the tool and improve productivity.
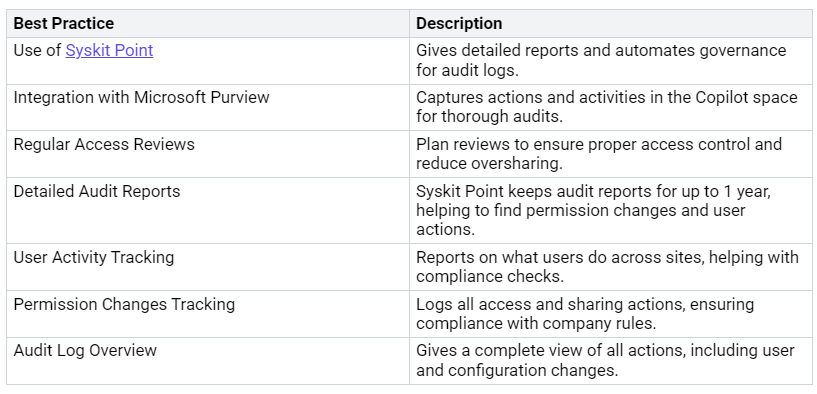
Audit Logs
Audit logs are very important for keeping your Microsoft 365 Copilot secure and compliant. They give a complete view of user actions and interactions in the copilot space. Here are some best practices for using audit logs:
By following these practices, you can make sure your organization stays compliant with rules. Looking at audit logs can show big compliance problems. For example, weaknesses may let users access files without proper logging. This situation can be risky for organizations that need to follow regulations like HIPAA for healthcare and SOX for finance.
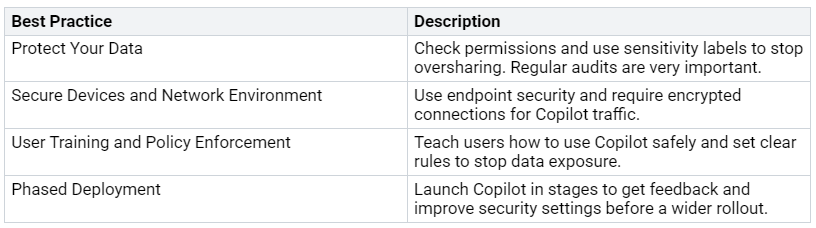
To make sure Microsoft 365 Copilot is safe and works well, follow these best practices:
By doing these steps, you can boost user adoption while keeping strong security measures. Remember, a careful approach to governance and ongoing improvement will help you get the most from your Copilot deployment.
FAQ
What is a custom copilot?
A custom copilot is an AI tool that helps you do tasks faster and better. It combines knowledge from inside and outside your organization to help users in different apps, like Microsoft 365.
How can I ensure data security when using copilots?
To keep data safe, use role-based access control, multi-factor authentication, and strong data rules. Regularly check permissions and watch user activity to stop unauthorized access.
What are the benefits of phased deployment?
Phased deployment lets you test features, get user feedback, and fix problems before a full launch. This method reduces risks and helps users adapt better by making the change easier.
How often should I conduct user training?
You should train users regularly, about every few months. This keeps employees informed about best practices, security rules, and new features, helping them use the copilot safely and effectively.
What should I do if I encounter a security issue?
If you find a security issue, tell your IT department right away. They can look into the problem, reduce risks, and make changes to stop it from happening again.