In today’s IT world, non-human identities are more common than human users. The average ratio is 50 to 1. This fast growth is caused by automation and AI. It brings big security problems. If these identities are not managed well, it can increase your attack surface. This can put your organization at risk. Knowing these risks is very important for good security.
Key Takeaways
Non-human identities, such as service accounts and API keys, are important in IT. However, they can create big security problems. Knowing these risks helps keep your organization safe.
Using least privilege access means giving limited permissions to non-human identities. This lowers the chance of unauthorized access and makes security better.
Automating credential rotation means changing passwords and keys often. Regular updates reduce the risk of credential leaks and help manage security better.
Security Risks of Non-Human Identities
Non-human identities, like service accounts, API keys, and IoT devices, are very important in today’s IT world. But they also bring big security risks. Knowing these problems helps you keep your organization safe from threats.
Common Vulnerabilities
Non-human identities have special weaknesses that can be taken advantage of. Here are some common types of non-human identities and their risks:
Service accounts: These accounts let applications use resources. If set up wrong, they can give too much access, leading to unauthorized entry.
API keys: These special codes help applications work with APIs. If they get out, attackers can misuse them to access private data.
IoT devices: These connected gadgets often do not have strong security, making them easy targets for attackers.
Bots: Software that automates tasks can be hacked if they use weak passwords.
System accounts: These represent operating systems or network devices. Mistakes in setup can create weaknesses.
Application-to-application (A2A) identities: These help software applications talk to each other. If not secured well, they can put your systems at risk.
Virtual machines and containers: Each one needs a unique identity. Bad management can create security holes.
These weaknesses often come from orphaned or overprivileged non-human identities. Credential harvesting from old service accounts is also a big risk. Attackers can use these flaws to get unauthorized access.
Potential Threats
Attackers often go after non-human identities because they have high-level access and can operate quietly. Here are some common ways they attack:
Token Abuse: Attackers misuse bearer tokens that do not have identity checks. This lets them access systems without being noticed.
Living-off-the-Land: Hacked non-human identities act like normal network activity, making it hard to spot bad actions.
Credential Exposure: Hardcoded passwords in setup files can create weaknesses. Attackers can easily find and use these passwords.
For example, in December, attackers got into an API key to access the U.S. Treasury Department’s systems without permission. This showed the risks linked to non-human identities. Delinea CISO Pierre Mouallem said that hacked non-human identities might be a bigger threat than hacked human identities. They often have access to very sensitive information, making them prime targets.
Also, credential stuffing is when attackers use lists of stolen passwords to access non-human identities with weak or reused secrets. This can cause huge financial losses, as breaches can go unnoticed for a long time. The LastPass breach shows how a leaked non-human identity can lead to repeated attacks and increased access, resulting in a lot of stolen data.
By knowing the security risks of non-human identities, you can take steps to keep your organization safe from threats.
Best Practices for Non-Human Identity Management
Managing non-human identities well is very important for strong security. Using best practices can help lower risks linked to these identities. Here are two main strategies to think about:
Implementing Least Privilege Access
Least privilege access is a key idea in identity security. It makes sure that non-human identities only get the permissions they need for their jobs. This helps reduce the risk of giving too much access, which can cause serious security problems. Here are steps to use least privilege access well:
Conduct a privilege audit: Check all privileged accounts often to ensure proper management.
Establish least privilege as the default: Make least privilege the standard for all new accounts.
Implement separation of privileges: Don’t give too many permissions to any one identity.
Provide just-in-time, granular access: Allow temporary access to resources when needed, without causing workflow issues.
Monitor and analyze privileged access continuously: Watch how identities use their permissions.
Review privileges regularly: Take away extra permissions to keep a secure environment.
By limiting access rights, you can reduce possible damage from compromised identities. This strategy helps contain the impact of any attack, lowering the chances of account breaches. Organizations that use least privilege access often see better overall security.
Automated Credential Rotation
Automating credential management is another important practice for protecting non-human identities. Regularly changing credentials helps lower the risks of credential leaks. Here are some best practices for automating credential rotation:
Automate credential rotation and just-in-time issuance: This lowers the chances of credentials being exposed.
Regularly review and retire unnecessary identities: This stops security risks from old accounts.
Implement automation and orchestration: This cuts down on human error and boosts security.
Regularly update passwords, tokens, and keys: Keeping credentials fresh limits chances for attackers.
Adopt secure, scalable solutions: Ensure consistency in managing non-human identities across cloud and hybrid environments.
By following these practices, you can improve your organization’s identity security management. Automating credential rotation not only boosts security but also makes operations smoother, letting your team focus on more important tasks.
Making Security Better with a Zero Trust Framework
A Zero Trust framework is very important for managing non-human identities. It believes that threats can come from anywhere. This means you cannot trust any user or device automatically. This method focuses on always checking and watching all identities, like service accounts and API keys. By combining human and non-human identity management, you can build stronger security.
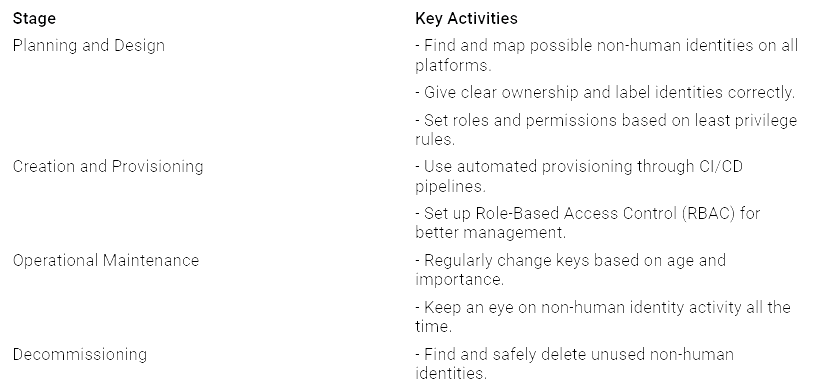
Managing Identity Lifecycles
Good identity lifecycle management is key for non-human identities. You should do these important activities:
By managing these identities well, you can stop unauthorized access and lower security risks.
Ongoing Monitoring and Audits
Ongoing monitoring is crucial for keeping security in a Zero Trust setup. You need to see everything about your machine identity landscape. This includes:
Regular checks of non-human identities to ensure they follow rules.
Watching for strange activity that might mean a breach.
Using tools that give real-time information about identity use.
By taking a proactive approach to monitoring, you can quickly find and deal with possible threats. This plan not only improves security but also makes management easier across your IT environment.
Keeping non-human identities safe is very important for your organization’s cybersecurity. As you follow best practices, think about these important trends:
New standards for managing non-human identities will come up.
Moving to temporary solutions will replace old identities.
Zero trust plans will include non-human identities, treating them like human ones.
By putting money into ongoing discovery and automated management, you can make your defenses stronger against possible threats. Remember, strong authentication methods and constant monitoring are key to keeping your systems safe.
FAQ
What are non-human identities?
Non-human identities are things like service accounts, API keys, and IoT devices. Applications use them to get to resources.
Why are non-human identities a security risk?
These identities usually have too many permissions and fixed credentials. This makes them easy targets for attackers.
How can I improve non-human identity security?
You can use least privilege access, automate changing c