In today’s online world, managing identities for many tenants is hard. You might face problems like different identity systems when companies merge. This can make it tough for users from different tenants to share resources. SCIM provides a strong solution by automating Multi-Tenant Identity Management. It makes identity processes the same, allowing easy syncing across different platforms. As organizations grow and use more cloud services, good identity management is very important for security and following rules.
Key Takeaways
SCIM helps set up and remove users automatically. This cuts down on mistakes and makes identity management faster.
SCIM also makes security better. It updates user roles and permissions quickly. This lowers the chances of unauthorized access.
SCIM makes it easier to bring in new users. Organizations can add them to their systems quickly.
Regular checks of SCIM systems keep security strong. They make sure user access is managed correctly.
Using SCIM can save a lot of money. It makes identity management easier for many tenants.
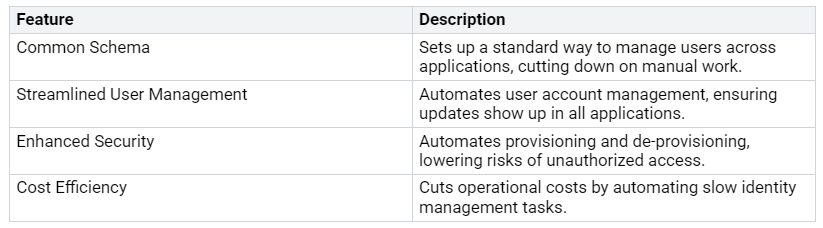
SCIM Benefits
Efficiency in Multi-Tenant Identity Management
SCIM makes multi-tenant identity management much better. It automates user setup and removal. This means you don’t have to do it by hand, which can cause mistakes. With this automation, you can manage user accounts on many platforms easily.
Using SCIM for user management lowers the chance of unauthorized access. You can quickly give and take away user access, which is very important for safety.
SCIM improves security by handling identity lifecycles. This means it automatically sets up and removes user accounts. This helps keep identity management safe and consistent.
Using SCIM makes onboarding new users easier. You can get new users started fast, which saves time.
For example, the Charon version of the SCIM service at KnowBe4 cut operational costs by 99.37%. Now, costs depend on how many customers are onboarded. This allows for quick changes instead of fixed costs. This efficiency saves time and lowers the total cost of managing identities for many tenants.
Scalability for Growing Organizations
As organizations grow, scalability is very important for identity management. SCIM helps this growth by automating tasks that used to be done by hand and could cause errors.
Without SCIM, growing feels like pushing a heavy rock uphill. With SCIM, it feels like rolling downhill—smooth, fast, and easy.
SCIM helps scalability in many ways:
It automates user setup and removal, making it easy to manage more users.
It simplifies onboarding, cutting down on extra work and speeding up adoption across teams.
SCIM boosts security and compliance, making sure your identity management stays strong and safe as you grow.
It helps teams adopt faster, so you can grow your operations without the hassle of complicated identity management tasks.
By automating what used to be done by hand, SCIM quickly creates accounts, gives permissions, and syncs access as teams change. This ability supports smooth growth and ensures your identity management keeps up with your organization’s expansion.
Key Features of SCIM
SCIM has many important features that make managing identities easier and safer for many tenants. These features help you handle user identities well across different platforms.
User Provisioning and De-provisioning
User provisioning and de-provisioning are key steps in identity management. SCIM makes these tasks faster and more dependable. Here’s how it works:
When an employee leaves, the Identity Provider (IdP) turns off their account.
The IdP sends a notice to each service provider in a set format.
Each service provider gets this information and turns off or deletes the user account. This makes sure the user is taken out of any groups, stopping unauthorized access.
This automation lowers the chance of security problems. Forgetting to de-provision can make organizations open to compliance issues. SCIM helps you manage user lifecycles well, whether it’s bringing in new employees or taking away access for those who don’t need it anymore.
Standardized API Endpoints
Standardized API endpoints in SCIM make it easier to connect with current identity management systems. These endpoints give a clear structure for managing users and groups. Here are some benefits of using standardized API endpoints:
You can work with many applications using the same endpoints and data formats.
Changes, like user promotions, spread easily across connected applications because of the uniform SCIM endpoints.
This consistency cuts down on mistakes and makes provisioning smoother.
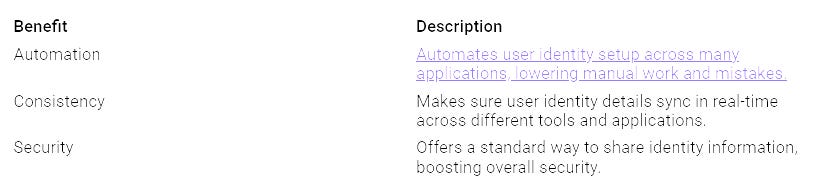
By using SCIM, you can lower manual work and deal with identity issues. Automating user lifecycle management makes sure all identity changes come from one source. This method boosts security and compliance while making everything run better.
By using these key features, SCIM helps you manage identities well in a multi-tenancy setting.
Implementing SCIM in Multi-Tenancy
Using SCIM in a multi-tenant setup needs careful planning. First, check your current identity management systems before starting the integration. This check helps you find problems and get ready for a smooth move to SCIM.
Assessing Current Systems
Before using SCIM, spend time looking at your current identity management systems. Follow these steps:
Understand user access: Find out which users can access company resources. This includes employees, IoT devices, and outside partners.
Identify assets: Write down the physical tools and apps that need protection.
Evaluate connection methods: Check how users connect to the network, especially when working from home.
Analyze usage patterns: Look for regular user access patterns to spot any unauthorized access.
Examine current IAM systems: Check how well your current identity and access management systems work to make sure they meet rules.
By following these steps, you can see your current identity setup clearly. This knowledge will help you adjust your SCIM setup to fit your organization’s needs.
Configuring SCIM Connectors
After checking your current systems, the next step is to set up SCIM connectors. These connectors are important for automating user setup and removal. Here are some best practices for setting up SCIM connectors in a multi-tenant setup:
SCIM automates user lifecycle management, including onboarding and offboarding, which is key for security and compliance.
It serves as a single source of truth for user roles, helping with access management.
Connecting SCIM with security frameworks like SOC 2 and ISO 27001 helps with compliance and boosts security.
To set up SCIM connectors successfully, think about these steps:
Set up your main user account using AzureAD SSO for easy access.
For automated setups, think about using API keys.
Set up a second domain or subdomain in Azure for managing multiple tenants.
Microsoft Entra ID works well with SCIM in multi-tenant setups. Here’s how it improves your SCIM setup:
Microsoft Entra ID helps manage users by finding them through their email addresses. This lets SCIM users access only one tenant.
Group management is easier because groups are identified by name. SCIM manages groups that exist in a tenant.
Users and groups synced by SCIM are marked clearly, ensuring easy management and control.
By using Microsoft Entra ID, you can make adding users to tenants and managing their access easier. This connection simplifies the challenges of multi-tenancy while keeping strong security and compliance.
Challenges and Solutions
Using SCIM in a multi-tenant setup can bring some problems. You might face issues with integration and compliance that need careful handling.
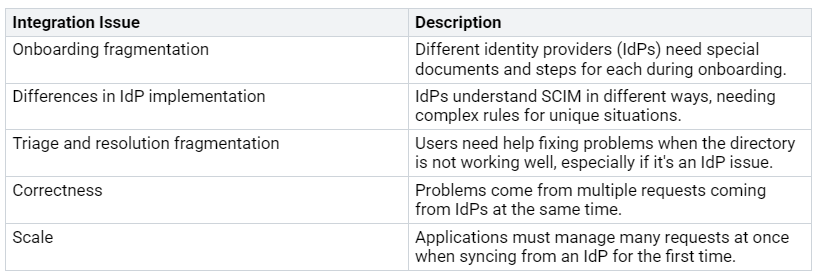
Integration Issues
Integration problems often happen when you set up SCIM. Here are some common issues you might see:
To solve these integration problems, think about using Directory Sync by WorkOS. This service gives a safe and simple way to set up users. You only need to connect with the WorkOS API, which works with all major identity providers. WorkOS takes care of the tricky parts of each provider, making sure SCIM requests are processed in real-time.
Compliance and Security Concerns
Compliance and security are very important when using SCIM in multi-tenancy. You need to make sure your identity management system follows the rules. Here are some things to think about for compliance:
Send requests to the right organization based on a shared secret, subdomain, or token mapping.
You need to figure out tenant context from request headers or credentials since identity providers don’t share tenant info directly.
Also, security issues can happen in multi-tenant systems. You should connect the SCIM identity to a user object to ensure proper checks. A well-known case of account takeover happened when an email change was not properly approved, causing problems in user management. Not having tenant-isolation logic can make security worse, allowing unauthorized access between different tenants.
By tackling these challenges early, you can improve how well your multi-tenant identity management works with SCIM.
Best Practices for SCIM
Regular Audits
Regular audits are very important for keeping your SCIM system safe. You should do these audits to check for security and rules. Here are some steps to follow:
Audit User Data: Look at user accounts and their access levels often. This helps you find any unauthorized access or unused accounts.
Review SCIM Logs: Check logs for any strange activity. This can warn you about possible security problems or integration issues.
Assess Compliance: Make sure your SCIM processes follow industry rules. This includes checking that adding and removing users follows set policies.
By doing these audits, you can find problems early and keep a secure environment for accessing a tenant with single sign-on.
Documentation and Training
Good documentation and training are key for a successful SCIM setup. You should focus on several important parts:
Setting Goals and Objectives: Clearly define what you want to achieve with your SCIM setup. Identify who is involved and create a plan for implementation.
Select a SCIM-Compatible Identity Provider: Pick the right IdP that fits your organization’s needs. Check its features to ensure it works well.
Configure SCIM Endpoints: Set up and protect endpoints for communication between your systems.
Map User Attributes: Find and match user attributes to the SCIM schema. This makes sure data syncs correctly.
Implement SCIM Provisioning: Set rules for provisioning and test them thoroughly to ensure they work.
Monitor and Maintain SCIM Integration: Keep an eye on the system and update it regularly to keep it running well.
Establish Clear Governance: Create SCIM policies and assign roles to ensure everyone is responsible.
Conduct Regular Audits: As mentioned before, checking user data and SCIM logs is very important.
Train IT Staff and End-Users: Provide training for IT staff and teach end-users how to use the system properly.
By following these best practices, you can improve your SCIM use in a multi-tenancy setting. This will boost security and make adding users to tenants easier.
In conclusion, SCIM is very important for automating identity management in multi-tenant settings. It makes user setup easier and improves security. By automating how user identities are set up, you lower the need for manual work and mistakes. This helps keep identity management steady and safe across different applications.
Think about the long-term advantages of SCIM:
By using SCIM, you make user management easier and cut costs linked to custom solutions. Choose SCIM as a good option for your identity management needs, especially if you handle users from many tenants.
FAQ
What is SCIM?
SCIM means System for Cross-domain Identity Management. It helps manage user identities on different platforms. This keeps access safe and the same for users in multi-tenant settings.
How does SCIM improve security?
SCIM makes security better by automating user setup and removal. This lowers the chance of unauthorized access. It also makes sure user roles and permissions are updated on time.
Can SCIM integrate with existing systems?
Yes, SCIM can work with many identity management systems. It uses standard API endpoints. This makes it easier to connect and manage user identities across different apps.
What are the main benefits of using SCIM?
The main benefits of SCIM are better efficiency, scalability, and security in managing identities. It automates tasks, cuts down on mistakes, and helps follow rules.
How do I get started with SCIM?
To start using SCIM, first check your current identity management systems. Then, set up SCIM connectors and link them with your existing platforms. Think about using Microsoft Entra ID for easier management.