In today’s online world, security problems with identity are a significant risk for companies. By 2026, businesses with strong Unified Identity Security plans will have 50% fewer breaches than those without. Sadly, more than half of all breaches include customer personal information, such as important data like emails and tax ID numbers. As you navigate the challenges of identity security, it is crucial to understand how solutions like Conditional Access and Defender for Identity work together. This collaboration not only enhances your security but also addresses the urgent issues of managing identities effectively.
Key Takeaways
Combining Conditional Access and Defender for Identity makes security better. It uses different ways to check user access. This lowers the chance of unauthorized access.
Conditional Access lets organizations create specific rules for access. These rules depend on user roles, device safety, and location. This helps control sensitive data better.
Defender for Identity keeps watch and finds threats all the time. It helps organizations act fast against suspicious actions and possible breaches.
Updating security rules often and doing practice attacks can make defenses stronger. This also helps meet industry standards.
A combined identity security plan makes management easier across platforms. It builds trust with customers and protects against new threats.
Conditional Access Overview
Conditional Access is an important tool in identity security. It uses different signals to make smart access decisions. This system works on a simple if-then rule. Access to resources depends on certain actions done by the user. By checking more than just passwords, Conditional Access boosts security. It makes sure the right people get access at the right times.
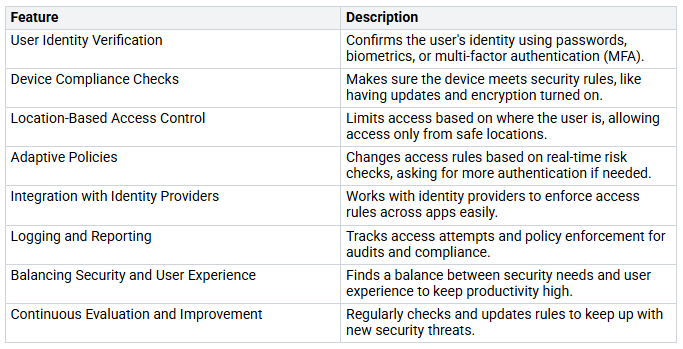
Key Features
The table below shows the main features that set Conditional Access apart from other access management tools:
Benefits of Conditional Access
Using Conditional Access gives many benefits for organizations:
Enhanced Security: By checking access with multiple factors, you greatly lower the chance of unauthorized access.
Granular Control: You can set access rules based on user roles, location, and device type, reducing unauthorized data exposure.
Improved User Experience: Smart security measures improve user experience by cutting down on unnecessary prompts, letting real users access resources easily.
Transition to a True Zero Trust Posture: This method checks every access request based on identity and device trust, lowering the attack surface.
Fewer Infosec Headaches: Organizations see lower control costs and less need for on-premises solutions, making IT easier.
By using Conditional Access, you can manage access better and boost your organization’s overall security.
Defender for Identity Insights
Microsoft Defender for Identity is a cloud security tool. It helps watch over and protect identities in organizations. It works well with Microsoft Defender XDR. It uses signals from both on-site Active Directory and cloud identities. This helps you find, spot, and check advanced threats easily. Defender for Identity keeps an eye on domain controller traffic. This helps you notice strange activities during cyber-attacks.
Core Capabilities
Defender for Identity has many important features that improve your security:
24/7 Monitoring: It watches identity sources all the time. This helps you find threats as they happen.
Behavioral Analytics: The tool looks at user behavior. It finds odd logins or rule changes that might mean a threat.
Incident Response: You can quickly act on incidents. For example, you can deactivate hacked user accounts to reduce risks.
Visibility into Authentication Traffic: Defender for Identity shows you authentication traffic and security settings. This helps you see possible weaknesses.
Detection of Identity-Based Attacks: It is made to find attacks like stealing credentials and gaining extra privileges.
Advantages of Defender for Identity
Using Microsoft Defender for Identity has many benefits over older security tools:
Proactive Threat Detection: By looking at user behavior, you can find suspicious actions before they get worse.
Integrated Security Strategy: Defender for Identity works well with other security tools. This creates a united way to protect identities.
Comprehensive Visibility: It uses different sources of threat information and behavior analysis. This gives you a clear view of your security situation.
Regulatory Compliance: The tool improves security to protect sensitive data. It also helps meet rules like HIPAA and ITAR.
Reduced Administrative Burden: Automating regular tasks makes compliance easier for your IT teams.
By using the features of Defender for Identity, you can greatly improve your organization’s identity security system.
Importance of Unified Identity Security
In today’s complicated online world, combining Conditional Access and Defender for Identity is very important for strong security. This combination helps you build a unified identity security system. It improves your overall security and lowers possible weak spots.
Enhancing Security Posture
Unified identity security keeps an eye on all identities in your organization all the time. This method helps you find weaknesses and makes sure you follow identity rules. By setting access rights that match business needs and laws, you greatly lower risks linked to identity management.
Microsoft Defender for Identity protects your on-site identities. It uses smart technologies like machine learning and behavior analysis. This helps find and respond to threats right away. This ability improves the safety of your identity data and assets. It lets you keep track of your organization’s security status well.
The combination of Conditional Access and Defender for Identity gives you many key benefits:
Visibility into Applied Risk-Based Policies: You can see the specific risk-based policies used in sign-in logs. This helps you check how well they work in your organization.
Advanced Conditional Access Features: You get better options for Conditional Access, like setting rules based on how often users sign in. This gives you more control over user access.
Unified Access Policy Management: Managing all access policies in one place makes admin tasks easier and boosts efficiency.
Enhanced Flexibility in Access Control: You can improve access control by adding different risk conditions, like location, for a stronger security system.
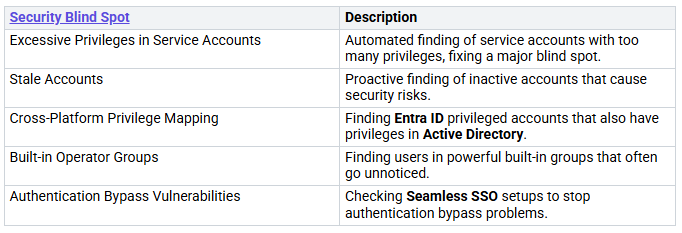
Reducing Blind Spots
Combining Conditional Access and Defender for Identity helps fix common security blind spots that organizations have. These blind spots can cause big weaknesses if not taken care of. For example, too many privileges in service accounts and old accounts can create security problems. By automating the finding of these issues, you can manage your security better.
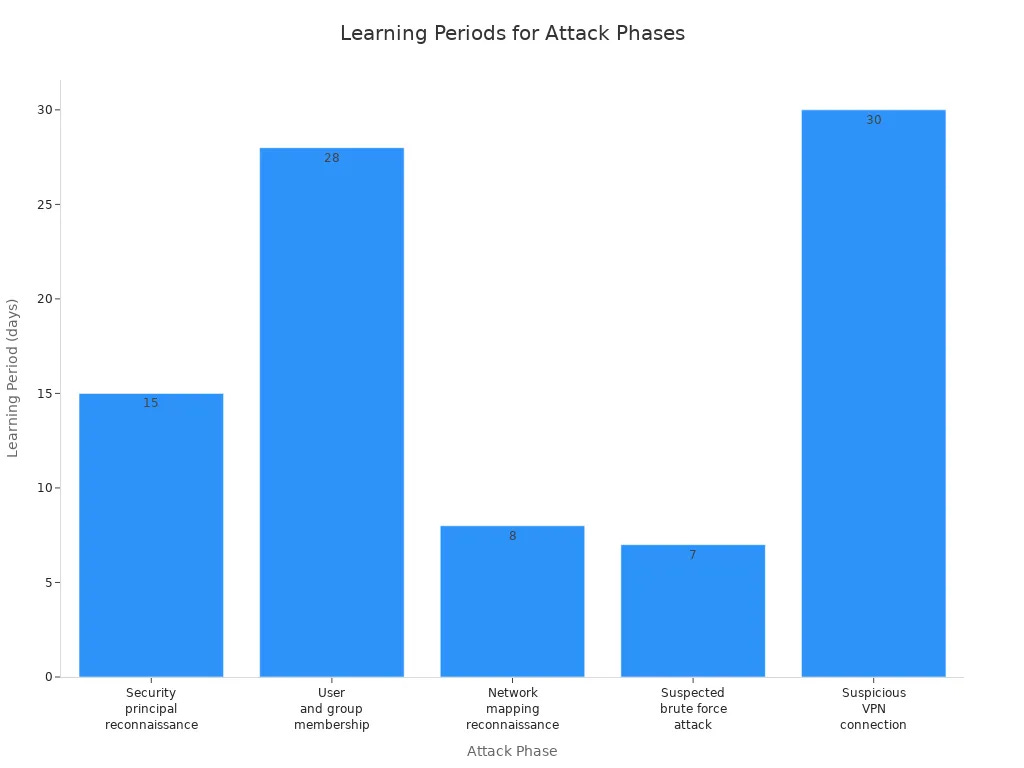
By combining these tools, you can greatly improve your organization’s ability to find and react to security threats. AI systems can analyze thousands of frames every second. They can spot threats that human workers might miss. This ability cuts down on false alarms by telling apart normal actions from real threats, thus boosting overall security.
Integration Steps for Security Teams
To connect Conditional Access with Defender for Identity, you need to plan carefully. Follow these steps to make the integration go smoothly.
Configuration Guidelines
Define Security Policies: First, set up security rules that match industry standards. This helps your organization follow best practices and meet legal requirements.
Inventory Cloud Assets: Find and list all cloud assets. This helps you know what needs protection and makes sure no accounts are left open to risks.
Apply Secure Baseline Configurations: Use secure settings on all platforms. Keeping settings the same lowers the chance of mistakes that could cause security problems.
Automate Scanning and Detection: Use tools to automatically check for mistakes in settings. This helps you find risks quickly and fix them before they get worse.
Track Configuration Drift: Watch for any changes in your settings that are not allowed. Keeping an eye on these changes helps keep your security strong and ensures you follow the rules.
Enforce Policy-Based Remediation: Set up rules that automatically fix any problems found. This helps you respond to alerts faster and makes things easier for your security teams.
Ensure Continuous Compliance: Check your settings regularly to make sure they meet legal standards. Ongoing checks are key to keeping strong security.
Following these steps not only boosts your security but also follows best practices from NIST Special Publication 800-53 and CIS Control 4. These guidelines stress the need for good configuration management to stop data breaches from mistakes.
Best Practices
To make your integration work better, think about these best practices:
Regularly Update Policies: Keep your security rules current. As new threats come up, your defenses should change too. Regular updates help your organization stay strong against new attacks.
Conduct Simulated Attacks: Run fake attacks often to test your security. This helps you find weak spots in your defenses and lets you improve your response plans.
Utilize Unified Dashboards: Use combined dashboards to watch alerts from both Conditional Access and Defender for Identity. This gives you a complete view of your security, helping you respond to threats better.
Train Your Teams: Make sure your security teams know how to use both tools well. Trained staff can use the features of Conditional Access and Defender for Identity better, leading to stronger security.
Review and Adjust: Check how well your integration is working regularly. Change rules and settings based on what you learn from monitoring and responding to incidents.
By following these steps and best practices, you can build a strong connection between Conditional Access and Defender for Identity. This will improve your organization’s overall security and lower the risk of identity-related threats.
Using Conditional Access and Defender for Identity builds a strong security system for your organization. Here are the main points from this combination:
Conditional Access (CA) looks at different factors before giving access. This makes security and compliance better.
Microsoft Entra ID lets you create detailed CA rules that change based on real-time risk checks.
New CA methods check device health, location, and session control. They do more than just multi-factor authentication (MFA).
As you deal with the challenges of identity management, keep in mind that a unified identity security plan is very important. It makes security management easier across different platforms and helps with identity oversight. In today’s world of increasing fraud and AI attacks, a strong identity plan not only protects users but also builds customer trust and helps your business grow.
“A unified identity security platform is essential to provide comprehensive visibility and control across all access types, reducing security gaps.”
By focusing on integration, you can make your organization stronger against changing threats.
FAQ
What is Conditional Access?
Conditional Access is a security tool. It uses different signals to decide who can access resources. It checks user identity, device safety, and location to allow or block access.
How does Defender for Identity enhance security?
Defender for Identity watches user actions and login traffic. It finds unusual activities and gives you information to help you act fast against possible threats.
Why should I integrate Conditional Access with Defender for Identity?
Combining these tools makes a strong security system. This mix improves real-time threat detection and flexible access control. It helps close security gaps and boosts overall safety.
What are the key benefits of unified identity security?
Unified identity security helps you see everything better, reduces hidden risks, and improves compliance. It also makes security management easier, helping you protect sensitive data.
How can I start integrating these tools?
Start by setting up security rules and listing cloud assets. Follow setup guidelines and best practices to make the integration process smooth and improve your organization’s security.