In today’s digital world, organizations face new security challenges. The rise in cyberattacks makes it important for you to use strong cybersecurity strategies. Recent data shows that the average cost of a data breach will hit $4.44 million by 2025. Also, 78% of breaches come from cyberattacks. This worrying trend highlights the need for careful attention and action. As threats change, you must use complete strategies to protect sensitive information well.
Think about these changing threats:
There are big risks from third-party exposures.
State-sponsored actors are targeting critical infrastructure.
To tackle these challenges, you need to keep improving your cybersecurity strategy.
Key Takeaways
Organizations need strong cybersecurity plans to fight growing cyber threats and keep sensitive data safe.
Using Zero Trust principles makes sure every access request is checked. This lowers the chance of data breaches.
Regular risk checks and ongoing monitoring are important for finding weaknesses and boosting security.
Using advanced tools like AI and automation can improve threat detection and response times. This makes cybersecurity work better.
Building a culture of cybersecurity awareness among workers helps them spot and stop insider threats.
Current Cyber Threat Landscape
Types of Cyber Threats
Today, organizations deal with many cyber threats. These threats can disrupt work and put sensitive data at risk. Here are some common types:
Ransomware: This is a very serious threat. Ransomware can stop operations and hurt reputations in all areas.
Misconfigurations and Unpatched Systems: These problems make you vulnerable to cyber risks. Hackers often take advantage of systems that need updates.
Credential Stuffing: Cybercriminals use bots to exploit reused passwords. This lets them get into accounts without permission.
Social Engineering: Attackers trick users into giving away sensitive information. They may fool you into doing things that harm security.
The growth of hybrid work and cloud use changes the threat landscape. As you move workloads to the cloud, securing these systems gets harder. This makes cybersecurity risks go up. You might lose sight and control over data security, making it tough to manage these risks. Remote work brings new weaknesses since employees work outside regular offices. While hybrid cloud models have benefits, they also raise cybersecurity risks, needing new security methods.
Insider Threats
Insider threats are different from outside threats. These threats often come from employees or contractors who have real access to your systems. They can be harder to spot because they know how things work inside. Insider threats can cause serious damage, often leading to data theft and network problems. Unlike outside attackers, insiders may use clever methods for personal gain. Their ability to cause big problems shows the need for strong monitoring and response plans.
In this changing threat landscape, organizations must stay alert. Knowing the types of threats you face is key to creating good cybersecurity strategies.
Limitations of Traditional Cybersecurity Strategies
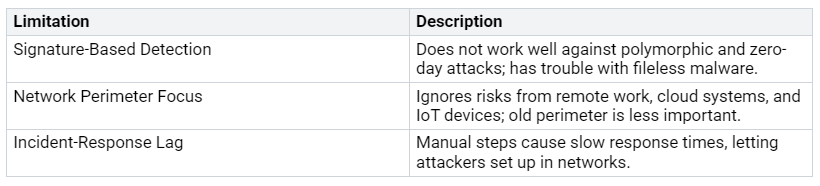
Reactive Approaches
Many organizations still use old cybersecurity methods. These methods often react to problems instead of stopping them. This reactive way makes you open to new threats. For example, signature-based detection has trouble with polymorphic and zero-day attacks. It also cannot find fileless malware. Plus, focusing on network perimeter security ignores risks from remote work and cloud systems.
Here’s a summary of some limits of traditional reactive methods:
These limits show why you need a proactive cybersecurity plan. You should expect threats before they happen. Changing your mindset can greatly improve your security.
Common Vulnerabilities
Old systems often have weaknesses that attackers use. These weaknesses come from outdated security, compatibility problems, and unpatched systems. Here are some common weaknesses in traditional cybersecurity systems:
Outdated security: Old systems often lack modern features like firewalls and multi-factor authentication.
Compatibility issues: New security tools may not work with older systems, making them less effective.
Unpatched weaknesses: Old systems often do not get updates, leaving them open to known attacks.
Knowing these weaknesses is important for making a good incident response plan. By fixing these issues, you can make your defenses stronger and lower the chance of successful attacks.
Enhancing Cybersecurity Strategies with Zero Trust
Zero Trust is a new way to think about cybersecurity. It follows the idea of “Never trust, always verify.” This method moves away from old defenses that focus on protecting the outside. These old methods can leave organizations open to attacks. Zero Trust believes that both inside and outside sources can be dangerous. It focuses on checking user access requests all the time, no matter where they come from. This is very important today because many people work from home and use cloud services. By using Zero Trust, you can lower the chances of data breaches and improve your overall security.
Identity and Access Management
Identity and Access Management (IAM) is very important in a Zero Trust security model. IAM systems make sure that only the right users can see sensitive information. Here are some key parts of IAM in a Zero Trust setup:
Multi-Factor Authentication (MFA): This method asks users for different ways to prove who they are before they can access systems. MFA adds an important layer of protection against unauthorized access.
Granular Access Controls: Setting strict access rules based on user roles helps reduce risks. This makes sure users only see the information they need for their jobs.
Continuous Monitoring: Keeping an eye on user activities lets you quickly take away access if something suspicious happens. This helps prevent breaches and keeps security strong.
Context-Aware Access Decisions: By looking at things like where the user is and what device they are using, you can make smart access choices that fit with Zero Trust ideas.
Data Encryption: Protecting sensitive data with encryption keeps it safe and secure, adding another layer of defense against breaches.
By focusing on these IAM practices, you can build strong security rules that match Zero Trust ideas.
Continuous Verification
Continuous verification is another key part of Zero Trust. This process makes sure that all users and devices prove who they are before they can access the network. Here are some best practices for using continuous verification:
Authenticate Before Access: Make all users and devices verify their identities before they can use any network resources.
Ongoing Identity Checks: Regularly check that access permissions are still valid over time. This helps keep security strong as user roles change.
Utilize Multiple Authentication Factors: Use different ways to verify identity, like biometrics and one-time passwords, to boost security while allowing flexible access.
To effectively use continuous verification, follow these steps:
Use the idea of “never trust, always verify” for all network parts.
Set clear boundaries and security rules that support continuous verification.
Create strict access rules for each part to stop unauthorized access.
Continuous verification is a key part of Zero Trust systems. It makes sure that access permissions are not just based on where users are in the network. By always checking and verifying user and device identities, you can greatly lower the risk of internal threats and keep a secure environment.
Using Technology for Today’s Cybersecurity
In the changing world of cybersecurity, using technology is very important. You can make your defenses stronger by adding advanced tools and solutions. The Microsoft Security Ecosystem is a complete set that offers strong protection against today’s threats.
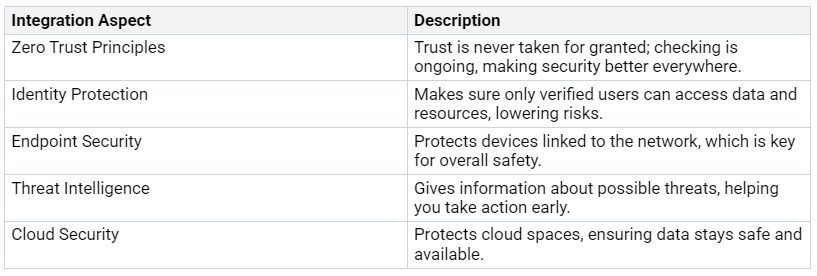
Microsoft Security Ecosystem
The Microsoft Security Ecosystem combines different security solutions to create a strong defense plan. This combination has many benefits:
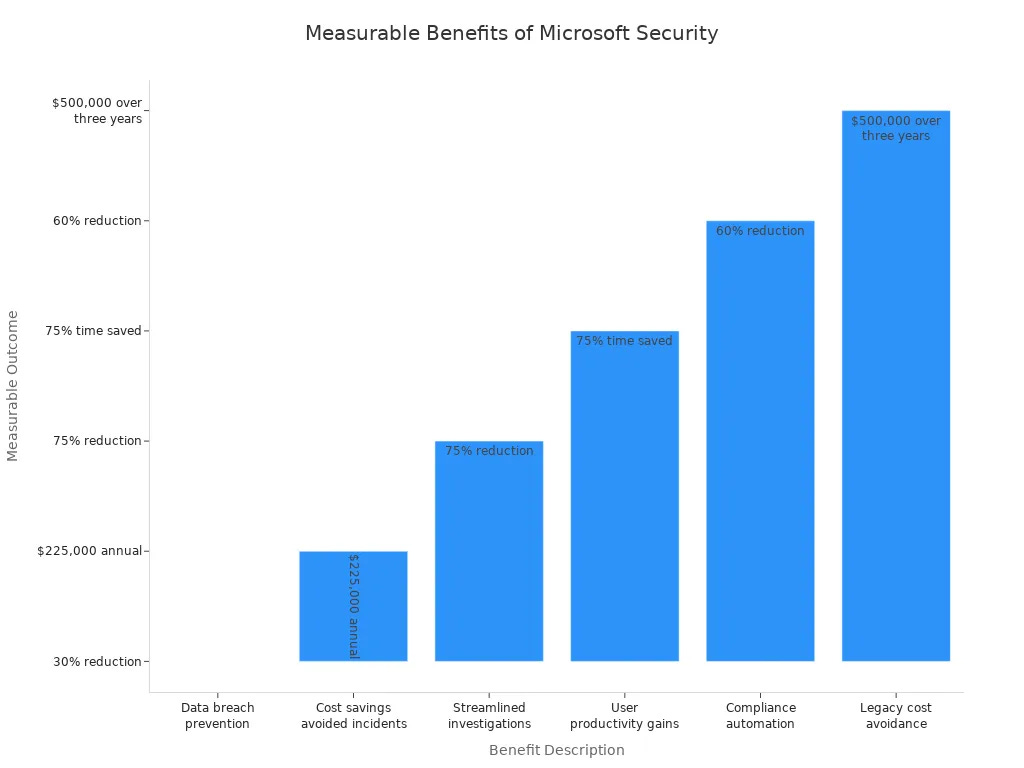
By using these combined solutions, you can greatly lower the chances of data breaches. In fact, organizations that use the Microsoft Security Ecosystem see a 30% drop in data breach chances. This ecosystem not only makes security checks easier but also saves time and resources.
Automation and AI Tools
Automation and AI tools are very important in today’s cybersecurity. They help you find and respond to threats quickly. Here are some main uses and benefits of these technologies:
Proactive Threat Hunting: AI changes cybersecurity from just reacting to threats to actively searching for them by learning and adapting.
Real-time Pattern Recognition: Machine learning models learn from past events to spot similar patterns right away.
Phishing Detection: AI checks email links and content to block 92% of phishing attempts before they reach you.
Behavioral Biometrics: AI improves authentication by looking at user behavior patterns for identity checks.
Continuous Monitoring: AI provides 24/7 threat detection without getting tired, boosting overall security.
The effects of AI and automation are huge. For example, AI increases productivity by 40% after it is used. Automated vulnerability scanning finds weaknesses 89% faster than doing it by hand. Also, AI cuts down on human mistakes, which cause 90% of successful breaches.
To sum up the benefits of AI in cybersecurity, think about these points:
AI looks at large amounts of data to find patterns of cyberattacks, helping to spot suspicious activities quickly.
Continuous monitoring by AI helps find compromised devices and block harmful traffic, making defenses stronger.
AI tools check user authentication data to find unusual activities, improving user verification.
By adding these advanced technologies, you can boost your cybersecurity strategies and get ready for the future of cybersecurity. The mix of the Microsoft Security Ecosystem and AI tools creates a strong defense against changing threats.
Continuous Improvement in Cybersecurity
Improving cybersecurity all the time is very important. You need to check risks often and change your plans to stay safe from threats. Regularly checking for risks helps you find weak spots and make your defenses stronger.
Risk Assessment Practices
To create a strong culture of managing risks, follow these helpful steps:
Use a framework.
Make a risk assessment process.
Share responsibilities.
Focus on cybersecurity risks.
Make a response plan.
Train your workers.
Keep an eye on threats.
Act quickly.
Share information.
These steps help you stay aware of possible threats and respond fast. By using a performance-first approach, you can go beyond just following rules and be ready to act. Continuous performance management gives you proof of how well your security works. This way, you can question risk numbers and move resources based on how things are going.
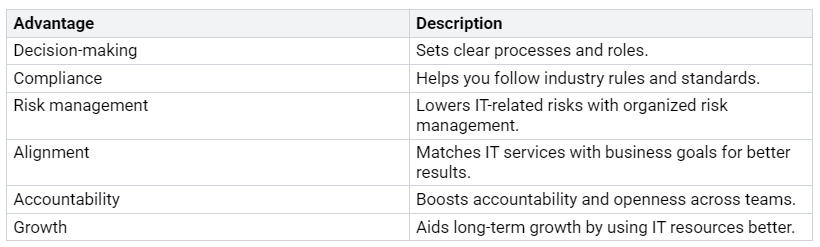
Governance Frameworks
Governance frameworks are very important for improving cybersecurity over time. They set clear processes and roles, which helps you follow industry rules. Here are some benefits of using governance frameworks:
The NIST Cybersecurity Framework (CSF) gives guidelines for handling cybersecurity risks. It helps you find, protect, detect, respond to, and recover from cyber threats. By matching your security rules with risk priorities, you can keep checking and improving your cybersecurity strength.
Today, the threat landscape is changing fast. You need to use strong cybersecurity strategies. These strategies help improve your security and make operations run better. They also keep sensitive data safe. For example, organizations using Zero Trust architecture have better compliance and more trust in their systems.
To boost your cybersecurity, think about these steps:
Do regular security checks.
Watch networks and software for weaknesses.
Focus on the biggest risks.
Set and track security goals.
Use automation tools.
Make and follow an incident response plan.
By following these steps, you can lower the chances of cyber incidents and get ready for future threats.
FAQ
What is Zero Trust in cybersecurity?
Zero Trust is a way to keep data safe. It means you can’t trust any user or device right away. You need to check every request to access information, no matter where it comes from.
How can I improve my organization’s cybersecurity posture?
You can make your cybersecurity better by using Zero Trust ideas. Also, do regular checks for risks and use smart tools like AI and automation to find and respond to threats.
What are insider threats?
Insider threats are problems that come from workers or contractors. They misuse their access to hurt the organization. These threats can be on purpose or by mistake, making them hard to find and handle.
Why is continuous monitoring important?
Continuous monitoring helps you find threats as they happen. It lets you act quickly when something seems wrong, which lowers the chance of data breaches and keeps things safe.
How does automation benefit cybersecurity?
Automation makes security tasks easier and faster. It helps you spot and deal with threats quickly. It also cuts down on mistakes and lets your security team work on harder problems.