Mastering Entra ID app registration and OAuth 2.0 is very important for today’s developers. You get many benefits, like better security, easy integration, and growth options. These features help your apps follow rules and standards. Knowing how to use these tools helps you create safe and strong connections with Microsoft services.
Key Takeaways
Know the permissions needed for Entra ID app registration. Roles like Application Administrator and Cloud Application Administrator are important for managing your app well.
Pick the right account type for your app. Choose between single-tenant and multi-tenant options based on who needs access and how you control permissions.
Use best practices for OAuth 2.0. Manage tokens securely, check redirect URIs, and use CSRF protection to keep your apps safe.
Prerequisites for Entra ID App Registration
Before starting with Entra ID app registration, you must know the needed permissions and the basics of OAuth 2.0. These prerequisites are very important for a good app registration process.
Required Permissions
To register an application in Microsoft Entra, you need certain permissions. Here are the main roles you should know about:
Application Administrator: This role lets you create and manage all parts of enterprise applications, including application registrations. You can also agree to delegated permissions.
Cloud Application Administrator: This role is like the Application Administrator. It has the same permissions but cannot manage application proxy settings.
Having the right permissions helps you manage your app registration and its settings well.
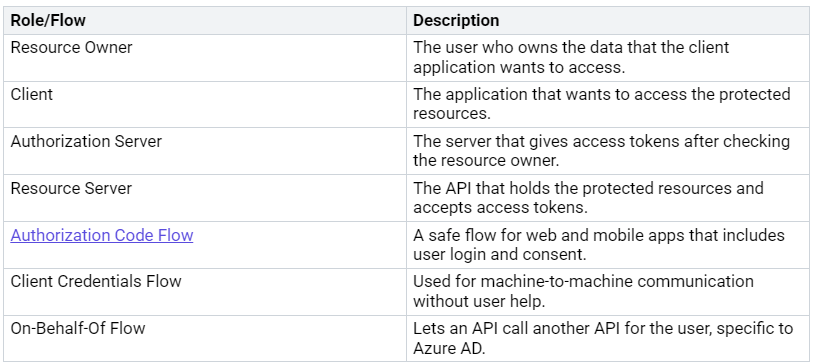
Understanding OAuth 2.0 Basics
Knowing the basics of OAuth 2.0 is key for using Microsoft Entra. Here’s a quick look at the main ideas:
Knowing these ideas will help you go through the app registration process and use secure authentication well.
Entra ID App Registration Steps
Registering your app in Microsoft Entra has some important steps. Follow this guide to make the app registration easy.
Naming Your Application
When you register your app, pick a good name. This name should show what the app does. A clear name helps you and others find the app later. Here are some tips for naming:
Choosing Account Types
Next, you must choose the account types for your app. Microsoft Entra lets you pick between single-tenant and multi-tenant apps.
Single-tenant: This option limits access to users in your organization. Only users from your tenant can log in.
Multi-tenant: This option lets users from other organizations use your app. It needs user or admin approval to create a local Enterprise Application.
Choosing the right account type is very important. It decides who can use your app and how you manage permissions.
Setting Up Redirect URIs
Redirect URIs are very important for logging in. They tell the authentication server where to send users after they log in. Follow these tips when setting up redirect URIs:
Exact Matching: Make sure the redirect URIs match exactly. This stops unauthorized access and keeps things safe.
Limit to Trusted URIs: Only add URIs that your app needs. Too many can create security problems.
Avoid Wildcards: Wildcard URIs can increase risks. Stick to specific URIs to lower dangers.
When you set up your redirect URIs correctly, you make your app safer. The authentication server will only send users to registered URIs, making sure tokens go to the right places.
To sum up the registration steps, here’s a quick checklist:
Go to App registrations and click + New registration.
Type your app’s name and choose the right account type.
Click Register to create the app registration.
Set up your redirect URIs.
Copy the Application (client) ID for later use.
Set API permissions as needed.
By following these steps, you can register your app in Microsoft Entra and get it ready for safe authentication using OAuth 2.0.
Configuring Permissions and Roles
When you set up permissions and roles in Microsoft Entra, you create a safe way for people to access your application. It is important to know the types of permissions for good management.
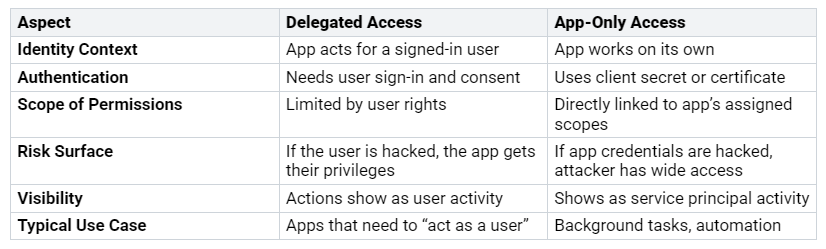
API Permissions
API permissions decide what your application can do with Microsoft services. You can pick between two main types: delegated and application permissions.
To keep security and functionality balanced, follow these tips when setting API permissions:
Use many security controls for better protection.
Keep your API management tools updated with the latest patches.
Regularly check for security issues.
Train developers on API security best practices.
User Roles and Access Control
Managing user roles and access control is very important for security. Here are some good strategies:
Use the least privilege principle. Give users only the permissions they need.
Use groups for role assignments. This makes management easier and improves security.
Create a clear role hierarchy based on job duties.
Regularly checking and watching user activities helps find problems. Teaching users about permission management also helps keep things secure. By using these strategies, you make sure your application stays safe while giving needed access.
Implementing OAuth 2.0
Using OAuth 2.0 is very important for keeping your apps safe. Knowing the different ways to get permission helps you pick the best one for what you need. Each way has its own uses and safety concerns.
Understanding Authorization Flows
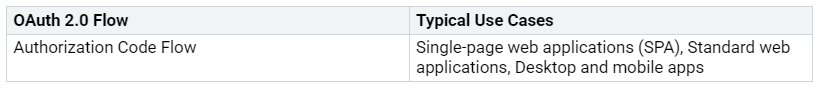
OAuth 2.0 has different ways to get permission. Each way fits different situations and user needs. Here’s a table that shows the main OAuth 2.0 ways and when to use them:
The authorization code flow is the safest choice. It needs users to log in and give permission. This way works well for web and mobile apps.
You should not use the implicit grant flow. This way has safety problems that can put your tokens at risk. The issues happen when tokens are sent using response_mode=fragment. This means the token can be seen by any JavaScript on the page. This could be a problem if the page has third-party scripts. Instead, choose the authorization code flow to make both safety and user experience better.
Token Management and Security
Good token management is key to keeping your app secure. Here are some tips for safe token management in OAuth 2.0 with Microsoft Entra:
Use HTTPS: Encrypt your communications to keep sensitive data, like tokens, safe.
Validate Redirect URIs: Make sure redirect URIs are registered to stop unauthorized access.
Implement PKCE: Use Proof Key for Code Exchange to boost security for public clients.
Conduct Regular Audits: Find and fix setup mistakes by doing frequent security checks.
Secure Token Storage: Keep tokens safe using environment variables and secure storage options.
Handle Tokens Securely: Set reasonable expiration times and have ways to revoke tokens.
By following these tips, you can lower the chances of token theft and unauthorized access. Managing access tokens and ID tokens well keeps your app secure while giving users a smooth experience.
Best Practices for OAuth 2.0
Security Considerations
When using OAuth 2.0, keeping your apps and users safe is very important. Here are some key practices:
Redirect URI Validation: Always set up your authorization server to only allow exact or pre-registered redirect URIs. This stops open redirect problems.
CSRF Protection: Use state parameters and CSRF tokens in all OAuth flows. This helps protect against Cross-Site Request Forgery attacks.
Token Storage: Keep tokens safe. Use HTTP-only cookies or secure places to stop unauthorized access.
Token Leakage Prevention: Don’t put tokens in URLs. Use Referrer-Policy headers to control how much info your app shares with other sites.
A recent security study found that 43% of enterprise OAuth setups have at least one serious security problem. The most common issue is not checking redirect URIs enough, found in 27% of the vulnerable setups.
Performance Optimization Tips
Making performance better is key for handling many token checks and refresh actions. Here are some tips to improve your OAuth 2.0 setup:
Single App Registration: Make one app registration for all APIs. This lets clients get one token for many APIs, making things easier.
Multiple App Registrations: Or, create different app registrations for each API. This gives smaller JWT tokens but means clients must handle many tokens.
Client Authentication Methods: Use managed identities for Azure resources or certificates for better security. Change client secrets often to keep security strong.
Using OAuth-protected APIs in Microsoft Azure API Management can also boost security and management. This method provides infrastructure as code for easy setup and role-based security for better access control.
By following these best practices, you can make sure your OAuth 2.0 setup is safe and works well for your apps.
Troubleshooting Common Issues
When you use Microsoft Entra app registration and OAuth 2.0, you might run into some problems. Knowing common errors and how to fix them can help you solve issues quickly.
Common Errors and Solutions
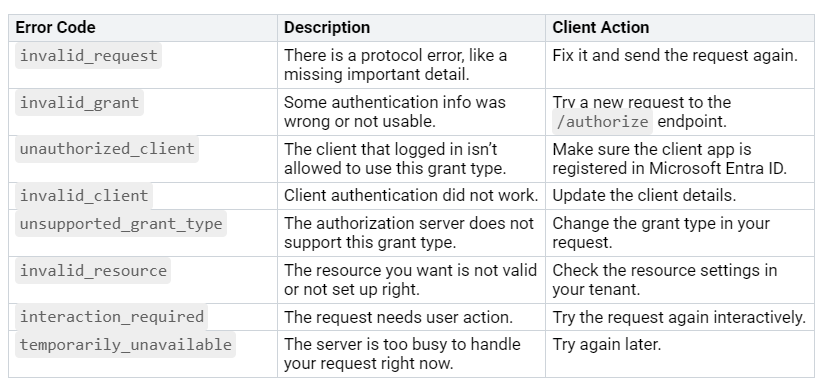
Here are some common error codes you may see during app registration or OAuth 2.0 setup, along with what they mean and what you can do:
Debugging Tips
If you have trouble with authentication, follow these steps to troubleshoot well:
Take notes about your experience: Write down important details like error messages, username, time of the issue, URL or app used, and device info.
Find where the problem happens in the expected authentication flow: Compare your sign-in experience to the expected flow to see where it goes wrong.
Also, use diagnostic tools to help you fix issues. For example, check the Event Viewer for logs about Microsoft Entra. Look for entries under Applications and Services Log > Microsoft > Windows > AAD. This can give you clues about the authentication process and help you find specific errors.
By knowing these common errors and using the debugging tips, you can fix problems faster and have a better experience with Microsoft Entra app registration and OAuth 2.0.
Learning about Entra ID app registration and OAuth 2.0 is very important for making your apps safe and effective. Here are some main points to remember:
Know the challenges of using different platforms for successful connections.
Handle permissions well to fit with Microsoft’s identity system.
Understand the details of OAuth 2.0, especially in Business Central.
By paying attention to these points, you improve your organization’s security and make sure your apps work well. Use these practices to create safe and strong connections.
FAQ
What is Entra ID app registration?
Entra ID app registration helps you make and control apps that work safely with Microsoft services.
Why is OAuth 2.0 important?
OAuth 2.0 gives safe permission for apps. It lets users allow access without giving out their passwords.
How do I troubleshoot common OAuth errors?
Look at error codes, check redirect URIs, and check your app’s permissions to fix common OAuth problems fast.