In today’s online world, email and collaboration tools are big targets for cyber threats. You deal with many phishing attacks, malware, and impersonation attempts. The growth of smart threats needs better solutions to keep your organization safe. Microsoft Defender for Office 365 helps with these problems using strong security features.
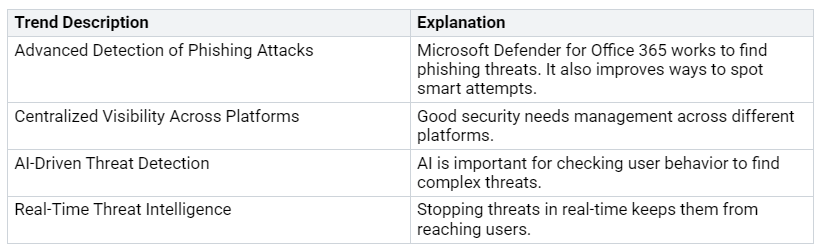
Look at these new trends in email and collaboration security:
Your organization’s security depends on good solutions that change with these new threats.
Key Takeaways
Microsoft Defender for Office 365 gives strong protection against phishing and malware. This helps keep your organization safe from online dangers.
Use Safe Links and Safe Attachments to check all email content for safety. This reduces the chance of harmful clicks.
Set up data loss prevention (DLP) rules to protect sensitive information. This stops unauthorized sharing in your organization.
Use real-time monitoring and reporting tools to stay informed about possible threats. This helps you respond quickly to security problems.
Teach users and run phishing tests to help your team spot and deal with cyber threats well.
Microsoft Defender Threat Protection
Microsoft Defender for Office 365 has strong advanced threat protection features. These features help keep your organization safe from changing cyber threats. They work together to create a multi-layered plan for email security. This helps you fight against phishing, malware, and other harmful activities.
Advanced Threat Features
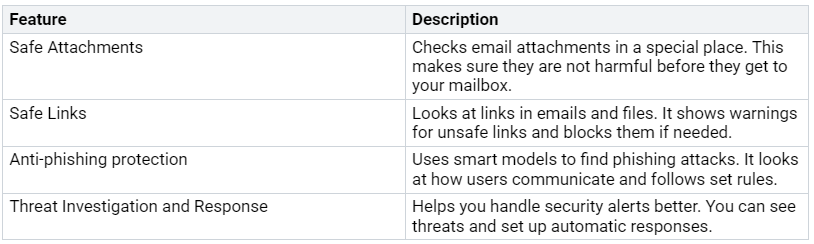
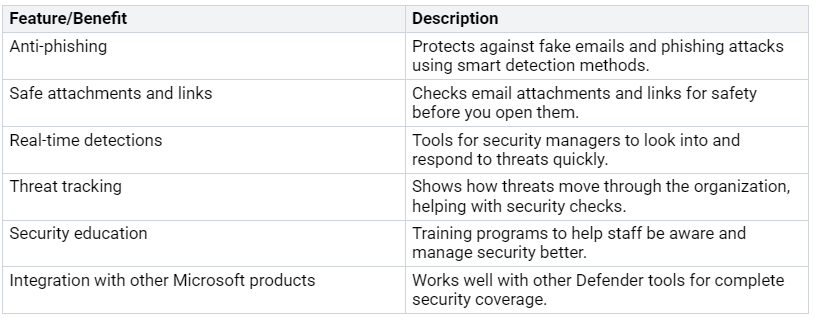
The advanced threat protection features of Microsoft Defender include:
These features work together to improve your email protection plan. For example, the anti-phishing protection uses smart systems to study communication patterns. This helps find possible phishing attempts that might be missed.
Also, Microsoft Defender gives real-time protection against zero-day malware. This means it can find and stop new threats before they cause damage. The automatic investigation and response features help control and fix the effects of cyberattacks. This keeps your organization safe.
Safe Links and Attachments
Safe Links and Safe Attachments are key parts of Microsoft Defender’s plan to fight phishing and malware threats. Here’s how they work:
Safe Links changes links in emails to make sure they are safe before they get to your inbox. This feature checks URLs from incoming emails against known phishing sites. If a link is unsafe, it gets blocked. This stops users from accidentally clicking on harmful content.
Safe Attachments opens files in a safe environment to check for harmful content. Incoming emails are checked for dangerous attachments. Any suspicious files are opened in a secure place. This process makes sure harmful files do not reach your users.
The success of these features is clear in the numbers. Microsoft Defender for Office 365 blocks almost 40 million emails with business email compromise (BEC) tactics every month. It also stops 100 million emails with harmful credential phishing links each month. This level of protection is very important today with many advanced email threats.
By using these advanced cybersecurity features, you can greatly lower the risk of problems and improve your organization’s overall security.
Data Protection Strategies
Data protection is very important. It helps keep sensitive information safe and private. Microsoft Defender for Office 365 has strong strategies to help you protect your data well.
Policy Configuration
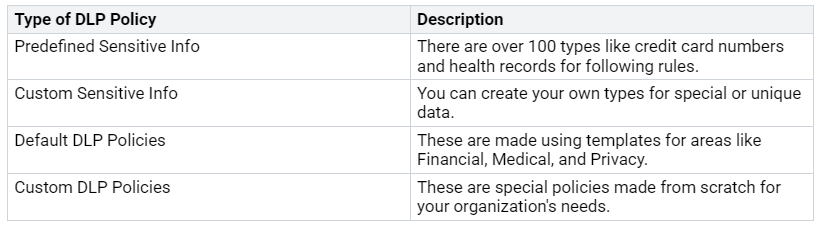
You can set up different data loss prevention (DLP) policies to keep sensitive information safe. These policies stop unauthorized sharing and help you follow rules. Here are some types of DLP policies you can use:
To make these policies, do these steps:
Go to the Policies section in Microsoft 365 Compliance Center.
Click on Data Loss Prevention and then on the Policies tab.
Choose to create a Default or Custom DLP policy.
Pick the right template or change your policy settings.
By using these policies, you can watch and control who sees sensitive documents. Working with Microsoft Information Protection helps you sort and manage data. This makes sure only allowed users can see sensitive information, which lowers the chance of data leaks.
Monitoring and Reporting
The monitoring and reporting tools in Microsoft Defender for Office 365 give you real-time updates about your organization’s security. You can keep an eye on important issues and act fast on possible threats. Here are some key features:
Real-time reports and updates for tracking important issues.
Threat Explorer to find and study recent threats.
Real-time detections to check threats from the last seven days.
Threat Trackers that give information on cybersecurity problems.
Automated investigation and response tools for managing threats easily.
Attack simulation training to help with phishing risks.
These tools keep you updated on new threats and weaknesses. You can set up data exposure policies to watch for and alert on unauthorized sharing of sensitive data. Also, blocking the sharing of confidential data with outside users stops data leaks.
By using these monitoring and reporting tools, you can improve your organization’s overall cybersecurity plan. This proactive way helps you deal with advanced social engineering threats, ransomware, and insider threats effectively.
Microsoft Defender Integration
Microsoft Defender for Office 365 works well with Microsoft 365. This helps improve your overall email security plan. This connection makes sure you get complete protection across all Microsoft services. Here’s how it works:
The benefits of this connection are important. You get full coverage in the Microsoft environment. This means better and coordinated protection across devices, apps, and data sources. Smart protection uses AI and machine learning for real-time threat detection. This improves your proactive security measures.
Automating monitoring and incident response helps reduce response times. It also makes things more efficient through automatic threat resolution. Plus, centralized management gives you a clear view of security operations across different platforms. Finally, threat intelligence uses AI to quickly spot and deal with new threats by analyzing data from many sources.
Compatibility with Microsoft 365
The compatibility of Microsoft Defender for Office 365 with Microsoft 365 is key for strong cybersecurity. This connection lets you use the full power of both platforms. You can manage security settings and policies from one place, making your work easier.
Also, Microsoft Defender for Office 365 works well with other Microsoft security tools. For example, it connects with Microsoft Defender for Endpoint to improve security by using endpoint data to find threats. It also teams up with Microsoft Defender for Identity to protect user credentials and stop spear phishing attacks. Additionally, it works with Microsoft Defender for Cloud Apps to watch over and secure cloud resources against suspicious access.
Third-Party Integrations
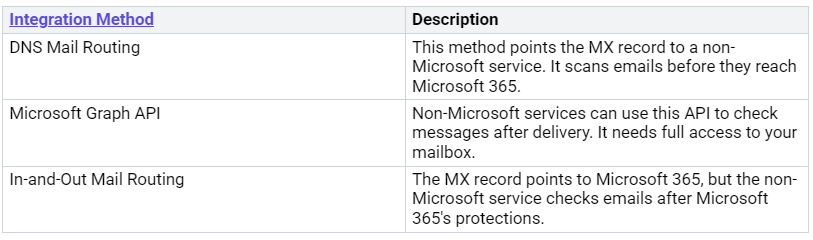
While Microsoft Defender for Office 365 is great with Microsoft 365, you might want to connect it with third-party platforms too. But challenges can come up during this process. Here are some common issues you might face:
Compatibility problems with third-party security solutions.
Performance issues that may happen when using multiple security tools.
Managing overlapping security features that can make things confusing.
To successfully connect Microsoft Defender for Office 365 with third-party services, consider these steps:
Check if your current security tools work with Microsoft Defender.
Watch performance to make sure the connection does not slow down your systems.
Manage overlapping features carefully to avoid confusion and keep a clear security plan.
By solving these challenges, you can improve your cybersecurity setup while using the strengths of both Microsoft Defender for Office 365 and third-party solutions.
User Education and Awareness
Teaching users is very important for keeping your organization safe. Microsoft Defender for Office 365 provides many training tools. These tools help you and your team spot and deal with cyber threats.
Training Resources
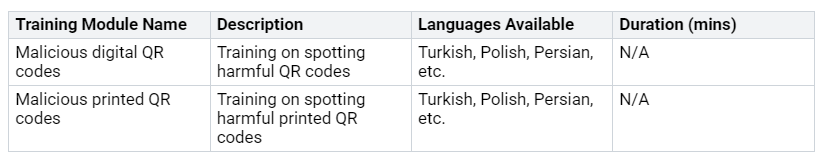
You can find different training modules that help you learn about possible threats. Here are some important resources you can use:
These modules help you learn about Microsoft Defender for Office 365 and how it protects you. You will find out how to spot and fix attacks while getting to know the Microsoft Defender portal.
Phishing Simulation
Phishing simulations are very important for lowering successful phishing attacks. These tools check how vulnerable employees are and give them real experiences. Here’s how they work:
Realistic simulations let employees feel what a phishing attack is like.
Targeted training based on simulation results helps employees be more aware and strong against phishing threats.
After running simulations, organizations get detailed reports about user responses. These reports show where improvements are needed. This helps you see how well your training programs work. By focusing on user education, you can greatly lower risks from phishing, spear-phishing attacks, and business email compromise.
Adding user education to your security plan not only helps your team but also makes your overall email security stronger.
In short, Microsoft Defender for Office 365 gives strong protection for your email and teamwork tools. You get important features that make your security better, like:
You can see how these features work through dashboards that show user protection and threat handling. This complete plan helps you stay ahead of new cyber threats.
FAQ
What is Microsoft Defender for Office 365?
Microsoft Defender for Office 365 is a security tool. It protects your email and teamwork tools from dangers like phishing, malware, and impersonation. It has advanced features to keep your organization’s data safe.
How does Safe Links work?
Safe Links checks links in emails and documents right away. It blocks unsafe links before they get to your inbox. This stops you from accidentally clicking on harmful content.
Can I customize data loss prevention policies?
Yes, you can make custom data loss prevention (DLP) policies for your organization. This helps you keep sensitive information safe and follow rules.
What training resources are available for users?
Microsoft Defender for Office 365 has many training modules. These resources help users spot threats and boost their cybersecurity knowledge.
How does Microsoft Defender integrate with other tools?
Microsoft Defender for Office 365 works well with Microsoft 365 and other Microsoft security tools. This connection improves your overall security and gives complete protection across platforms.