The workplace has changed. Old ways of managing devices do not work for today’s companies. You deal with problems from remote work and more devices using company data. Microsoft Intune provides a solution by focusing on security based on identity. This method improves your organization’s security, lowering the chances of breaches and failed audits. As fields like finance and healthcare use Intune, you can adjust security to fit your needs. With 96% of users happy, Intune is a trustworthy option for keeping your digital space safe.
Key Takeaways
Microsoft Intune changes security focus from devices to users. This helps protect against breaches better.
More remote work means we need security based on identity. It is important to control access from different devices.
Unified Endpoint Management (UEM) in Intune makes security easier. It combines protection for devices, apps, and data.
Dynamic conditional access lets organizations limit access to resources. This is based on real-time risks, so only trusted users can connect.
Using Zero Trust principles with Intune makes security stronger. It keeps checking user identities and device health all the time.
Endpoint Management Evolution
From Device-Centric to Identity-Centric
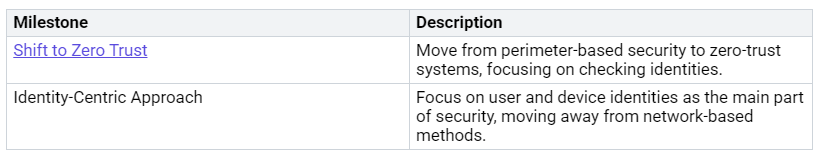
The way we manage devices has changed a lot. Old device management focused on keeping hardware and networks safe. This method often did not work well in today’s fast-changing world. You faced problems like lost devices and stolen passwords. These issues showed that we need a stronger security plan.
The move to identity-centric security solves these problems. This plan focuses on checking who the user is instead of just securing devices. You can now create rules that change based on the user, where they are, and how healthy their device is. This change fits with Zero Trust ideas, which believe threats can come from inside and outside the network.
Here are some key milestones in this evolution:
The Role of Remote Work
Remote work has sped up the use of identity-focused security plans. A Gallup poll from October 2020 showed that 58% of Americans worked from home sometimes or all the time. This change made companies rethink their security plans. You now have to control access to company resources from many personal devices.
The rise of remote work has created several challenges:
Harder to control who can access the network.
Compliance problems because of different device types.
A strong need to keep checking user identities.
As you deal with this new situation, using an identity-driven security plan is very important. This method not only improves security but also helps with the flexibility that remote work needs.
Microsoft Intune’s Holistic Security Framework
Microsoft Intune gives a complete way to keep things safe. It combines device, application, and data protection into one system. This helps you manage security for all devices easily. It makes sure your organization stays strong against threats.
Unified Endpoint Management
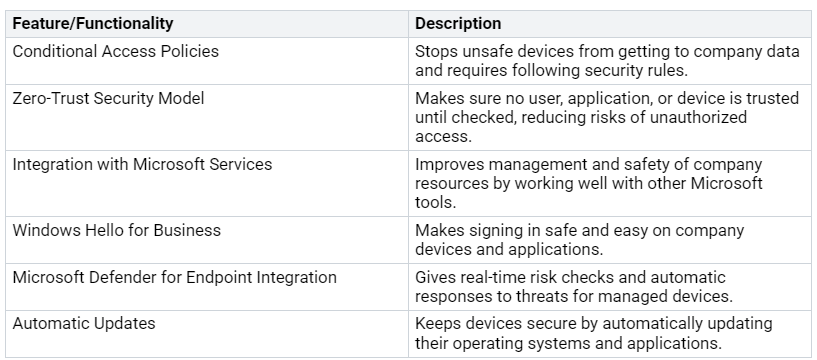
Unified endpoint management (UEM) is an important part of Microsoft Intune. It offers protection for devices, applications, and data all together. With UEM, you can watch and control all devices from one place. This helps you see how devices work and how applications are used. You can fix problems before they turn into security issues.
Here are some key features of UEM in Microsoft Intune:
By using these features, you can lower security problems a lot. UEM tools keep an eye on device activities, spotting strange actions and possible threats. This active approach helps stop security breaches and keeps your organization following rules.
Dynamic Conditional Access
Dynamic conditional access is another key part of Microsoft Intune’s security system. This feature boosts safety for remote and hybrid workers. It lets you limit access to resources based on different factors. You can set rules that change based on real-time risks, making sure only trusted users and devices can see sensitive data.
Here are some benefits of dynamic conditional access:
It lets organizations limit access based on device safety, user location, and identity checks.
IT staff can use multi-factor authentication (MFA) for extra security against unauthorized access.
Device checks make sure devices meet safety standards before they can connect to the network.
With these smart security features, you can manage access to your organization’s resources safely, even when working remotely. Microsoft Intune’s holistic security framework works well for small and medium businesses and also fits large companies. This flexibility helps you change your security as your organization grows.
Zero Trust Security with Intune
Zero Trust security is a new way to think about safety. It believes that threats can come from inside or outside your organization. This approach focuses on always checking who the user is and how healthy their device is. Microsoft Intune is very important for using Zero Trust ideas. It helps keep your organization safe in a changing world.
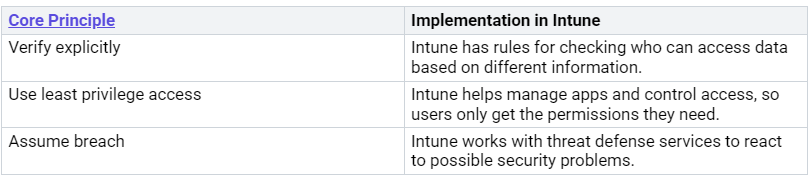
Identity and Risk-Based Policies
Knowing about identity and risk-based policies is key to protecting your company’s resources. These policies help you control access based on who the user is and how risky their device is. Here are the main ideas of Zero Trust and how Intune uses them:
By following these ideas, you can lower the chances of unauthorized access to important data. For example, Microsoft Intune works with Microsoft Entra ID Conditional Access to control who can access company resources based on device safety. This means only devices that meet certain security rules, like having encryption and approved operating systems, can use sensitive apps like Microsoft 365.
Protecting Corporate Data
To protect corporate data well, you should use best practices with Microsoft Intune. Here are some important strategies:
Set up endpoint security policies.
Create device configuration policies.
Make device compliance policies to reach security goals.
You can also set rules that only let safe devices connect to the network. It’s important to limit access to resources like file shares and company email. Also, protecting corporate credentials stops unauthorized access. Make sure devices follow security rules through compliance checks, and use strong authentication, device encryption, and safe app management.
Regular security checks help find weaknesses. Updating Intune settings and policies to match current security needs is very important.
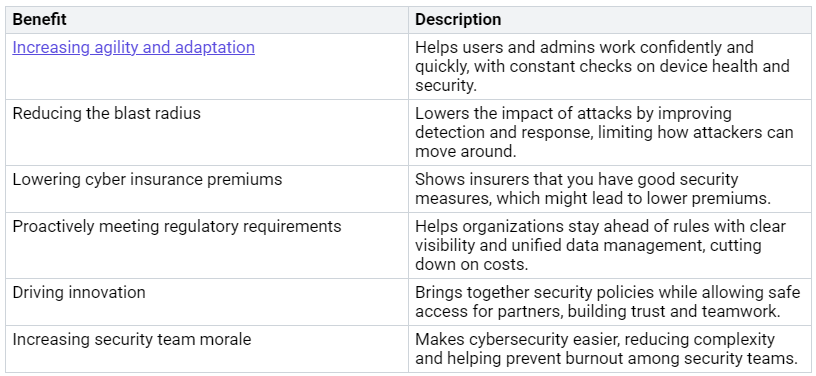
The clear benefits of using Zero Trust security with Microsoft Intune include:
By using these practices, you can build a strong security system that protects your data and makes your organization more resilient against cyber threats.
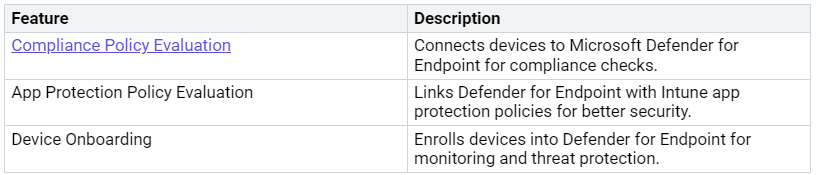
Integration with Microsoft Defender and Purview
Microsoft Intune works well with Microsoft Defender and Purview. This helps make your organization’s security and compliance better. The integration gives you advanced threat information and checks for compliance all the time. These are very important in today’s digital world.
Advanced Threat Intelligence
With Microsoft Defender, you get advanced threat information. This helps you find and deal with possible security threats. The integration allows you to monitor and detect threats in real-time across your devices. Here are some key features of this integration:
This advanced threat information helps you act fast against possible breaches. It makes sure your organization stays safe.
Compliance Oversight
Compliance is very important for organizations, especially in regulated industries. Microsoft Purview improves compliance checks by giving you tools for data management and compliance. These tools help you handle sensitive information well. Key benefits include:
Communication Compliance: Finds and manages risks in email and Microsoft Teams messages.
Data Lifecycle Management: Provides tools for keeping and deleting content across different Microsoft services.
eDiscovery: Lets you search data across many platforms, helping with compliance and oversight.
Also, Microsoft Intune offers real-time compliance checks. This feature helps you quickly find and fix compliance problems. Automated compliance checks help you follow rules, lowering the chance of penalties. You can also create detailed reports that show compliance trends, helping you make better decisions.
Microsoft Intune is very important for improving security and following rules in organizations. When you use Intune, you get tools that keep sensitive data safe on devices and apps. It makes managing devices easier, so you can watch and protect endpoints better. Intune also helps remote workers by making sure they can safely access company resources.
Here are some main benefits:
Easier Device Management
Help for Remote Workers
Adding Microsoft Intune to your security plan helps your organization succeed in today’s digital world. Use Intune as a key part of a safe digital workplace.
FAQ
What is Microsoft Intune?
Microsoft Intune is a cloud service. It helps you manage devices, apps, and data security. You can set security rules and check compliance on different devices in your organization.
How does Intune support remote work?
Intune allows safe access to company resources from anywhere. It uses identity-based security measures. This means only approved users and safe devices can reach sensitive data.
Can Intune manage personal devices?
Yes, Intune supports Bring Your Own Device (BYOD) rules. You can manage personal devices while keeping corporate data safe. This way, employees can keep their privacy.
What is dynamic conditional access?
Dynamic conditional access is a feature that limits access to resources. It uses real-time risk checks. It looks at user identity, device health, and location to ensure safe access.
How does Intune integrate with other Microsoft services?
Intune works well with Microsoft Defender and Purview. This connection improves threat detection, compliance checks, and overall security management for your organization’s digital space.