In today’s digital world, using a Zero Trust security model is very important. Organizations need to change their security plans to protect important business data well. Recent data shows that 51% of IT leaders and C-Suite companies have started using this method. Adoption rates have grown a lot in the last few years. Modern Authentication is key in this change, particularly within Microsoft 365. It offers tools like Azure Active Directory Conditional Access and Microsoft Defender for Endpoint. These tools help you manage access, watch for threats, and make sure there is strong data protection. You must always assume breach in this environment.
Key Takeaways
Use a Zero Trust security model to keep your data safe. Always check users and devices before letting them in.
Use Modern Authentication in Microsoft 365 to make security better. Features like Multi-Factor Authentication and Single Sign-On help protect you more.
Regularly check user access and permissions to stop permission creep. Make sure users only see the data they need.
Use Conditional Access policies to make smart choices about access. This is based on user behavior and device health.
Think about using passwordless sign-in methods. This can make security better and help users. It also lowers the chance of credential theft.
Understanding Zero Trust
Zero Trust is a security plan made to solve today’s cybersecurity problems. It works on the idea of “never trust, always verify.” This means you should always check users and devices before letting them access important data. In a world where cyber threats keep changing, this method is very important for keeping your organization safe.
Zero Trust Principles
The main ideas of the Zero Trust security plan include:
Never Trust, Always Verify: You must check all users and devices before giving access to information.
Least Privilege Access: Give workers only the access they need to do their jobs. This helps reduce risks and limits damage.
Micro-Segmentation: Divide your IT setup into smaller, separate parts. This stops threats from spreading and makes security better.
Continuous Monitoring & Validation: Use tools to check behavior and find unusual activities. These tools help spot suspicious actions right away.
Data-Centric Security: Make sure your data is encrypted, sorted, and only available to authorized people.
By following these ideas, you build a strong security system that changes with new threats.
Benefits of Zero Trust
Using a Zero Trust security plan has many benefits for organizations. Here are some clear advantages:
These benefits show how Zero Trust not only makes security better but also helps work get done more efficiently. According to Gartner, 90% of cybersecurity leaders say that using Zero Trust has made them stronger against modern attacks and helps them recover faster after an incident.
Modern Authentication in Microsoft 365
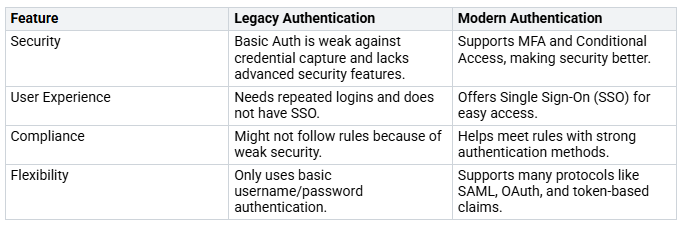
Modern authentication is a big change from old ways of logging in. Organizations need to stop using basic authentication. This method uses simple usernames and passwords. It makes you vulnerable to security risks like credential capture and phishing attacks. Instead, you should use modern authentication. It improves security and makes it easier for users.
Enforcing Modern Authentication
To use modern authentication in Microsoft 365, focus on these important features:
Enhanced Security: Modern authentication includes Multi-Factor Authentication (MFA) and Conditional Access policies. These features help check who the user is and control access based on certain rules.
User Experience: With Single Sign-On (SSO), users can log in once to access many apps. This makes things easier and less frustrating for them.
Compliance: Modern authentication helps meet rules and regulations. Strong authentication methods keep you in line with industry standards.
Flexibility: Modern authentication works with different identity providers and supports many ways to log in, like SAML and OAuth.
Here’s a comparison of old and modern authentication:
Phishing-Resistant Methods
Phishing attacks are still a big threat to organizations. To fight this, you should use phishing-resistant authentication methods. Here are some good options:
FIDO2 Security Keys: These hardware keys give strong authentication without showing your credentials.
Windows Hello for Business: This feature lets users log in using their fingerprints or facial recognition.
Certificate-Based Authentication: This method uses digital certificates to check who the user is, adding extra security.
By using these methods, you make your organization’s security stronger and protect sensitive data from unauthorized access.
Security Challenges in Microsoft 365
Organizations have many security problems when using Microsoft 365. Knowing these problems helps you make your security stronger.
Addressing Legacy Authentication Risks
Legacy authentication brings big risks to your Microsoft 365 setup. This method does not support modern security tools like multi-factor authentication (MFA). Because of this, your organization is open to many attacks. For example, over 99% of password spray attacks and 97% of credential stuffing attacks come from legacy authentication methods. Azure AD accounts that use legacy authentication are 67% more likely to be hacked than those that do not.
To reduce these risks, you should stop using legacy authentication. Switching to modern authentication methods makes security better and keeps sensitive data safe from unauthorized access.
Managing Device Sprawl
Device sprawl is another big problem in Microsoft 365. As employees use many devices for work, it gets hard to keep track of them. This lack of control can create security holes.
You must regularly check user access to manage privileges and access well. Poor management can lead to sensitive data leaks and unauthorized access. Here are some common risks linked to device sprawl:
Open security holes because of lack of control.
More risk and complexity from too many privileges and access.
Chance of unauthorized access to sensitive data.
By solving these problems, you can build a safer Microsoft 365 environment that follows zero trust ideas. Using strong identity and device access controls will help you protect your organization’s data better.
Implementing Conditional Access
Conditional access is very important in a Zero Trust model. It works like a policy engine that uses different identity signals to make smart access decisions. This way, you check who users are and give access based on the least privilege needed. By doing this, you can better handle possible security problems.
Role-Based Access Control
Role-Based Access Control (RBAC) is key for managing permissions in Microsoft 365. It lets you give access rights based on user roles. Here are some good practices for using RBAC:
Apply the principle of least privilege: Only give users the permissions they need for their tasks.
Limit the number of Global Administrators: Keep this number under five to lower risks.
Restrict privileged role assignments: Limit these to fewer than ten to stop privilege escalation.
Use groups for role assignments: Assign roles to groups instead of individuals for easier management.
Activate multiple roles using Privileged Identity Management (PIM): This helps productivity while keeping security strong.
Utilize cloud-native accounts: Avoid using on-premises accounts for role assignments to lower security risks.
By following these practices, you can improve your security and make identity and access management easier.
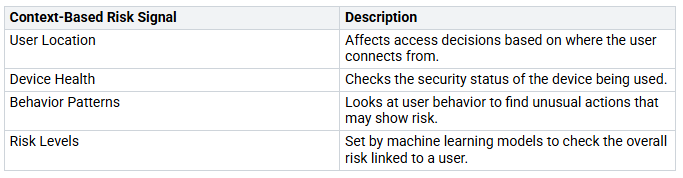
Context-Based Risk Signals
Context-based risk signals are important for creating conditional access policies. These signals help you check the risk linked to user actions. Here are some useful context-based risk signals:
You can set up conditional access policies using these signals. For example, if an employee logs in from a work laptop in the office, access is granted easily. But if the same employee tries to log in from a personal device at an airport, multifactor authentication (MFA) is needed. If there are strange sign-ins from unknown places, you might deny access or require MFA.
By using context-based risk signals, you can build a safer environment that follows Zero Trust ideas.
Advanced Security Capabilities
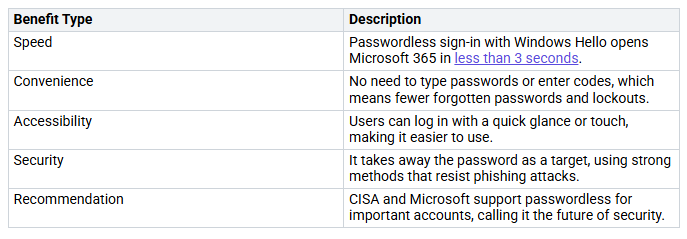
Passwordless Sign-In
Passwordless sign-in is a big change for Microsoft 365 users. It makes security better and helps users. Here are some important benefits of using passwordless sign-in:
By using passwordless sign-in, you make access easier and lower the risk of losing credentials.
Identity Protection Strategies
Protecting identities is very important in a zero trust setup. Microsoft 365 has strong identity protection strategies to help find and stop identity threats. Here are some key features:
Centralized Identity Threat View: This shows a complete view of identity risks and security tips.
Insights into Suspicious Activity: It shows data for risks like stolen credentials and strange admin actions.
Highlights At-Risk Identities: The system finds users with high privileges or unusual behavior.
Correlates Multiple Signals: It connects identity data with device and network activity for better threat analysis.
Enables Quick Response: This feature makes detection faster and helps with incident investigation.
To improve your identity protection, think about these strategies:
Prevent identity attacks: Use a modern identity and access management solution.
Reduce response time: Combine information from all identity sources into one view.
Stop identity attacks: Use automatic tools to stop lateral movement.
Establish behavior baselines: Find changes using user and entity behavior analytics (UEBA).
Correlate alerts: Give a full view of the cyberattack chain.
Also, Privileged Identity Management (PIM) is important for lowering insider threats. PIM enforces strict access rules, limiting how long and how much access users have. It checks privileged sessions often, giving detailed logs to find suspicious actions. Just-In-Time (JIT) access gives privileges only when needed, lowering chances for misuse.
By using these advanced security features, you can greatly improve your organization’s security and protect sensitive data well.
Governance and Monitoring
Good governance and monitoring are very important for keeping Microsoft 365 safe. Regular audits and reviews help you follow rules and protect sensitive data. By watching user activities and permissions, you can find security risks before they get worse.
Audit Logs and Reporting
Audit logs keep a detailed record of what users do in Microsoft 365. Checking these logs often is key for compliance and security. Keeping logs for more than three months is usually not enough because threats change. Organizations should set their log retention based on specific compliance needs. Here’s a quick reference for compliance standards:
By automating monitoring, you can save time and lower the chance of mistakes. Automation helps enforce governance rules consistently and reduces compliance risks. For example, automated reporting gives insights into usage and security, making audits easier.
Preventing Permission Creep
Permission creep happens when users gain too many access rights over time, often more than they need. This can create security problems. To stop permission creep, think about these effective strategies:
Implement a Least-Privilege Model: Use least-privilege rules in your Microsoft 365 setup. Make sure new sites and content have limited access permissions.
Standardize Permission Structures: Create clear, role-based access control models. This helps reduce hidden permission issues and keeps permission management consistent.
Utilize Access Reviews and Recertification: Do regular checks, like quarterly reviews and yearly recertification. This helps keep the right access permissions and remove unnecessary rights.
By following these practices, you can make your security stronger and ensure users only access the data they need. This method fits with zero trust ideas, where you always check and confirm user access.
In conclusion, building a Zero Trust base in Microsoft 365 is very important for making your organization safer. Pay attention to important areas like managing users and identities, keeping an eye on activities, and responding to incidents to check how you are doing. Take clear steps to create this base by doing security checks, setting rules, and training employees. By following these steps, you can greatly boost your data safety and meet compliance needs. Always remember, being proactive about security helps you stay ahead of dangers and keeps your organization safer.
FAQ
What is Zero Trust in Microsoft 365?
Zero Trust is a security plan that checks every user and device trying to access resources. It believes that threats can be inside or outside the network. So, you must always check before giving access.
How does Modern Authentication enhance security?
Modern Authentication makes security better by using methods like Multi-Factor Authentication (MFA) and Conditional Access. These features help you confirm who the user is and control access based on certain rules. This reduces the chance of unauthorized access.
Why is managing device access important?
Managing device access is very important because employees often use many devices for work. Without proper controls, this can create security problems. You need to make sure that only safe devices can access sensitive data.
What are the benefits of passwordless sign-in?
Passwordless sign-in improves security by getting rid of passwords, which are often targeted in attacks. It allows faster access through methods like fingerprints and security keys. This makes it easier for users while keeping strong protection.
How can I ensure compliance in Microsoft 365?
To ensure compliance in Microsoft 365, regularly check access permissions and do audits. Use tools like audit logs and automated reporting to watch user activities and keep up with rules and regulations.