In today’s fast digital world, precision and segmentation are very important for zero-touch deployment. By changing deployment plans to fit user needs, you make sure everyone gets the right tools and apps. This method helps people work better and makes security stronger. For example, data shows that good segmentation can give a precision score of 0.88. This greatly improves deployment results.
By focusing on what users need, you can lower compliance risks and improve security overall.
Key Takeaways
Precision in zero-touch deployment makes sure users get the right tools and apps. This helps them work better and stay safe.
Role-based policies control user access to needed resources. This can cut security breaches by up to 50%.
Dynamic Azure AD groups change user access automatically. This makes deployment easier and cuts down on admin work.
Microsegmentation improves security by splitting networks into smaller parts. This stops unauthorized access and movement.
Using zero trust principles means only verified users can reach sensitive resources. This lowers security risks.
Precision in Zero-Touch Deployment
Precision is very important in zero-touch deployment. It helps you change the deployment process to fit different user groups. When you use precise strategies, you can make deployment much more successful.
Role-Based Policies
Role-based policies are key for getting precision in zero-touch deployment. These policies let you set access controls based on user roles. This way, you can lower the chances of mistakes and security problems. Here are some main benefits of using role-based access control (RBAC):
RBAC can cut security breaches by up to 50% by limiting user access to what they need.
It can lower unauthorized access risks by about 40% with strict role checks.
Automated logging with RBAC can speed up incident response times by 40-50%, helping to find and fix security issues faster.
By using role-based policies, you make a safer environment. This method makes sure users get only the apps and tools they need. This reduces compliance risks and boosts overall productivity.
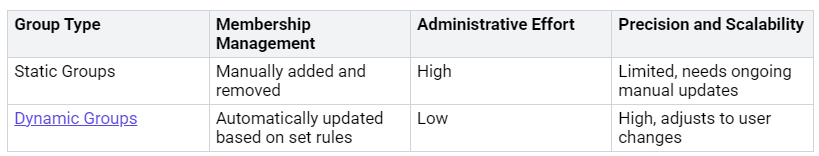
Dynamic Azure AD Groups
Dynamic Azure AD groups also improve precision and scalability in zero-touch deployment. These groups automatically change membership based on set rules. This cuts down on administrative work and makes things more efficient.
Dynamic Azure AD groups help you react quickly to changes in your organization. When users join or leave, the system automatically changes their access rights. This flexibility keeps your deployment precise and relevant to the current workforce.
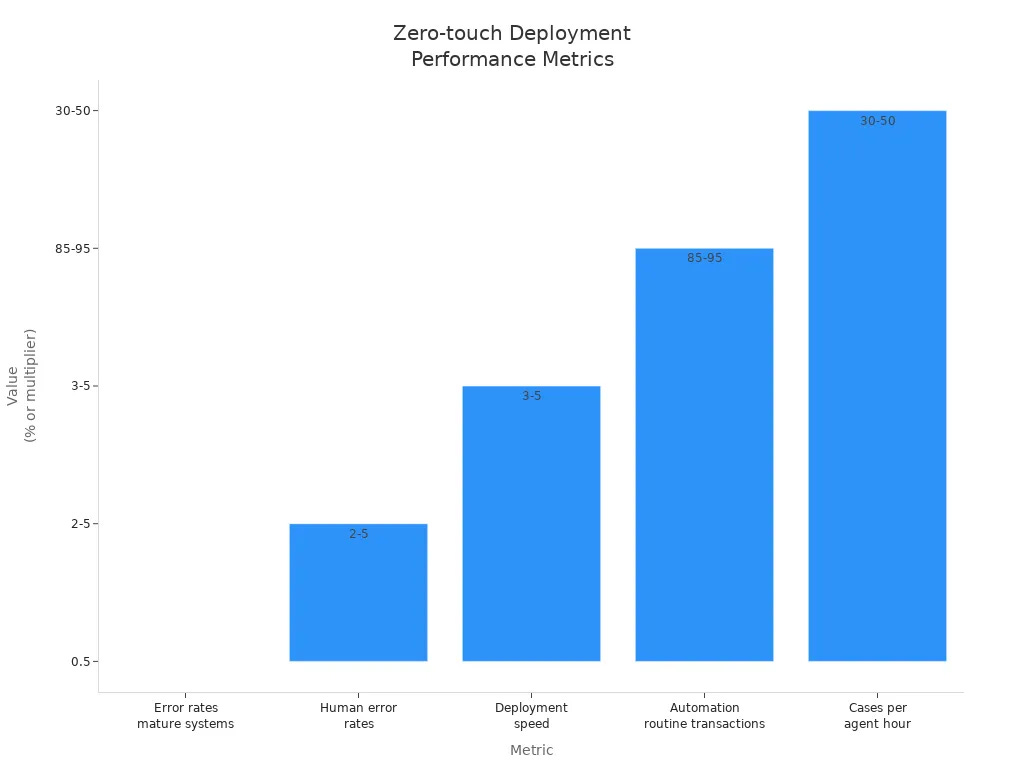
The effect of precision on deployment success is very important. Metrics show that advanced zero-touch systems have error rates below 0.5%. In comparison, human error rates are usually between 2-5%. Also, zero-touch platforms deploy 3-5 times faster than traditional methods. Automation for routine tasks can reach 85-95%, which boosts the number of cases handled per agent hour by 30-50%.
By focusing on precision with role-based policies and dynamic Azure AD groups, you can make your zero-touch deployment a smooth and efficient process that meets the different needs of your users.
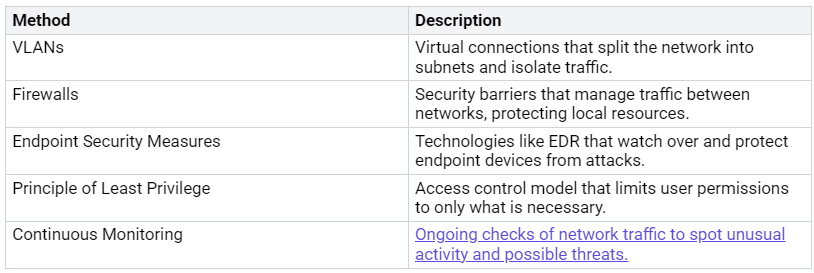
Microsegmentation for Enhanced Security
Microsegmentation is a way to improve cybersecurity. It divides a network into smaller, separate parts. Each part works as its own security zone. This method reduces the risk of attacks and stops hackers from moving around the network. In zero-touch deployment, microsegmentation is very important for better security.
Individualized Security Controls
Individualized security controls make protection stronger in zero-touch deployment. These controls use advanced security features like those from trusted Certificate Authorities. Here are some main points about individualized security controls:
They follow federal security rules like FedRAMP and FIPS 140.
The system uses FIPS 140-2 Level 3 certified Hardware Security Modules (HSMs) to meet rules.
There is constant physical security monitoring to keep the Public Key Infrastructure (PKI) safe.
Using individualized security controls in segmented networks needs different strategies. You can set edge perimeters, use demilitarized zones (DMZs) for app safety, and create micro-segmentation in private networks. These strategies help stop unauthorized access and keep communication safe between segments.
Application Clustering
Application clustering also boosts security in zero-touch deployment. This method groups applications based on their security needs and how they operate. By clustering applications, you can use specific security measures for each group.
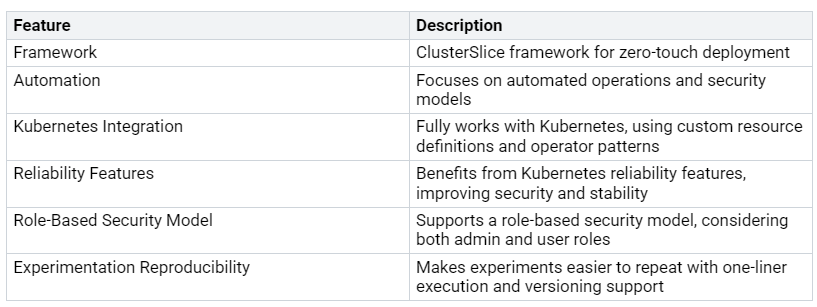
The ClusterSlice framework for zero-touch deployment focuses on automated operations and security models. It works well with Kubernetes, using custom resource definitions and operator patterns. This connection improves security and stability. Here are some features of application clustering:
By using micro-segmentation and application clustering, you greatly improve your security. These strategies help guard against data breaches and keep your zero-touch deployment strong against new threats.
Best Practices for Zero Trust Security
Setting up zero trust security needs careful planning and action. You should pay attention to best practices that make your security stronger and lower risks.
Conditional Access Layers
Conditional access layers are very important for improving security. They make sure that only allowed users can access sensitive resources. Here are some main benefits of using conditional access:
Strict access controls: Every access attempt is checked to confirm permission.
Regular monitoring: You can watch access behaviors to find unusual activities quickly.
Dynamic policies: Change access permissions based on new threats to improve your security.
Also, checking user identity before giving access is very important. This step makes sure that only real users can access sensitive resources. You should enforce device compliance to stop unauthorized devices from connecting to your network. Adding location limits gives extra security by controlling access based on where users are.
Compliance and Risk Management
Compliance and risk management are key parts of zero trust architecture. You must keep checking your security measures to make sure they follow rules. Regular audits help find gaps in your security setup.
Pilot testing is a good way to improve your zero trust plans. You can run pilot projects to show how zero trust works in certain situations. Testing in low-risk areas lets you see improvements in security and usability directly. The process of checking pilot results helps you improve strategies and solve problems. This method leads to better zero trust plans.
By focusing on these best practices, you can build a strong zero trust environment that boosts cybersecurity and lowers risks.
Challenges in Zero-Touch Deployment
Zero-touch deployment has many benefits, but it also comes with challenges. Knowing these challenges helps you deal with the difficulties of putting it into action.
User Needs and Compliance Risks
User needs can be very different for each role in your organization. If you do not meet these needs, you might create compliance problems and lower productivity. Here are some common challenges:
Legacy Systems or Apps: Older apps may not work with new deployment methods. This often means you have to set things up manually.
Deployment Errors and Reliability: Automated scripts can break, leaving devices set up wrong. Mistakes usually happen during rollout.
Change Management & Team Buy-In: Pushback from IT and users can slow down the use of new processes.
To reduce these risks, think about these strategies:
Start getting security and compliance needs in early.
Define a risk reduction plan early.
Automate reports for compliance problems to make sure rules are followed.
By focusing on user needs and compliance, you can improve the success of your zero-touch deployment projects.
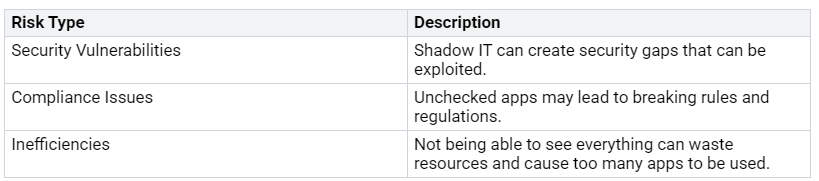
Addressing Shadow IT
Shadow IT brings big risks in zero-touch deployment settings. Employees might use apps that are not allowed, causing security problems and compliance issues. Here are some risks linked to shadow IT:
To deal with shadow IT, you should set up strong monitoring tools. This way, you can quickly react to suspicious actions. Also, teaching employees about the dangers of shadow IT can help build a culture of compliance and security awareness.
By facing these challenges, you can make sure your zero-touch deployment process runs smoothly while meeting user needs and keeping security and compliance in check.
Case Studies: Successful Implementations
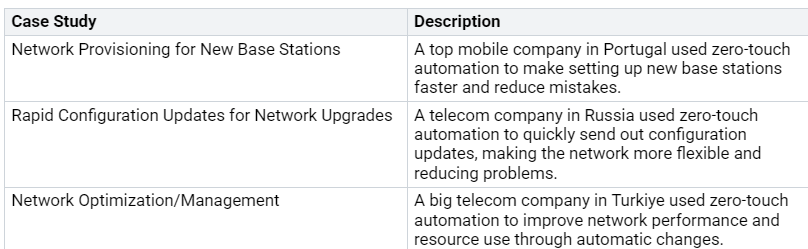
Industry Examples
Real-life examples of zero-touch deployment show how well this method works. Here are some important case studies:
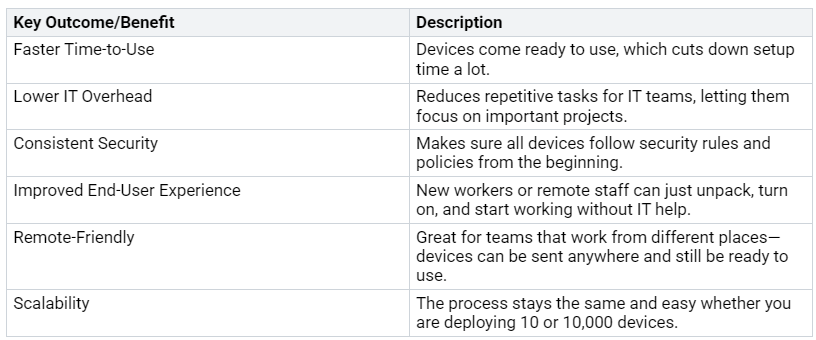
Outcomes and Benefits
The benefits of these projects are big. Here are some main results seen in different industries:
From these examples, you can learn important lessons. Good planning is very important. You need to know about old technologies and ISPs to make sure deployments go well. Using templates can save time and help find problems before deployment. Keep in mind that zero-touch provisioning is not completely zero-touch; it usually needs some interaction, so have realistic expectations. Better visibility through SD-WAN helps with troubleshooting and checking service performance. Finally, knowing the support model is key, as SD-WAN changes how management usually works.
By using these ideas, you can improve your own zero-touch deployment plans and get better results.
In conclusion, precision and segmentation are very important in zero-touch deployment. By changing deployment processes to fit user needs, you can boost productivity and security. Here are some main points to remember:
Network segmentation helps security by keeping important assets safe and managing network traffic well. This lowers the chance of big cyberattacks.
Microsegmentation uses detailed access controls. This stops unauthorized movement within a network, which makes security better.
The Zero Trust idea in microsegmentation makes sure that only needed access is given. This helps networks stay strong against lateral attacks.
By using these strategies, you can build a strong zero-touch deployment. This not only meets compliance rules but also helps your workforce do better.
FAQ
What is zero-touch deployment?
Zero-touch deployment sets up devices automatically. It lets you configure devices from far away without needing to do it by hand. This saves time and cuts down on mistakes during setup.
How does precision improve zero-touch deployment?
Precision makes deployment fit the needs of users. By using role-based policies and dynamic Azure AD groups, you make security better and ensure users get the right tools.
What is microsegmentation?
Microsegmentation breaks a network into smaller parts. Each part works as its own security area. This method stops unauthorized access and lowers the chance of attackers moving around.
Why is zero trust important in zero-touch deployment?
Zero trust makes sure only allowed users can access resources. It lowers security risks by checking user identity and device safety before giving access.
How can I address shadow IT in my organization?
To deal with shadow IT, use strong monitoring tools. Teach employees about the dangers of using unauthorized apps. Encourage them to stick to approved tools to keep security and compliance strong.