I once let my cousin borrow my car, only to realize I’d left the keys to my house on the keychain. Spoiler: Nothing bad happened, but it kept me up that night thinking, "Did I just give away too much trust by accident?" If you’ve ever been in charge of who-gets-access-to-what in your organization, you know that uneasy feeling. Today, let’s explore how Microsoft Entra roles act as that critical barrier (or, if you’re careless, as a wide-open front door), and why wrestling with the principle of least privilege can save you serious headaches.
1. Permission FOMO: Why Over-Access Starts with Good Intentions (and Ends in Trouble)
Let's be honest—nobody sets out to create security nightmares on purpose. Most over-permissioning starts with the best intentions. You know how it goes:
"Just give them admin access for now to save time."
"They might need these permissions later, so let's add them all."
"It's easier than having to go back and update later."
When Monday's Shortcut Becomes Tuesday's Disaster
Consider this all-too-common scenario: A junior admin gets assigned global administrator privileges because, well, it seemed easier than figuring out exactly what they needed. By Monday afternoon, they're productive! By Tuesday morning? They've accidentally deleted a critical application thinking it was a test instance.
"Imagine a junior admin is assigned a high level role such as global administrator without truly needing it."
This isn't a made-up horror story—it happens regularly in organizations of all sizes. Microsoft Entra roles exist precisely because these scenarios are real and disruptive.
Your Security is Swiss Cheese
Every unnecessary permission you grant is another hole in your organization's defense. It's like lending your house keys to the pizza delivery guy because he seemed trustworthy and you might need him to water your plants someday.
The risks break down into two major categories:
Operational Risk: Accidental deletions, misconfiguration of critical systems, or unintentional exposure of sensitive information. Oops doesn't quite cover it when 500 employees suddenly can't log in.
Security Risk: Every permission is an attack vector. When one account has excessive privileges, it becomes a golden ticket for attackers. Compromise that account, and they've hit the jackpot.
Good Intentions, Bad Outcomes
The road to security incidents is paved with convenience-based decisions. That quick fix to "just make them an admin" creates vulnerabilities that can haunt your organization for years.
What makes this particularly dangerous is how reasonable it seems in the moment. You're not being malicious—you're being helpful! You're removing roadblocks! You're enabling productivity!
Until you're explaining to the executive team why customer data is now publicly accessible.
Microsoft Entra roles were designed specifically to manage what users can do—they're core to securing your resources. Using them correctly isn't just a best practice; it's your organization's digital immune system.
2. Built-In Roles vs Custom Roles: The IKEA Furniture of Access Management
Ever bought IKEA furniture? Some pieces fit perfectly in your home, while others... not so much. Microsoft Entra roles work the same way.
The Off-the-Shelf Solution
Built-in roles are like that ready-to-assemble bookshelf – they work for most situations but weren't designed specifically for your weirdly-shaped living room with the slanted ceiling.
Microsoft offers several pre-packaged roles that handle common access needs:
User Administrator: Can manage accounts, reset passwords, and check service health
Global Administrator: The master key to your digital kingdom (use sparingly!)
Application Administrator: Manages your organization's apps without total control
These built-in options work great for standard needs. But what if standard isn't enough?
Custom-Built for Your Needs
This is where custom roles come in – they're the custom furniture you design when nothing in the store quite fits.
Want your IT tech to reset passwords but stay away from system configurations? Custom roles let you get that granular. Need someone to manage only specific resources? You can build that.
"Custom roles give your organization the flexibility to tailor permissions precisely to your needs."
The catch? Creating and managing custom roles requires Microsoft Entra ID Premium P1 or P2 licenses. Yes, there's a cost barrier. But the increased control often justifies the price, especially when implementing the principle of least privilege.
Finding the Right Balance
Most organizations benefit from a strategic blend:
Use built-in roles for simplicity and common scenarios
Deploy custom roles for critical workflows or unique situations
Think of it like furnishing your house – buy the standard bed frame and dresser, but maybe splurge on that custom home office setup where you spend 8+ hours daily.
The hybrid approach gives you the best of both worlds: the convenience of pre-built options with the flexibility to tailor permissions where it really matters. Like any good interior design, it's about finding the right pieces for the right spaces.
3. Role Categories—Or, Why Your Toolbox Should Have More Than Hammers
Ever opened your toolbox only to find nothing but hammers? Not very helpful when you need a screwdriver, right? Microsoft Entra roles work the same way—they're specialized tools for specific jobs.
The Three-Sided Toolbox
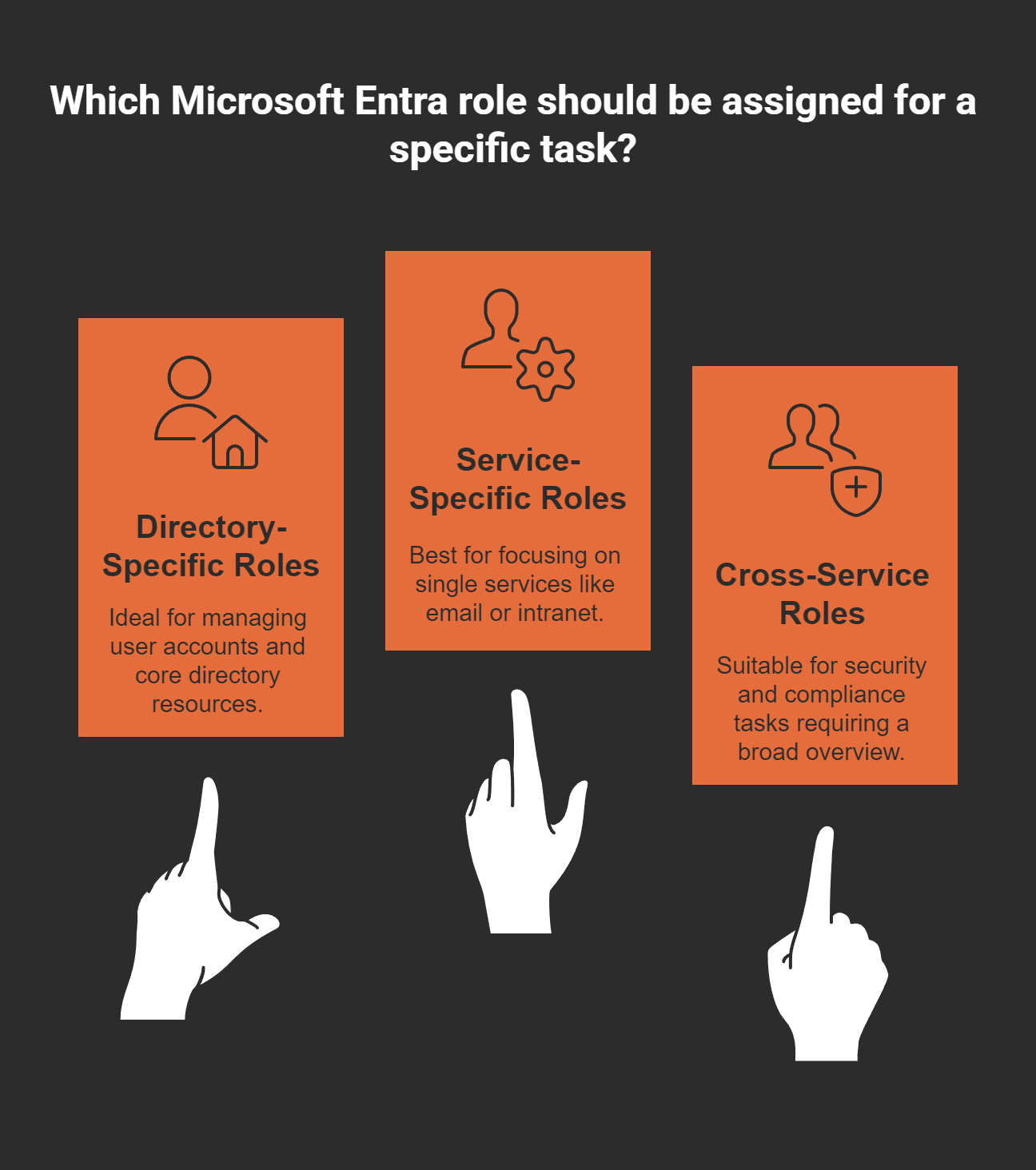
Not all Entra roles are created equal. They actually fall into three distinct categories, each serving a different purpose in your admin arsenal:
Directory-specific roles: These are for managing the "house" itself—user accounts, groups, and core directory resources. Think of the User Administrator who handles account management or the Groups Administrator who controls memberships.
Service-specific roles: Like having the perfect screwdriver for just one gadget. These roles focus on single services: Exchange Administrator for email, SharePoint Administrator for your intranet, Teams Administrator for collaboration, or Intune Administrator for mobile devices.
Cross-service roles: The Swiss Army knives of your admin toolbox. These span multiple services and are especially valuable for security and compliance folks who need a bird's-eye view of everything.
"If roles were tools in a toolbox, Microsoft Entra specific roles would be the screwdrivers essential for foundational tasks like building and maintaining structures."
Using the Wrong Tool = Disaster Waiting to Happen
Imagine giving someone a sledgehammer to hang a picture frame. That's what happens when you assign overpowered roles for simple tasks.
For example: Need someone to occasionally reset passwords? Giving them the Security Administrator role is massive overkill—like handing someone the keys to your entire house when they just need to water your plants.
The Plumbing Analogy
Think about it this way: assigning roles is like organizing your toolbox before fixing the sink. You need:
The right tool for the right job
Only the tools necessary for the task at hand
And please—don't give the plumber your car keys unless you want them driving off with your Porsche
The consequences of mismatched roles aren't just theoretical. When someone with a cross-service security role accidentally changes a setting they don't understand (because they only needed directory access), you're looking at potential downtime, security vulnerabilities, or compliance nightmares.
So before you start handing out admin roles like candy, ask yourself: what's the actual job that needs doing? Then pick the right tool from your carefully organized toolbox.
4. The Myth of Set-and-Forget: Why Role Assignments Need Regular "Spring Cleaning"
Let's bust a dangerous myth right now: role assignments aren't tattoos. You don't set them once and live with them forever. They need regular reviews and updates—especially when staff changes, promotions happen, or new projects kick off.
When Good Roles Go Bad
Ever heard about the help desk employee who accidentally became an accidental SharePoint demolition expert? Here's what happened:
Jake from IT support inherited his predecessor's account—complete with admin rights nobody remembered to revoke. While trying to help a user recover a file, he nearly wiped an entire SharePoint site. Not because he was malicious, but because he had permissions he never should have had in the first place.
"Changing a user's assigned role automatically updates their permissions."
That's great when you're setting things up... terrifying when you forget old permissions still exist.
Double-Layer Protection
Smart organizations pair role assignments with conditional access policies. Think of it as wearing both a belt and suspenders:
Give someone admin rights? Limit those rights to only work when they're on secure devices
Need to grant temporary project access? Set an expiration date
Have high-risk roles? Require multi-factor authentication every single time
The Stinky Fridge Theory
Old roles left unchecked are exactly like expired milk in the fridge—nobody notices until something stinks. By then, it's too late. The mess is made.
Even small organizations can be completely wrecked by a single wrong assignment. It only takes one over-permissioned account to cause disaster.
Your Security Maintenance Ritual
Make this your new mantra: Assign, review, repeat.
Set calendar reminders for:
Quarterly role reviews for all staff
Immediate access changes whenever someone's job changes
Project-end cleanups to remove temporary access
Remember, permission creep is real. Left unchecked, users accumulate access rights like digital packrats, creating security nightmares waiting to happen.
While automation helps (those automatic permission updates when roles change are excellent), nothing replaces human oversight. The most sophisticated systems still need your eyes on them regularly.
So grab your digital broom and dustpan. It's time for some permission spring cleaning—no matter what season it actually is.
5. When Least Privilege Feels Like a Tightrope Walk—Getting Practical
Let's be real: implementing least privilege isn't about becoming the office security paranoid. It's about finding that sweet spot between freedom and fences.
Ever watched a tightrope walker? That's you now, balancing security and productivity. One wobble too far either way and... well, you know.
The Million-Dollar Question
"RBAC is about answering a simple question, what does this person need to do their job?"
Not what they might need someday. Not what would be convenient. What they actually need to fulfill their responsibilities—and not one thing more.
Navigating the Role Landscape
Before you start assigning permissions, understand the territory:
Directory roles: Control identity resources like users and groups
Resource roles: Manage specific Microsoft Entra features and services
Mixing these up is like using your house key to start your car. Different locks, different keys.
The "Just in Case" Trap
We've all been tempted. "Let's make them a Global Admin just in case they need it later."
Nope. That's like handing out fireworks at a campfire—usually a bad call.
Consider your HR team. They might need to reset passwords and manage basic user profiles. The User Administrator role handles that perfectly. Giving them Global Admin access is just asking for trouble.
Permission Evolution
Roles aren't set in stone. As responsibilities change, so should access levels. Maybe someone needs temporary elevated access for a project? Grant it, then remove it when they're done.
Too often organizations set permissions once and forget them. Bad idea.
The Human Element
RBAC provides the framework, but your judgment fills the gaps. Sometimes the "by the book" approach needs a reality check.
Ask yourself:
What's the worst that could happen with this access level?
Is there a more limited role that would still let them do their job?
How easily could this access be misused or compromised?
Remember: too little access creates bottlenecks. Too much creates vulnerabilities. Finding that balance isn't just about following rules—it's about understanding your people and processes.
The tightrope walk gets easier with practice. And honestly? A careful walk beats a careless fall any day.
6. Wild Card: "What's the Worst That Could Happen?" – A 'Day in the Life' Disaster Scenario
Let me paint you a picture. It's Monday morning. Admin Bob is swamped with tickets and the new intern, Jane, needs access to help with account cleanup.
"Hey Jane, I'll just make you a global admin. It's easier than figuring out exact permissions right now," Bob says, clicking through the dialog boxes without a second thought.
Jane is eager to impress. Armed with her shiny new global admin rights, she begins her mission: clean up inactive accounts. She's careful, or so she thinks.
The Domino Effect Begins
Two hours later, the CEO calls IT in a panic. His email has vanished. All his contacts? Gone. That presentation for the board meeting tomorrow? Poof.
Jane looks horrified. She accidentally included the CEO's account in her cleanup script because it showed "inactive" (he was on vacation).
What happens next?
The CEO misses critical client communications
IT scrambles to restore from backups (if they exist)
The board presentation is delayed
Jane is mortified
Bob is in the hot seat
But wait—it gets worse.
Enter the Hacker
During all this chaos, Jane clicks a phishing email sent to her personal address. Because she's working from home on her personal device, her browser has saved her work credentials.
The hacker now has global admin access to your entire system.
"Suddenly, your organization is at serious risk of a security breach."
While everyone's distracted by the CEO's missing email, the hacker quietly creates backdoor accounts, downloads sensitive data, and plants malware throughout the system.
One small misstep = total chaos.
The Ounce of Prevention
Sure, this scenario sounds dramatic. But ask any IT security professional—they've seen similar disasters unfold.
Those "excessive" best practices around role management? They exist because someone, somewhere lived through this nightmare.
When setting up Entra roles, don't just ask "What does this person need to do their job?" Ask "What's the absolute worst that could happen if this account was compromised or misused?"
Consider this: Would you rather spend time configuring proper permissions now, or explaining to your board why customer data is being sold on the dark web?
Trust is nice. Verification is better. But proper role configuration from the start? That's priceless.
7. Not-So-Obvious Tips for Nailing Entra Role Assignments (Even When You're Rushed)
Let's face it—you're busy. Really busy. And when you're juggling multiple priorities, role management often becomes that thing you "just need to get done." But hasty role assignments are exactly when security gaps happen.
I made this mistake last month. Rushing to meet a deadline, I gave a contractor way too much access because I couldn't remember exactly which permissions they needed. Big facepalm moment during our security review.
Your Secret Weapons for Better Role Management
Create a role assignment checklist - Don't trust your memory when you're in a hurry. A simple document with role review steps and licensing requirements saves you from those "I thought I remembered" moments.
Balance broad roles with hard limits - If you must assign a powerful role, pair it with conditional access policies. Restrict by location, device compliance, or time of day to reduce risk exposure.
Document your "why" - Ever look at a role assignment six months later and think "who approved this and why?!" Future you (or your auditor) will thank present you for noting "Marketing Director needs this access for campaign analytics during Q2 launch."
Rotate your reviewers - We get blind to our own permission structures. Having different admins review role assignments catches those "we've always done it this way" problems.
Embrace "just enough" access - That voice saying "let me add this permission just in case" is your enemy. When rushed, we default to over-permissioning out of misplaced helpfulness.
Get an outside opinion - Someone not emotionally invested in the project can spot unnecessary access rights that you might overlook because you're focused on making things work.
The Hidden Cost of Rushing
Remember: without a structured approach like properly implemented RBAC, we default to manual assignments that create inconsistencies and security gaps. As the transcript notes: "Without a structured framework like RBAC, access is often assigned manually, creating inconsistencies and gaps that can go unnoticed."
Ever notice how permission problems always seem to surface during critical projects or right before vacations? That's no coincidence—it's the direct result of rushed role management.
The principle of least privilege isn't just security jargon—it's your best defense against the chaos that comes from hurried access decisions.
What role assignment mistakes have you caught just in time? We've all been there!
Conclusion: Access Control as an Act of Care (Not Just Compliance)
We've reached the end of our journey through Microsoft Entra role management, and I want to leave you with something more meaningful than a technical summary. What we've been discussing isn't just IT administration—it's an act of care.
Setting roles isn't just ticking boxes on a compliance checklist. It's leadership in action. When you carefully assign permissions based on what people truly need rather than what's convenient, you're demonstrating what good stewardship looks like.
The Invisible Heroes
Think about it: the 'least privilege' mindset protects both people and organizations. It's like digital hospitality with sensible locks—you welcome guests properly while ensuring they can't accidentally wander into areas that might harm them or others.
The most successful access administrators I know aren't celebrated with awards. Their greatest compliment? "Nobody noticed anything went wrong—because it never did." Your vigilance creates that invisible safety net everyone relies on but rarely sees.
Small Actions, Big Impact
Those small, thoughtful pauses before clicking "grant all permissions"? They matter more than you think. That extra moment to consider whether someone really needs global admin rights or if a more targeted role would suffice—these make an outsized impact over time.
I've seen organizations transform their security posture not through massive overhauls but through these seemingly minor decisions made consistently day after day.
Beyond the Framework
While frameworks give us structure, remember that experience and context matter just as much. Revisit and refine your approach as you learn. Sometimes perfect on paper doesn't translate to perfect in practice.
Your judgment—informed by understanding your organization's unique needs—is what turns good practices into great protection.
A Final Thought
You're not just a gatekeeper; you're a caretaker. The work you do managing Microsoft Entra roles might seem routine or even tedious at times, but it's heroic work... even if invisible.
When you approach access control as an act of care rather than just compliance, something shifts. You begin to see how these technical decisions reflect your values—how you protect not just systems but people.
So take pride in this work. Your thoughtful role management isn't just securing a directory—it's creating space where people can do their best work without fear or unnecessary friction.
That's something worth doing well.