Imagine a smart doorman. He guards your company’s digital doors. This doorman checks your ID. He also looks at your location. He sees what device you use. He even checks your usual behavior. This helps explain Conditional Access. It protects company data. It also protects resources. Criminals use stolen credentials. This happens in many cyberattacks. You want to avoid data breaches. They cost a lot of money. Conditional Access makes security smarter. It is not harder for your team.
Key Takeaways
Conditional Access is like a smart digital doorman. It checks many things. This happens before you enter company systems.
This system uses ‘if-then’ rules. It decides if you can get in. This is based on who you are. It also checks your device. It looks at where you are.
Conditional Access makes security stronger. It often uses multi-factor authentication (MFA). This adds extra protection.
It keeps company data safe. It also helps your company. It follows important rules and laws.
This system makes work easier. It also makes it safer. Employees can work from anywhere. There are no constant security interruptions.
What is Conditional Access
Think of Conditional Access as a digital bouncer. This bouncer does not just check your ID. It looks at many things. It checks before letting you in. This smart system checks rules. It decides if you can get in. You can access your company’s digital things. This explains Conditional Access simply. It makes sure only right people get in. They get in under right conditions.
Beyond Passwords
You might think passwords are enough. But strong passwords have problems. People forget them. They can get stolen. Attackers can guess them. This raises risk of security problems. Only using passwords leaves you open. Attackers can easily crack them. They can steal login info. They can get in without permission. Once in, they can move around. They can even get more power. Old security often struggles. This is with insider threats. Employees with access misuse it. Conditional Access goes beyond passwords. It adds more protection.
The “If-Then” Logic
Conditional Access policies work like “if-then” rules. Imagine this: If a user tries to use an app, then something must happen. For example, if you are in Finance. You try to use the Payroll app. The system might ask for more proof. It might need a safe device. If you are not in Finance. You try to use Payroll. The system will stop you.
Conditional Access policies check many things. They make smart choices. These things include:
User risk: Is your account possibly taken over? The system checks this.
Sign-in risk: Is this login attempt strange? It looks at your location. It checks how you usually log in.
Insider risk: Is an employee acting strangely? This uses info from security tools.
Device platforms: What device are you using? Is it an iPhone, Android, or Windows?
Client apps: Are you using a web browser? Is it a mobile app? Or an old email program?
This way of doing things looks at many facts. It looks at your job. It checks your device’s health. It checks how you log in. It figures out a risk score fast. If risk is high, it might ask for more proof. This is how Conditional Access decides access.
Enhancing Security with Multifactor Authentication
One of the best tools is multifactor authentication (MFA). This means you need more than a password. You need more to prove who you are. You might type your password. Then you get a code on your phone. This is also called two-factor authentication. It adds a lot of security.
Think about what MFA does. Over 99.9% of accounts were hacked. They did not have MFA on. This shows how strong it is. Using multi-factor authentication can cut cyberattack risk. It can cut it by up to 99.9%. This is a big deal. It stops people from getting in without permission. Even with MFA, some smart attacks still happen. But MFA makes it much harder for bad guys. You can turn on MFA. Do this through your Conditional Access policies. This makes your security much stronger.
Why Conditional Access Matters
Keep your company’s data safe. This includes customer lists. It includes financial reports. It includes new product designs. Conditional Access helps you do this. It is like a digital vault. It lets only the right people in.
Protecting Company Data
Conditional Access can:
Stop bad users from getting in. It uses your rules.
Block sensitive files. It stops them from being moved.
Add extra security. This is for designs or plans. It can limit access. This is for your network or managers.
Reducing Security Risks
You face many digital threats. Conditional Access helps you fight them. It makes security stronger. It lowers breach chances.
Conditional Access helps avoid big risks:
Bad access: People get into systems. They do not have permission.
Possible breaches: Data gets stolen. Or it is exposed.
Not following rules and laws.
Unmanaged threats: New ways attackers get in.
Conditional Access policies change. They adapt to new risks. They are not like old security. They can force MFA. This is for new devices. Or for risky places. They can stop access. This is from devices that do not meet rules. You can set specific rules. These rules are for groups. They are for apps. They are for access types. This gives “least-privilege” access. It makes security better. It does not slow down work. It works with threat tools. For example, it links with Azure Active Directory Identity Protection. It looks for strange logins. It changes access rights fast. This stops problems.
Conditional Access policies also cut down attacks. They block old login methods. These methods, like IMAP and POP, are used in password attacks. You can also make strong password rules. You can make people use complex passwords. You can make them unique. You can ask them to update passwords often. Strong passwords with MFA add strong security. This protects against stolen login details.
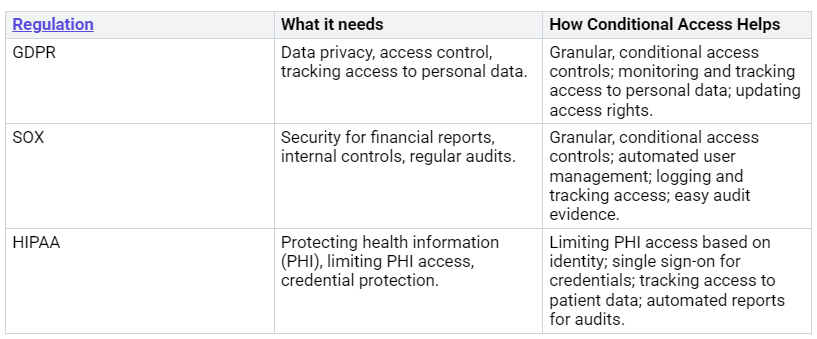
Meeting Compliance Needs
You know rules are important. Laws like GDPR, HIPAA, and SOX need strong data protection. Conditional Access helps you meet these rules.
Conditional Access policies help your company follow rules. They make sure access controls are steady. They create records you can check. They support strong login methods.
Benefits for Operations
Boosting Productivity
You want your team to work well. Conditional access helps them do just that. It makes security smart, not annoying. This system checks things in the background. It makes sure you are safe. You do not get constant pop-ups or extra steps when you do not need them. For example, if you are on your work computer in the office, you might not need extra verification. But if you try to get into sensitive files from a new device at a coffee shop, the system will ask for more proof, like an mfa code. This balance means you can work without constant interruptions. You stay focused on your tasks. This smooth process helps your whole team get more done. It gives you strong protection without slowing you down.
Flexible Access Control
Managing who can access what can be a big job for IT. Conditional access makes this much easier. It automates decisions about who gets in. Your IT team sets the rules once. Then, the system handles access automatically. This means IT does not have to manually check every single login. They do not have to manage permissions for each person or device. This automation frees up your IT staff. They can focus on bigger, more important tasks. It also means fewer mistakes. Automated processes are more accurate than manual ones. This helps your whole organization run more smoothly and efficiently. It reduces the daily workload on your IT team.
Adapting to Modern Work
Today, many people work from anywhere. They use different devices. Conditional access is perfect for this modern way of working. It helps keep your data safe, no matter where your team is. It checks who you are, often with mfa. It also checks if your device is secure. It can even make sure you are on an approved network. This system uses a “Zero Trust” idea. It means it does not trust anyone or anything by default. You must prove you are allowed in every time. This adds a strong layer of security. For example, you can let someone check email on their personal phone. But you can block them from seeing sensitive company documents on that same phone. This gives you great control over your cloud apps, like Microsoft 365.
Employee Impact
You may ask how security affects your work. Conditional access makes things safe. It also makes things easy. It helps you know why you have extra security steps. It makes your organization more secure.
A Secure User Experience
You want to finish your work. You do not want stops. This system helps you do that. It makes security strong. It also makes it easy to use. It does not always ask for more steps. For example, you log in from your work computer. It is in the office. You will not see extra steps. The system knows this is safe. It lets you get to things easily.
But, you try to log in from a new device. It is in a new place. The system might ask for more proof. It might need mfa. This is because it sees danger. Tools like Entra ID Identity Protection use smart learning. They look for strange login times. They look for unknown devices. This lets it change how it acts. It makes security better. It does not always stop real users. This smart way makes rules tighter. It does this only when danger is high. It makes rules looser when danger is low. This keeps you working.
Understanding Access Challenges
Sometimes, the system will stop you. It asks for more facts. Or it blocks you. You might ask why. This happens when the system sees something odd. Or it sees something risky. For example, you try to log in from a new country. You have never been there. It might ask for mfa. It could even stop the login.
Your device’s health is also key. Your device is not managed by the company. Access might be stopped. This also happens if you use an old authentication method. The system checks who you are. It checks where you are. It checks your device. It also checks the app you want to use. It even looks at real-time danger signs. These signs might show impossible travel. Or they show stolen login details. This helps keep company data safe.
Supporting Security Culture
This smart security system helps everyone. It helps your organization think about security. It makes security a team job. You can make security tasks fun. Imagine getting points. Or getting badges. This is for doing security tasks. This makes following rules feel like a game.
You can also have fun training. Teams can pretend to get sensitive data. They do this from different places. This helps everyone learn security rules. It makes security a fun group task. This helps make a stronger security culture.
Think of conditional access as a smart choice. It helps your company’s future. It is more than a security tool. It strongly protects your company’s data. This data is very important. It also helps your employees. They get a safe experience. It is also flexible. They can work anywhere. They can work how they want. This smart tech helps your business grow. It makes your company strong. This is for our fast digital world. You can be sure about future problems.
FAQ
What is Conditional Access in simple terms?
We explain conditional access as a smart security guard. It checks many things before you get into company resources. It looks at who you are. It checks your device. It sees where you are. Then it decides if you can enter.
Will Conditional Access make my work harder?
No, it makes security smarter. You will only see extra steps when needed. For example, if you log in from a new place. This keeps you safe without constant interruptions.
How does Conditional Access protect our data?
It stops unauthorized access. It checks your identity and device health. It also checks your location. If something looks risky, it asks for more proof. Or it blocks access. This keeps sensitive company data safe.
Can Conditional Access help with remote work?
Yes, it is great for remote work. It lets you work from anywhere. It keeps your data safe. It checks your device and location. This ensures secure access to company resources.